Windows systems are critical infrastructure for both businesses and individuals. That's why when a remotely exploitable vulnerability appears, it deserves attention. One such flaw, tracked as CVE-2023-32014, highlights a major weakness in the Windows implementation of Pragmatic General Multicast (PGM). In this long read, you'll get an easy-to-grasp explanation, see related code snippets, and learn why this bug matters.
What is PGM?
PGM (Pragmatic General Multicast) is a network transport protocol developed by Microsoft. It's mainly used for scalable, reliable multicast delivery and is popular in Windows environments where applications—think media streaming or financial services—need to send data to many receivers at once.
The Windows implementation of PGM is handled by the mswsock.dll and underlying kernel modules. Unfortunately, as CVE-2023-32014 demonstrates, complex code around network protocols often leads to serious vulnerabilities.
About CVE-2023-32014
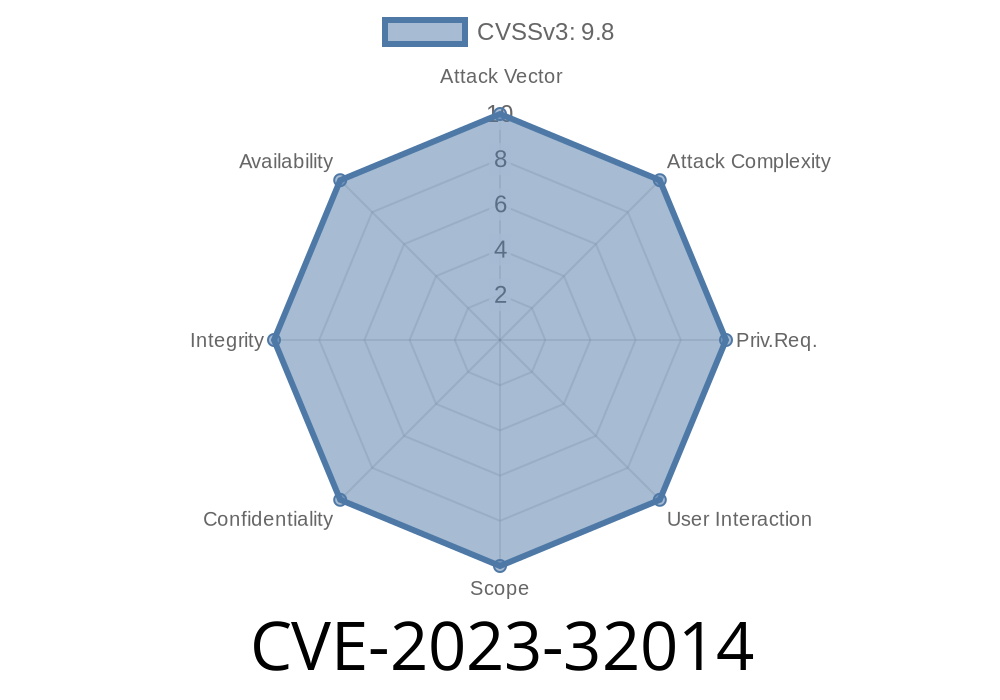
CVE-2023-32014 is a Remote Code Execution (RCE) flaw in Microsoft's implementation of PGM. It can allow a remote attacker to run code of their choice on vulnerable Windows systems—no authentication needed.
The official Microsoft advisory is here.
Affected Windows versions:
Windows Server 2016 and later
What makes this vulnerability dangerous is that PGM is enabled by default in some situations and can be triggered remotely with carefully crafted network packets.
Technical Details
The root cause lies in how Windows PGM handles network traffic, specifically the processing of malformed or maliciously crafted PGM packets. Attackers can send a specially-crafted sequence of packets over the network, causing a buffer overflow or use-after-free in the Windows PGM stack.
Here's a pseudo-snippet showing where things go wrong (simplified for clarity)
// Vulnerable function handling incoming PGM packet
void HandlePGMPacket(PGM_PACKET *pkt) {
// ...parse headers...
int dataLen = pkt->data_length;
char buffer[1024];
// !! No proper size validation !!
memcpy(buffer, pkt->data, dataLen);
// ...process buffer...
}
In real exploitation scenarios, the attacker sends a malformed packet where dataLen exceeds the size of buffer, leading to memory corruption and potential code execution.
## Proof-of-Concept / Exploit Overview
Disclaimer: This information is for educational purposes. Do not attempt to exploit systems you do not own.
Steps an Attacker Might Use
1. Identify an Exposed Target: The attacker scans the network for open PGM service endpoints (TCP/PGM port 113, for example).
2. Send Malicious Packet: By crafting a packet with a specifically malformed PGM header/data segment, they trigger the flaw.
3. Achieve Code Execution: The overflow allows the attacker to hijack control flow, executing shellcode or another payload remotely on the server.
Example Python Skeleton (non-working, illustrative)
import socket
# Connect to PGM port (often requires special privileges)
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.connect(('victim_ip', 113))
# Build malicious packet with an oversized data length field
malicious_packet = b'\x00\x01...' + b'A' * 200 # Overflows buffer
sock.send(malicious_packet)
sock.close()
*The actual exploit would need precise crafting and target-specific payloads.*
Security Impact
- Remote Code Execution: Attackers can run any code in the context of the affected process, which can mean full system compromise if exploited as SYSTEM.
Wormable Potential: If PGM is widely used internally, a worm could propagate between machines.
- No User Interaction Needed: Just exposing PGM services or having them available is enough for exploitation.
Mitigation
- Patch Immediately: Microsoft released fixes in June 2023. See the official advisory and apply updates:
Microsoft Patch
- Disable PGM if Not Needed: Remove or block PGM (protocol number 113) on the firewall if your apps don't use it.
References and Further Reading
- Microsoft Security Advisory for CVE-2023-32014
- NVD CVE Entry 2023-32014
- Wikipedia: Pragmatic General Multicast
- Detailed Analysis (Zero Day Initiative Blog)
Conclusion
CVE-2023-32014 is a classic but dangerous example of what can go wrong in complex protocol handling inside the Windows OS. If you run Windows servers or applications that leverage multicast or PGM, update *now*. Even if not, it’s a good reminder of why disabling unused network protocols and keeping up with patches is so important.
Timeline
Published on: 06/14/2023 00:15:00 UTC
Last modified on: 06/14/2023 03:37:00 UTC