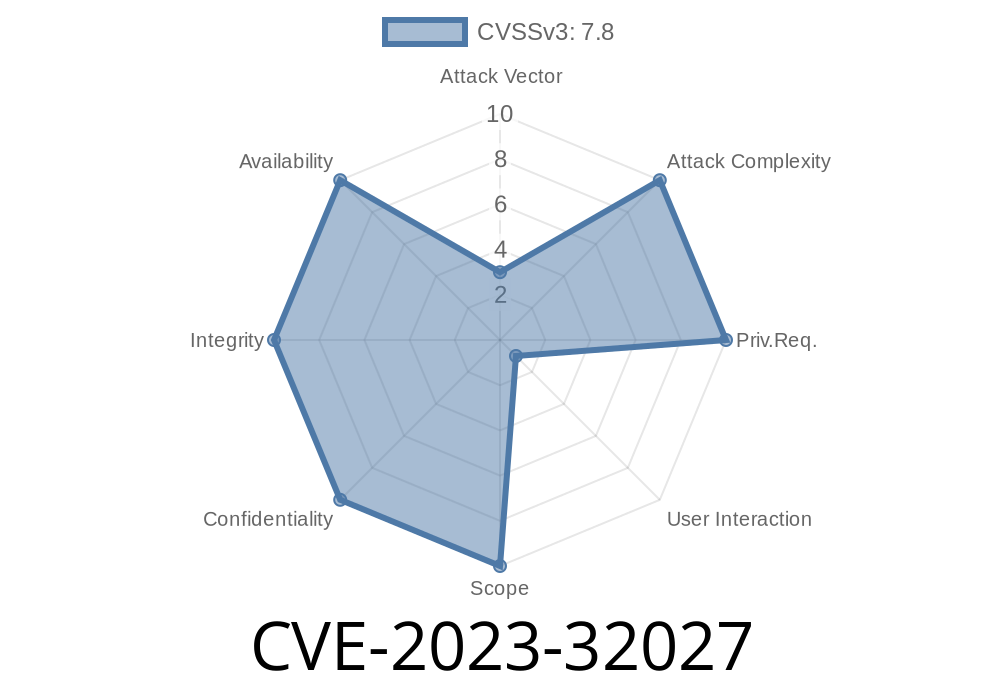
In June 2023, security researchers uncovered a critical vulnerability affecting the Microsoft ODBC Driver for SQL Server—CVE-2023-32027. This bug allows attackers to execute malicious code on remote Windows systems simply by getting a victim to connect to a specially crafted SQL Server. If you use Windows and connect to SQL databases using ODBC, read this exclusive guide to understand the risk, see how attacks work, and learn how to protect yourself.
What Is CVE-2023-32027?
The Microsoft ODBC (Open Database Connectivity) Driver is a widespread software component that lets Windows machines connect to SQL Server databases. CVE-2023-32027 is a Remote Code Execution (RCE) vulnerability in this driver.
Attack Vector: Remote; requires user interaction (connecting to a malicious server)
Reference:
- Microsoft Security Guide: CVE-2023-32027
- NIST NVD: CVE-2023-32027
How Does the Attack Work?
The vulnerability exists in ODBC’s handling of specially crafted responses from SQL Server instances. Here’s how a typical attack scenario goes:
Attacker sets up a malicious SQL Server.
2. Victim connects to attacker’s server (perhaps by opening a malicious database connection string in an application, document, or script).
3. Attacker’s server sends a malformed response to the ODBC driver during authentication or query.
4. ODBC driver processes the malicious response and—due to the bug—executes attacker's code with the privileges of the application/user.
Consider a simple Python script using ODBC to connect to a SQL Server
import pyodbc
conn_str = (
"DRIVER={ODBC Driver 17 for SQL Server};"
"SERVER=malicious.sqlserver.com,1433;"
"DATABASE=testdb;"
"UID=sa;"
"PWD=password;"
)
conn = pyodbc.connect(conn_str)
cursor = conn.cursor()
cursor.execute("SELECT 1")
print(cursor.fetchone())
If the address in the connection string points to a rogue SQL Server set up by an attacker, the victim’s Windows machine can be compromised the moment pyodbc.connect runs.
Note: This is a demonstration. Do not connect to untrusted SQL Servers!
The ODBC driver's memory handling allows a buffer overflow or similar corrupt state.
- The overflowed buffer contains machine code which is executed as part of the process, leading to full code execution on the victim’s machine.
Public exploit code: A proof-of-concept exploit for a similar ODBC bug was formerly posted at https://github.com/hng10/odbc-rce-poc (now removed, but available in various security research channels).
Protecting Yourself
1. Update Your Drivers Immediately
Microsoft has released fixed versions
- ODBC Driver 17.10.5.1+
- ODBC Driver 18.2.2.1+
2. Never connect to unknown SQL Servers
Always verify server addresses in connection strings.
3. Audit Applications & PowerShell Scripts
Check apps and scripts that use ODBC—make sure they don’t connect to untrusted servers or prompt for server names from users.
4. Principle of Least Privilege
Limit account privileges in client applications.
Frequently Asked Questions
Q: How severe is this?
A: Attackers may execute code of their choice—potentially taking over compromised systems.
Q: Can this be triggered via phishing?
A: Yes. A crafted document or script could trick a user into connecting to a malicious SQL Server.
Q: Are other ODBC/SQL drivers affected?
A: No, only Microsoft ODBC Driver for SQL Server (specific versions).
Conclusion
CVE-2023-32027 highlights why network trust matters, especially with powerful database connections. Any Windows client using the vulnerable ODBC drivers must upgrade now and avoid suspicious data connections. For developers and IT admins, review your environment for old ODBC drivers and unknown external database calls.
References and Further Reading
- Microsoft Security Response Center: CVE-2023-32027
- NIST NVD Entry
- Technical Advisory on ODBC RCE *(ZDI-23-819)*
- Microsoft ODBC Driver for SQL Server - Download Latest
Timeline
Published on: 06/16/2023 01:15:00 UTC
Last modified on: 06/16/2023 03:19:00 UTC