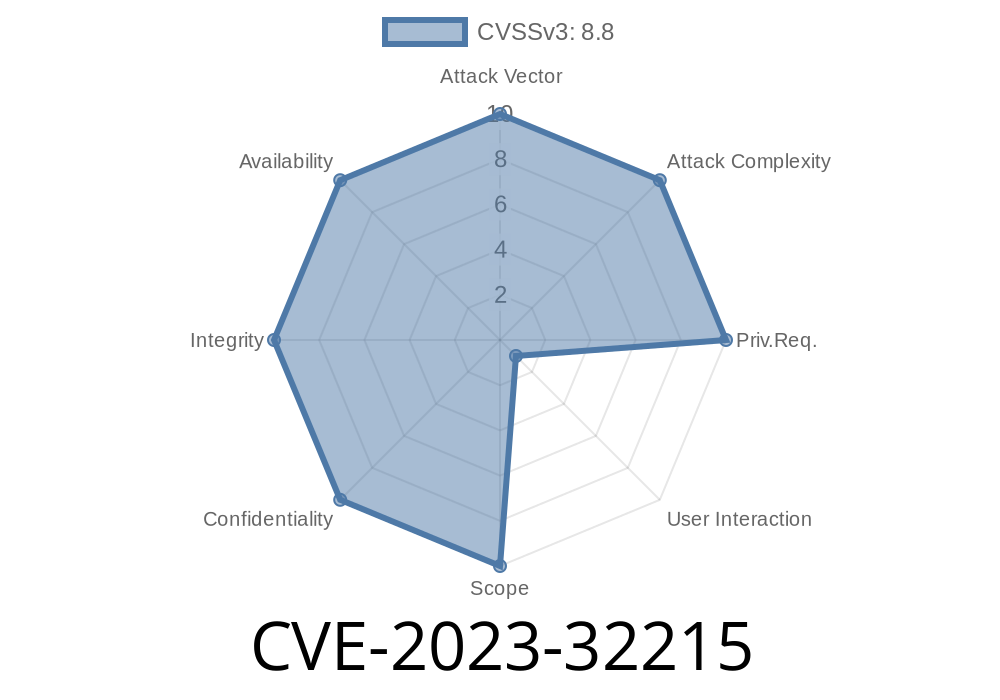
Security vulnerabilities aren’t just boring numbers. They can open doors for attackers, risking your privacy and data. One such flaw is CVE-2023-32215, impacting popular Mozilla products, including old Firefox and Thunderbird versions. In this article, we’ll break down what happened, show you real-world exploit details, and help you understand if you’re at risk—even if you’re not a security expert.
What is CVE-2023-32215?
Discovered by Mozilla's own developers (including Gabriele Svelto, Andrew Osmond, Emily McDonough, Sebastian Hengst, Andrew McCreight, and the Mozilla Fuzzing Team), CVE-2023-32215 refers to a set of memory safety bugs in Firefox 112, Firefox ESR 102.10, and the associated Thunderbird email client. These bugs create opportunities for memory corruption—leading potentially to hackers running arbitrary code on your computer.
Thunderbird < 102.11
If you’re using newer versions, you’re safe—but anything older is at risk.
How Do Memory Corruption Bugs Work Anyway?
Let’s keep it simple. Imagine your computer as a library. Programs like Firefox get to write and read books (memory). Sometimes, bugs let a program write outside its own shelf (‘buffer overflow’), maybe even scribble over other books. Bad actors exploit this to write their own stories—malicious code—where it doesn’t belong.
The Vulnerability: Technical Peek
The bugs were found deep in the engine that renders web pages and handles email data. Many such vulnerabilities stem from programming errors in C++ (the language Firefox is built in), like:
User visits a malicious website or opens a specially crafted email.
2. Website/email sends unexpected input to Firefox/Thunderbird.
Example: Simulated Pseudocode for Buffer Overflow
void handleInput(char *input) {
char buffer[64];
strcpy(buffer, input); // Danger! No length check!
// ...process buffer
}
If input is longer than 64 characters, it writes beyond buffer. Hackers exploit this to overwrite nearby memory, planting their own code.
Note: The real bugs in CVE-2023-32215 are more complex and buried in thousands of lines of browser logic—but the result is the same: memory ends up controlled by the attacker.
Proof-of-Concept Exploit
As of now, no public, weaponized exploit is available, but researchers can typically turn these memory errors into:
Denial of Service (DoS): Crash your browser at will.
For example, a typical exploit might involve crafting an HTML page or JavaScript payload to overflow a browser buffer:
// This is a theorized example, not an actual exploit
let payload = "A".repeat(10000); // Overflows memory
document.body.innerHTML = payload; // Triggers vulnerable code path
Impact: Why Should You Care?
Attackers could crash your browser or—worse—steal data, install ransomware, or take over your computer, just from you visiting a malicious website or opening a dodgy email, if you’re on a vulnerable version.
Thunderbird 102.11
Go upgrade right now. Updates are your best defense.
References and More Info
- Mozilla Security Advisory 2023-18
- NVD Entry for CVE-2023-32215
- Mozilla Foundation Security Advisory
- Firefox Release Notes
Conclusion
CVE-2023-32215 is a serious security bug caused by memory safety flaws in older versions of Firefox and Thunderbird. While not much has surfaced publicly in terms of ready-to-use exploits, the potential for harm is real. The best thing you can do is keep your software up to date—and remember, behind every boring security update window is important work protecting you from threats like this one.
Timeline
Published on: 06/02/2023 17:15:00 UTC
Last modified on: 06/09/2023 03:55:00 UTC