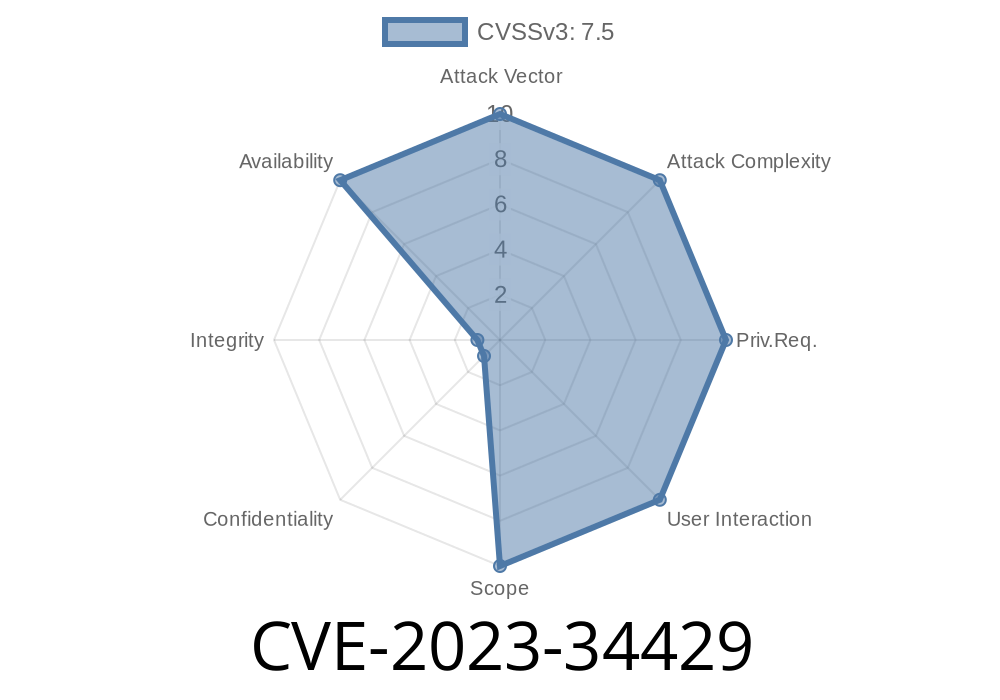
Weintek Weincloud is a popular cloud service for connecting and monitoring Human-Machine Interfaces (HMI) in industrial setups. In May 2023, a significant vulnerability, CVE-2023-34429, was discovered in version .13.6 of Weincloud. This flaw allows anyone to send a malicious authentication token and potentially crash the entire cloud system—effectively triggering a Denial of Service (DoS).
In this post, we’ll break down the details of CVE-2023-34429, look at example code, show how an attack could happen, and share official links for further reading. Our aim is to help engineers and security professionals understand this weakness before attackers can exploit it in the real world.
What Is CVE-2023-34429?
CVE-2023-34429 is a vulnerability found in Weintek Weincloud version .13.6. The issue is in the way this version processes JSON Web Tokens (JWTs) during the authentication phase.
Normally, Weincloud uses JWTs for secure login, making sure only authorized users can access cloud features. However, if a JWT is forged (i.e., created in an invalid or malicious way), Weincloud does not handle it properly. Instead, it can crash—and possibly all connected services go down—opening the door for any external attacker to launch a denial-of-service attack.
Official CVE link:
- NVD - CVE-2023-34429
Official vendor advisory (Weintek):
- Weintek Security Bulletins
Let’s say you’re an attacker who wants to take Weincloud offline. Here’s what you might do
1. Create a Fake JWT: Generate a JWT with invalid headers, malformed payload, or a tampered signature.
2. Send the Malicious JWT: Submit this JWT to the Weincloud server—through the login API or any endpoint that accepts JWTs.
3. Cause the Crash: The backend tries to process this toxic token. Due to badly written error-handling code, the application process may crash, which can make the service unavailable for everyone.
Important: No user account or password is needed; public endpoints are enough.
Example Exploit Code
Let’s walk through a basic Python example. *This is for educational and defensive purposes only!* Never test this on live or public systems you do not own.
import requests
# Endpoint URL - change to your Weincloud instance
url = "https://your-weincloud-instance/api/v1/login";
# A forged JWT: Header, Payload, and Signature do NOT match any real format.
fake_jwt = "abc.def.ghi"
headers = {
"Authorization": f"Bearer {fake_jwt}"
}
response = requests.get(url, headers=headers)
print("Status code:", response.status_code)
print("Response:", response.text)
What’s happening here?
The script sends a GET request with an obviously bogus JWT (abc.def.ghi). A properly secure system would reject it and return a 401 Unauthorized. But on vulnerable .13.6 installs, parsing this token internally could crash the service entirely, leaving Weincloud offline for all users.
How Can You Test Your Own Instance?
If you’re responsible for a Weincloud deployment, you can run the snippet above (pointing it to your test/development server!) and monitor logs or service status. If the service crashes or becomes unresponsive, you’re affected.
To protect production environments, update Weincloud to the latest recommended version from Weintek as soon as possible. Vendors may have issued hotfixes or patches—always check their security advisory.
Why Did This Happen?
From a technical side, the problem is because Weincloud .13.6 does not sanitize or check JWT input properly. Instead of using try/except blocks or input validation, it assumes all JWTs received will be well-formed and signed by a trusted source. When that’s not true, the code fails unpredictably—opening an easy path for denial-of-service.
Upgrade Weincloud to latest version.
- Add input validation for JWTs. An invalid token should always get a controlled error, never a crash.
References and Resources
- CVE-2023-34429 on NIST NVD
- Weintek Security Bulletin for Weincloud
- OWASP JWT Cheat Sheet
- JWT.io Introduction
Final Thoughts
While JWT authentication is powerful, it must be done carefully. As this vulnerability shows, any gap in how tokens are verified or parsed can put your cloud services—and business—at risk. Always keep your systems patched, validate all inputs, and keep up to date with vendor advisories!
Timeline
Published on: 07/19/2023 22:15:00 UTC
Last modified on: 07/26/2023 16:17:00 UTC