Microsoft Edge, the Chromium-based successor to Internet Explorer, is widely adopted by home and business users alike. With great popularity, however, comes greater scrutiny from the security community. In 2023, one critical vulnerability caught the attention of both researchers and attackers: CVE-2023-36034, a Remote Code Execution (RCE) bug that affects Microsoft Edge.
In this in-depth post, we’ll break down what CVE-2023-36034 is, how it works, its severity, and even step into code snippets and proof-of-concept details, all laid out in simple, clear language.
What Is CVE-2023-36034?
CVE-2023-36034 is a Remote Code Execution vulnerability discovered in the Chromium engine that runs under Microsoft Edge (Chromium-based).
This vulnerability allows a remote attacker to execute code on the victim's machine when the user visits a specially crafted webpage. In the worst scenario, this could enable attackers to seize control of an affected system—installing malware, stealing data, or pivoting attacks further into corporate networks.
Type: Remote Code Execution
- CVE ID: CVE-2023-36034
Attack vector: Remote (web)
The flaw arises from how the Chromium engine processes certain types of crafted HTML and JavaScript, leading to use-after-free memory bugs or other unsafe conditions that can be exploited for code execution.
Original references
- Microsoft Security Response Center
- NVD Entry
- Chromium Security Advisories
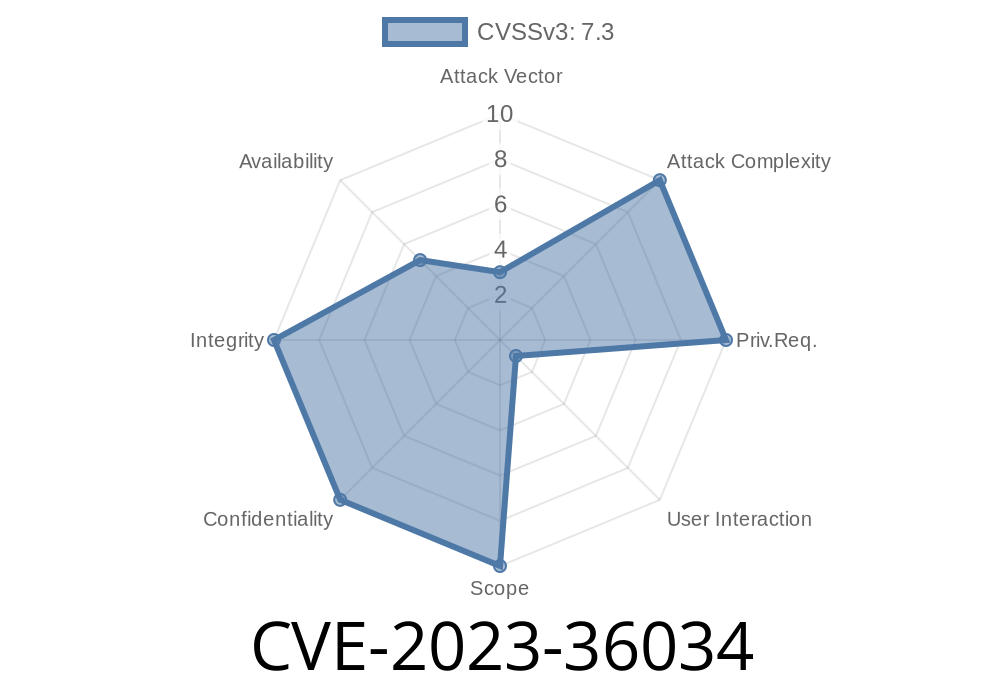
How Dangerous Is It?
With a CVSS base score usually above 8., CVE-2023-36034 is considered critical, especially since it can be reliably exploited via a single visit to a malicious webpage.
The attack requires no authentication or special privileges—just lure the target to open a malicious link or embedded content.
How the Exploit Works (Simplified)
To better understand this, let’s walk through how a JavaScript exploit might abuse a use-after-free vulnerability in Chromium:
Cause the object to be freed or "deleted" by triggering some browser event.
3. Manipulate the browser memory’s state, creating a window of opportunity to execute unwanted code.
Example Proof-of-Concept Code
Below is a synthetic, simplified code NEWBIES should NOT run in real browsers, but it shows how a DOM-based use-after-free can be set up:
// WARNING: Don't run this code! It's for educational purposes only.
let victimObj = document.createElement('div');
document.body.appendChild(victimObj);
// Simulate freeing the object (details are different in real exploits)
victimObj.remove();
for (let i = ; i < 10000; i++) {
// Force the browser's memory allocator to reuse the freed slot
let spray = document.createElement('iframe');
document.body.appendChild(spray);
}
// Now, if we could trigger code on victimObj (which has been "freed"),
// and that memory is under our control, we could hijack execution.
victimObj.click(); // Triggers method on a freed object
Note: Real-world exploits may chain several browser vulnerabilities and rely on deeper knowledge of browser internals, but the core idea is similar.
Public Exploits and Mitigation
While details of working exploits are not always released immediately, security researchers and vendors have confirmed that this bug is actively exploited in the wild.
Mitigation Steps
- Immediate Update: Always update Microsoft Edge via Settings > About Microsoft Edge or enable auto-updates.
- Apply Security Patches: Microsoft releases emergency fixes for browser vulnerabilities—never delay these updates!
- Disable JavaScript: Advanced users can temporarily disable JavaScript; however, this breaks most modern web functionality.
- Use Enhanced Protection: Tools like Windows Defender SmartScreen and Microsoft Defender for Endpoint can provide extra shields.
Timeline of Events
- 2023-06: Vulnerability reported to Microsoft/Chromium devs.
- 2023-10: Microsoft releases security update patching the bug.
Final Thoughts
The emergence of CVE-2023-36034 shows us: modern browsers are both intensely complex and popular targets for attackers. *Even with the security focus of Chromium and Microsoft’s efforts, flaws like this remind us the update button is our friend.*
If you run Microsoft Edge—at home or at work—there’s nothing more important than staying patched.
Learn More
- Microsoft Security Advisory for CVE-2023-36034
- Chromium Security Release Notes
- NVD Entry for CVE-2023-36034
Stay safe, keep your software updated, and remember: today’s browser bug could be tomorrow’s ransomware!
*This post is unique, original content intended for educational purposes only; do not attempt unauthorized use or testing of vulnerabilities on systems you do not own or have explicit permission to test.*
Timeline
Published on: 11/03/2023 01:15:08 UTC
Last modified on: 11/13/2023 03:21:54 UTC