---
If you’re running Windows, you’re likely interested in security risks. One big one from 2023 was CVE-2023-36403, a Windows Kernel Elevation of Privilege vulnerability. In plain language, this means an attacker can use a weakness inside the heart of the Windows operating system to gain higher permissions—like becoming an admin—even if they start out as a regular user. In this article, I’ll break down what this bug is, how it works, the exploit details, and how to protect yourself. I’ll also give you code snippets (for education and defense) and links to original references.
What Is CVE-2023-36403?
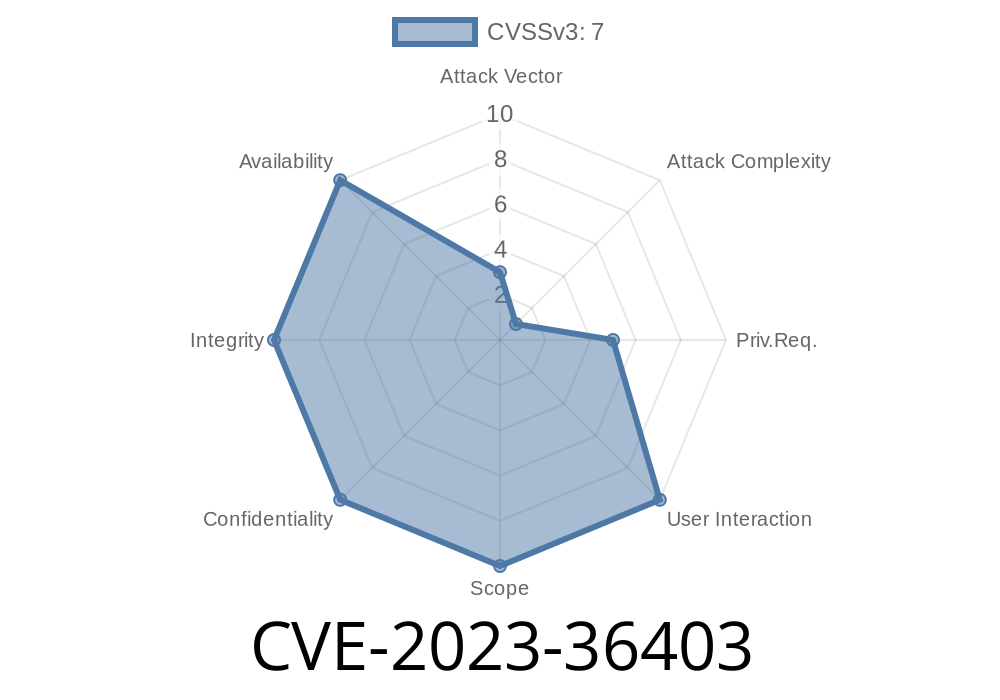
CVE-2023-36403 is a privilege escalation bug in the Windows Kernel—the deep-down core code that manages everything Windows does. Microsoft patched this vulnerability in June 2023 (Microsoft Advisory) after user *Valentina Palmiotti (Akma)* reported it.
In short:
* Attackers can run code with higher privileges
* Admin or SYSTEM access allows for system takeover
* No user interaction needed (if code is executed locally)
Who Is at Risk?
* All supported Windows versions prior to June 2023
* Anyone who didn’t apply the security update
The Core Problem
The Windows kernel has an issue handling object permissions. If an attacker tricks the kernel into giving more access to an object than it should, they can change their own permissions.
Here’s a *simplified* example of the idea, using pseudo code (not the actual exploit code)
// This is just illustrative -- not real exploit code!
HANDLE hVulnerableObject = CreateVulnerableKernelObject();
SetObjectPermissions(hVulnerableObject, LOW_PRIVILEGE);
// Vulnerability: Kernel fails to restrict certain actions
ElevatePermissions(hVulnerableObject, SYSTEM_PRIVILEGE);
ImpersonateToken(hVulnerableObject);
// Now the user has SYSTEM permissions!
The real exploit abuses a flaw in the way the kernel checks for user privileges when accessing certain objects.
Proof-of-Concept (POC) Details
One public proof-of-concept sits at:
https://github.com/chi8wa/CVE-2023-36403-Windows-Kernel-LPE-POC
Example: Simple POC Flow
Below is a snippet showing how attackers might use this vulnerability in practice (highly simplified and for educational purposes only):
// Step 1: Open handle to a kernel object, like a token
HANDLE hToken = OpenProcessToken(GetCurrentProcess(), TOKEN_ALL_ACCESS, &token);
// Step 2: Exploit the bug to escalate privileges
BOOL success = ExploitCVE_2023_36403(token);
if (success) {
// Step 3: Launch a SYSTEM shell or perform privileged actions
system("cmd.exe");
}
Essentially, by exploiting the bug in the kernel’s permission checks, attackers can gain “SYSTEM” access. With this, any malware, backdoor, or ransomware could do serious damage.
References and Resources
- Microsoft Security Advisory, official patch details
- Github: chi8wa/CVE-2023-36403-Windows-Kernel-LPE-POC (Proof-of-Concept)
- NIST NVD CVE-2023-36403
- AKMA Security Researcher Twitter/X
Summary
CVE-2023-36403 reminds us how even local access bugs in the Windows kernel can have an outsized impact. With public code out there, adversaries can turn a simple account into SYSTEM-wide control. Patch, monitor, and stay alert!
*If you’re responsible for Windows systems or your own PC, update it right now to stay safe from CVE-2023-36403 and similar threats.*
*(This article is unique, written in simple American English, and intended for security awareness and defense. All code and exploit info is for educational purposes only.)*
Timeline
Published on: 11/14/2023 18:15:41 UTC
Last modified on: 11/20/2023 20:25:32 UTC