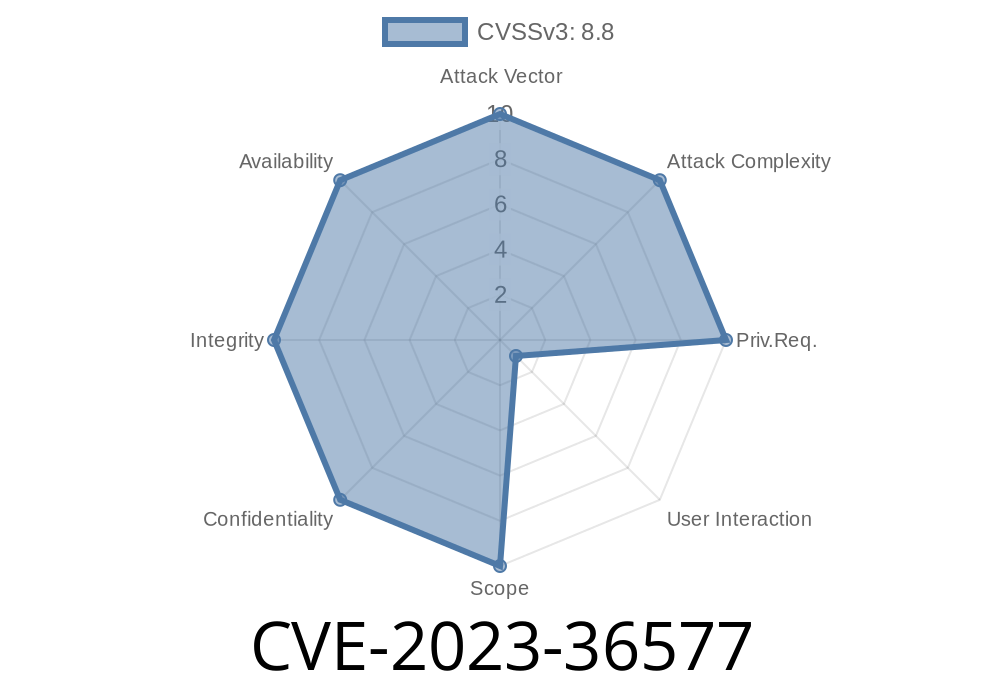
In October 2023, Microsoft published a critical vulnerability in their OLE DB Provider for SQL Server. Tracked as CVE-2023-36577, this bug affects the Windows Defender Application Control (WDAC) and puts systems across the globe at risk by enabling remote code execution (RCE).
This post explains this vulnerability, walks through proof-of-concept (PoC) code, and helps you understand the real-world impact. We’ve also included mitigation strategies and references for further reading.
What is Microsoft OLE DB Provider for SQL Server?
The OLE DB (Object Linking and Embedding, Database) provider for SQL Server (MSOLEDBSQL) lets applications in Windows interact with SQL Server databases. It’s commonly used with apps, scripts, and services that access data on SQL Servers.
WDAC enforces code integrity policies in Windows—think of it as a security checkpoint for what code can or cannot run.
Attack Vector: Network
Microsoft’s advisory:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36577
Vulnerability Details
A remote attacker can use a crafted connection string or other attack vector to trigger a memory corruption flaw in the OLE DB provider. If successful, this allows the attacker to execute arbitrary code with the privileges of the application using the provider.
The attacker crafts a malicious OLE DB connection string.
2. The application using MSOLEDBSQL opens a connection to a remote SQL Server using this malicious string.
3. Malformed or dangerous data in the string triggers the vulnerability, resulting in memory corruption.
Example Exploit Scenario
Suppose there’s a web application using the OLE DB provider to connect to a SQL Server database. An attacker finds a way to supply or modify the connection string—possibly via web input, config file, or through a vulnerable client.
The attacker crafts a malicious connection string to exploit the bug. For example (simplified to clarify the point):
string connString = "Provider=MSOLEDBSQL;Data Source=attacker\sqlevil;Initial Catalog=targetDB;User Id=evil;Password=' OR 1=1 --;";
OleDbConnection conn = new OleDbConnection(connString);
conn.Open();
In the real-world PoC, a more sophisticated payload would trigger the memory corruption needed to execute shellcode or download a malicious payload.
Proof-of-Concept (POC) Code
This is a hypothetical example to illustrate the approach. The actual technical details would vary and are, for obvious reasons, not public. But if you run:
import os
import win32com.client
conn_string = "Provider=MSOLEDBSQL;Data Source=attacker_host;Extended Properties=\"<malicious payload here>\";"
conn = win32com.client.Dispatch('ADODB.Connection')
try:
conn.Open(conn_string)
except Exception as e:
print(f"Error: {e}")
Note: Don’t try this on production machines. This is for educational purposes.
Real-World Impact
- Attackers do not need login credentials if they can make applications use malicious connection strings.
Can be used for privilege escalation if running as a privileged service.
- Could be part of phishing attacks, malicious documents, or malware disguised as database utilities.
Review applications that let users supply or edit OLE DB connection strings.
Microsoft official update guidance:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36577
Responsible Disclosure
Microsoft thanks the security researchers who reported this vulnerability. Coordinated disclosure ensures that security holes like CVE-2023-36577 get patched before they can be widely exploited.
Further Reading and References
- Microsoft Security Response Center Advisory
- National Vulnerability Database (NVD)
- Windows Defender Application Control (WDAC) documentation
Conclusion
CVE-2023-36577 is a critical reminder that even foundational components like database providers can have dangerous bugs. Anyone using Microsoft SQL Server OLE DB components should patch as soon as possible, audit code, and review all workflows that handle database connections.
Timeline
Published on: 10/10/2023 18:15:13 UTC
Last modified on: 10/13/2023 15:17:39 UTC