A deep dive into a critical path traversal flaw that exposes your website to Local File Inclusion (LFI) risks.
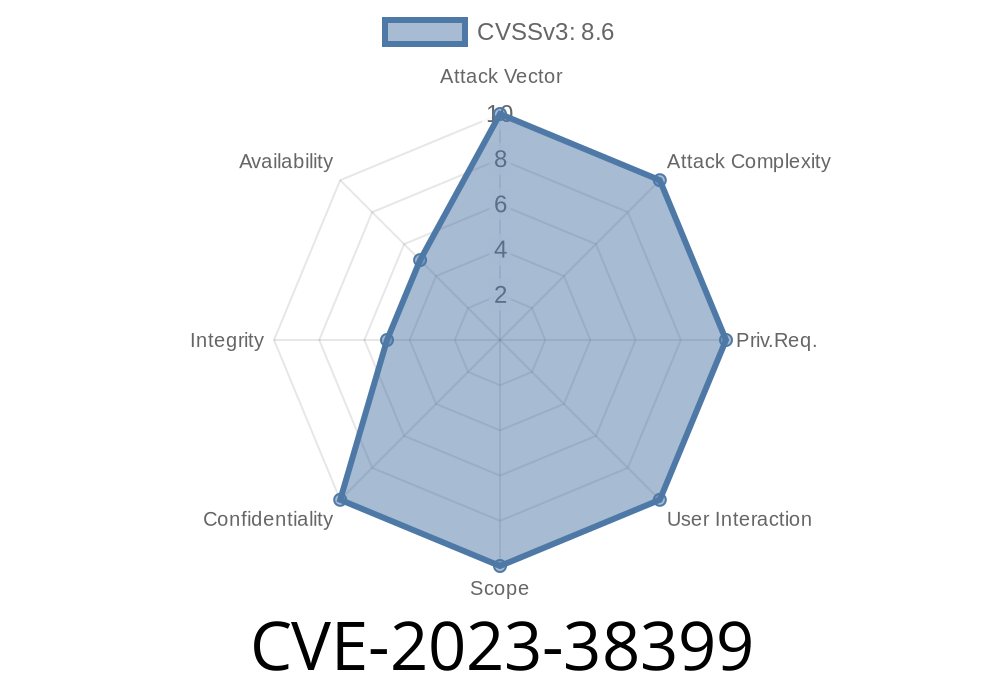
What is CVE-2023-38399?
CVE-2023-38399 is a security vulnerability found in Averta Phlox Portfolio, a popular WordPress plugin for portfolio design. This flaw lets attackers perform Path Traversal, ultimately triggering local file inclusion (LFI) through PHP code. In simpler terms: Hackers can read, and sometimes execute, files they shouldn’t have access to on your web server.
Affected plugin: Phlox Portfolio
Vulnerable versions: Up to and including 2.3.1
Why is This Dangerous?
A Path Traversal flaw means someone can manipulate file paths in the software to break out of the intended directory. If the program doesn’t check the filename well enough, an attacker could fetch sensitive files (like wp-config.php or /etc/passwd) or inject scripts.
*Attackers can:*
Below is a simplified PHP example of code logic that might appear in vulnerable plugins
<?php
// Retrieves a filename from the user via GET
$file = $_GET['portfolio_file'];
// Builds the full path (vulnerable: NO validation)
$path = '/var/www/wp-content/plugins/phlox-portfolio/files/' . $file;
if (file_exists($path)) {
include($path); // This is dangerous!
} else {
echo "File not found!";
}
?>
With NO filtering or sanitization, an attacker can exploit this by sending
http://example.com/wp-content/plugins/phlox-portfolio/show.php?portfolio_file=../../../../../../etc/passwd
This loads and displays the Unix password file instead of a legitimate portfolio asset!
1. Find the vulnerable input
The attacker finds an endpoint accepting portfolio_file or something similar.
2. Try payloads
They submit payloads like ../../../../wp-config.php to break out of the intended directory.
3. Exfiltrate files
If the code doesn’t check for .. or absolute paths (or file extensions), it will read or even include arbitrary files!
Example Exploit: Reading WordPress Config
GET /wp-content/plugins/phlox-portfolio/show.php?portfolio_file=../../../../wp-config.php HTTP/1.1
Host: victim.com
Suddenly, the page shows your entire DB password and settings!
What makes it happen?
Lack of filename sanitization and filtering.
The code should check that the filename
- Doesn't include ../
Here’s how you *should* secure such file handling
<?php
$file = basename($_GET['portfolio_file']); // Strips traversal chars
$allowed_extensions = array('jpg','jpeg','png','pdf');
$ext = strtolower(pathinfo($file, PATHINFO_EXTENSION));
if (!in_array($ext, $allowed_extensions)) {
die("Invalid file type!");
}
$base_path = realpath('/var/www/wp-content/plugins/phlox-portfolio/files/');
$target = realpath($base_path . '/' . $file);
// Check file is actually inside allowed dir
if ($target === false || strpos($target, $base_path) !== ) {
die("Hack attempt detected!");
}
include($target);
?>
References & Further Reading
- CVE-2023-38399 at NIST
- Patchstack Advisory Page (Advisory and PoC)
- WordPress Plugin Directory - Phlox Portfolio
- OWASP: Path Traversal Cheat Sheet
Final Thoughts
Path Traversal and LFI are preventable attacks, but still common due to oversights in input validation. WordPress plugin authors and site owners must validate all user input. If you’re managing Phlox Portfolio, update now—your site's security may depend on it.
Timeline
Published on: 05/17/2024 07:15:58 UTC
Last modified on: 06/04/2024 17:28:18 UTC