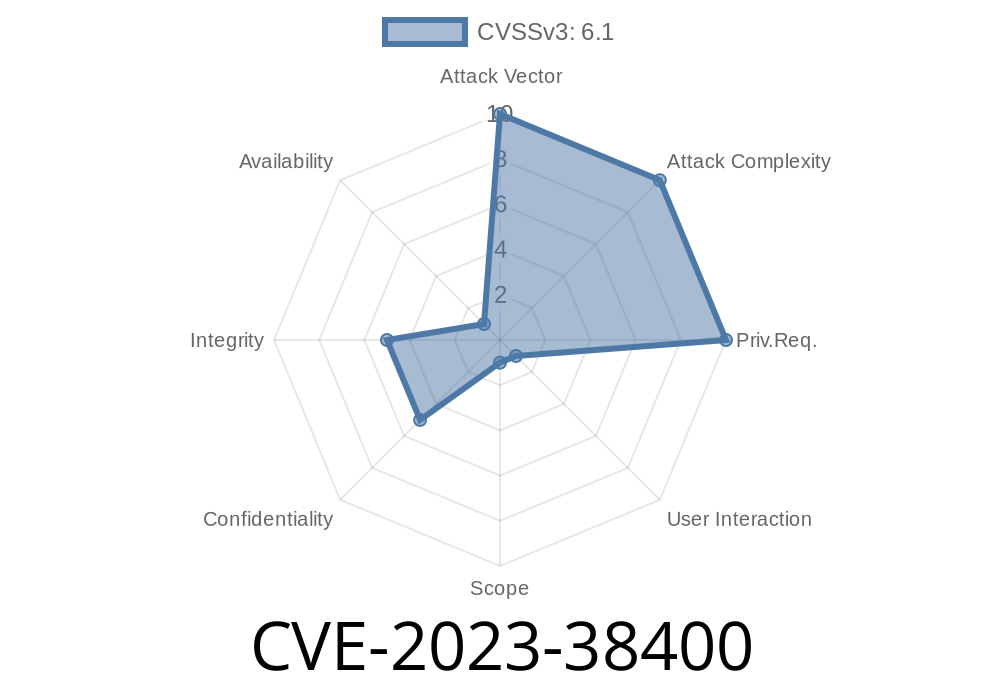
_If you’re a WordPress user running the popular Enfold theme by Kriesi, there’s a serious security issue you need to know about. CVE-2023-38400 is a Cross-site Scripting (XSS) vulnerability that affects Enfold versions up to 5.6.4. In this post, I’ll break down how this vulnerability works, why it’s dangerous, and show a technical example with references to help you secure your website._
What Is CVE-2023-38400?
CVE-2023-38400 is an Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability, or simply: a reflected XSS bug. This flaw happens because the Enfold theme does not properly filter user input before displaying it on the page. As a result, attackers can inject JavaScript code into web pages. If a user clicks a malicious link, that code can steal cookies, redirect users, or deface your site—all without your knowledge.
Why Should You Care?
This vulnerability is critical for anyone using Enfold with clients, e-commerce stores, or user logins. Successful exploitation lets hackers:
How Does the Exploit Work?
The issue is “reflected” XSS. This means that the attacker crafts a malicious URL and tricks a user (perhaps via email, social, or a public forum) into clicking it. The dangerous code rides along in the URL and is displayed—unfiltered—by the Enfold theme.
Victim clicks link: The user is authenticated or trusts the site.
3. Malicious script executes: Since the input isn’t properly escaped, the browser runs the code, stealing data or performing actions as the victim.
Technical Example (Proof of Concept)
Let’s say the vulnerable Enfold page echoes the s parameter in search results without sanitization.
Malicious URL Example
https://your-enfold-site.com/?s=<script>alert('Hacked by CVE-2023-38400')</script>
Vulnerable code snippet (hypothetical)
<?php
// Example search page snippet in Enfold
$search = $_GET['s']; // BAD: no escaping!
echo "You searched for: $search";
?>
When a user clicks the attacker’s link, the browser renders
You searched for: <script>alert('Hacked by CVE-2023-38400')</script>
And pops an alert (or worse).
Visit your Enfold site and add the following parameter
`
?s=
If you see an alert pop up, your theme is vulnerable!
Manual Testing Tip:
Use browser developer tools, or automated scanners like wpscan.
Update Enfold Theme to Version 5.6.5 or Higher!
Kriesi released a patch addressing this improper input neutralization. Always keep your themes and plugins up to date.
Use a Web Application Firewall (WAF).
- Add extra input sanitization with WordPress sanitization functions.
Better Search Code Example
<?php
$search = esc_html($_GET['s']); // GOOD: escapes HTML output
echo "You searched for: $search";
?>
References
- NVD CVE-2023-38400 Entry
- Patch Release Announcement by Kriesi (ThemeForest)
- Wordfence XSS Guide
- WPScan Vulnerability Entry
Conclusion
CVE-2023-38400 is a real risk for anyone running the Enfold theme on their WordPress site. This reflected XSS allows attackers to exploit your visitors with one click. The solution is simple: Update to at least Enfold 5.6.5.
Stay secure, keep your software up to date, and always be cautious about user input!
If this helped, please share with friends and clients using WordPress.
Timeline
Published on: 11/30/2023 17:15:09 UTC
Last modified on: 12/05/2023 22:08:09 UTC