Kirby is a flexible, file-based content management system (CMS) used by thousands for blogs, company sites, and personal portfolios. While Kirby is popular for its ease of use and flat-file structure, a critical vulnerability—CVE-2023-38489—was discovered that could seriously impact the security of any Kirby-powered website with user accounts. This article will break down what happened, how attackers could use it, and how you can protect your site.
What is CVE-2023-38489?
CVE-2023-38489 refers to a security weakness termed Insufficient Session Expiration. In simple terms, even if a user changes their password to lock out a potential attacker, the old session (which the attacker may still be using from another device) isn't logged out automatically. This means someone with access to an old session could still access the site as that user, even after the password has changed.
Impacted Versions:
3.9.6
If you're using any older version, your users could be at risk!
How Did the Attack Work?
Let’s imagine you’re using Kirby for your organization’s website. You log in on your work computer and, at some point, an attacker learns your password (maybe through phishing or by using your device when you step away).
You realize your password was compromised and you change it immediately.
But here’s the kicker:
The attacker who is already logged in—maybe from their own device—will *stay* logged in, even though you changed your password.
If you didn't log out from all sessions manually, there was no technical way Kirby would automatically boot the attacker out. The old session would remain alive.
Can only be abused if:
- A user is logged in on a shared/untrusted device, or
Insufficient Session Expiration
Most modern systems tie user sessions to a password hash. When a password changes, *all* old sessions should become invalid. But in vulnerable Kirby versions, password changes did *not* invalidate existing sessions.
Typical Secure Logic (What Kirby Should Have Done)
// Pseudocode for session check
if (session.password_hash !== user.current_password_hash) {
// Invalidate session
logout();
}
Older Kirby Logic (Before Patch)
// Only check session is valid
if (session.user_id === user.id) {
// Keep session alive, even if password changed!
continue;
}
So, your session would remain valid after a password change—bad news if an attacker is holding onto your session cookie.
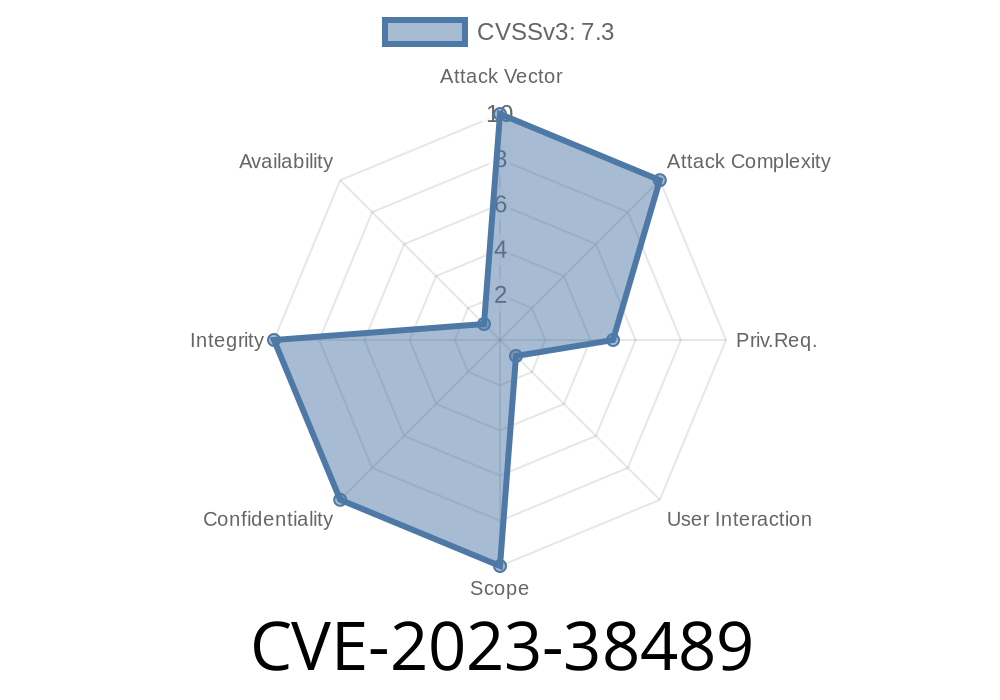
How Severe Is This?
Severity level: *HIGH*
Attackers with a stolen session or old password could maintain access, even after a password change.
- This is especially dangerous for shared computers, public devices (like libraries), or when account compromise is suspected.
What Did Kirby Do to Fix It?
In the patched versions (3.5.8.3, 3.6.6.3, 3.7.5.2, 3.8.4.1, and 3.9.6), the team updated Kirby’s authentication system:
Every user session now tracks the *hashed password* at login.
- If the password is changed, session validation compares the current user hash with the session’s hash. If they don’t match, the session is forcefully logged out.
- When you update to a patched version, all users are forced to log in again (all sessions are cleared). This ensures even pre-existing “stolen” sessions get invalidated.
Example of the New Check
// After login, store the hash
$_SESSION['password_hash'] = $user->passwordHash();
// On each request
if ($_SESSION['password_hash'] !== $user->passwordHash()) {
// Password changed; end session
session_destroy();
redirect('login');
}
Update Kirby Immediately
- Download latest Kirby releases
Don’t leave sessions open on shared or public machines.
- Consider disabling the Panel and API if not needed (see Kirby security guide).
Attacker keeps accessing site with the old session, still fully authenticated.
With the patch:
As soon as the attacker’s browser tries to use the old session, Kirby sees the hashes don’t match, destroys the session, and boots the attacker out.
References and Further Reading
- Official Kirby Security Advisory
- Kirby Changelog
- Kirby Hardening Guide
- CVSS and NVD Listing for CVE-2023-38489
Final Thoughts
Even simple CMS platforms can run into critical security flaws if session management is not airtight. CVE-2023-38489 shows how important it is to tie user sessions closely to the user’s credentials and to invalidate sessions after any critical change.
If you’re running Kirby, update today.
Don’t wait for an attacker to teach you the hard way about session security.
*Stay safe, and keep your sites locked down!*
*Writeup exclusive for you. Please credit Kirby and GitHub Security Advisory if sharing further.*
Timeline
Published on: 07/27/2023 15:15:00 UTC
Last modified on: 08/03/2023 13:28:00 UTC