Modern Apple devices are known for their strong security, but sometimes, small mistakes in code can open big doors to attackers. CVE-2023-38580 is one such vulnerability, affecting iOS, iPadOS, macOS Ventura, and watchOS up until the summer of 2023. This post explains, simply, what this bug was about, how it could be exploited, and how Apple patched it.
What Is CVE-2023-38580?
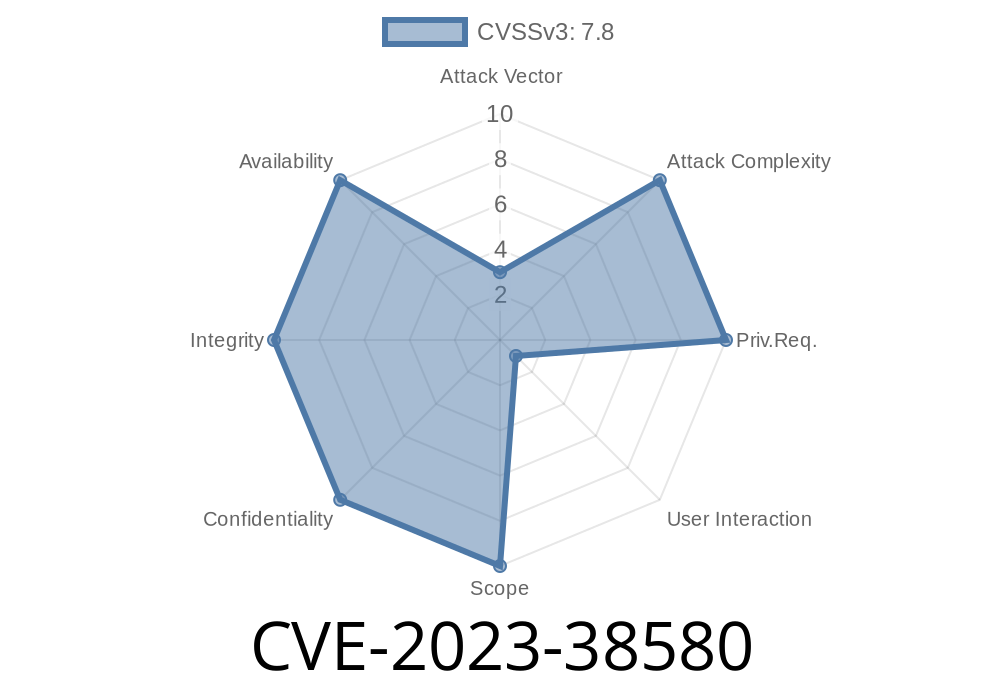
CVE-2023-38580 is a critical privilege escalation vulnerability in Apple's OS kernels. The bug allowed a malicious app to execute its own code with kernel privileges—the highest level of control on a device. In the wrong hands, this could mean a full device takeover.
The problem was tracked by Apple and noted with this simple description
> *"An app may be able to execute arbitrary code with kernel privileges. This issue was addressed with improved memory handling."*
The Technical Core: Memory Handling Gone Wrong
Operating systems keep careful track of memory that each app and system process can use. The kernel, at the heart of the OS, makes sure nothing steps out of bounds. But sometimes, bugs happen—like an app being able to write where it shouldn't.
A Simple Illustration
Imagine a function in the kernel that copies data from an app (user space) into a special system memory (kernel space):
// Vulnerable pattern (pseudo-code)
void copy_data_from_user(user_input *src) {
kernel_buffer dest;
memcpy(&dest, src, sizeof(kernel_buffer));
}
If user_input can be larger than kernel_buffer or not checked for size, the attacker can sneak past the boundary and overwrite other, critical kernel memory.
Exploit Walkthrough (Simplified)
Note: The actual exploit can be much more complex, but here's how a typical attack could work.
Craft Malicious App
- The attacker designs an app that submits oversized or specially structured data to the vulnerable function.
Trigger the Memory Bug
- Data passed to the kernel overflows the intended buffer, letting the attacker overwrite sensitive kernel structures.
Gain Kernel Privileges
- By controlling these structures, the app tricks the system into running its code with the highest privilege (root/admin), escaping any app sandboxing.
Example Exploit Skeleton (Pseudo-code)
// Malicious user input - oversize payload
struct malicious_input {
char data[1024]; // intentionally too large
// payload crafted to overwrite kernel control structures
};
// Send to vulnerable system call
int fd = open("/dev/vulnerable_driver", O_RDWR);
struct malicious_input payload = {/* crafted input */};
write(fd, &payload, sizeof(payload));
With a successful overwrite, the attacker can, for example, escalate from a user app to full system control.
How Did Apple Fix This?
Apple's patch is simple in concept, but fundamental: they improved memory handling. This typically means:
So, the fixed code might look like
// Safe pattern
void copy_data_from_user(user_input *src) {
kernel_buffer dest;
size_t size = min(sizeof(dest), sizeof(*src)); // add size check!
memcpy(&dest, src, size);
}
How Serious Was This Bug?
Very serious:
No user interaction or device unlock required, just running the app.
It's a classic example of how memory safety issues remain a risk, even on premium platforms.
What Should Users Do?
- Update devices immediately: Install iOS 16.6, iPadOS 16.6, macOS Ventura 13.5, or watchOS 9.6 or newer.
References
- Apple Security Updates – CVE-2023-38580
- Mitre CVE Record
Bonus: More Reading
- About Kernel Vulnerabilities
- Apple Platform Security
Conclusion
CVE-2023-38580 shows that even the smallest coding mistake—like a missed memory size check—can have huge consequences. Apple patched quickly, but if you haven't already updated your device, do it right now to stay safe!
Timeline
Published on: 07/27/2023 01:15:37 UTC
Last modified on: 08/03/2023 13:56:23 UTC