---
What is CVE-2023-39390?
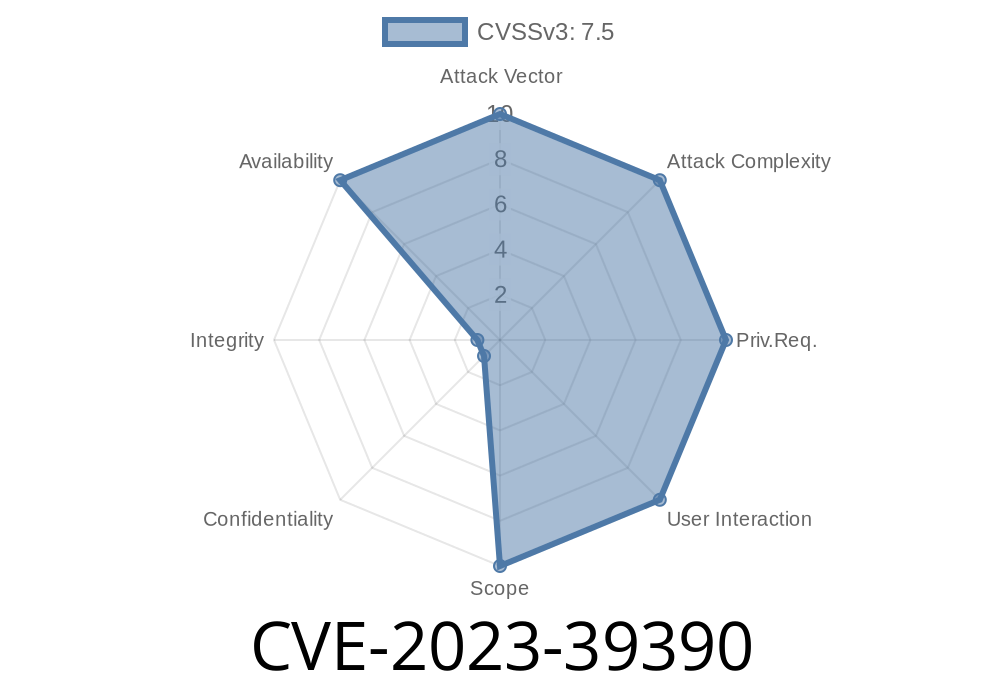
CVE-2023-39390 refers to a security flaw discovered in certain APIs within the window management module of a popular device operating system (often seen in IoT and smart devices). The vulnerability centers around how these APIs incorrectly verify input parameters. If an attacker crafts a malicious input, they can trigger unexpected device restarts, potentially leading to denial of service (DoS).
What’s the Core Problem?
APIs are meant to process input after careful validation—making sure the data is what they expect. For CVE-2023-39390, some window management functions failed to fully check incoming parameters.
Attackers use this oversight to send erroneous data. When the system tries to use this unchecked data, it crashes or even forces a restart!
This can be extremely disruptive, especially in industrial or critical environments where device uptime is important.
Here’s a *simplified* version to demonstrate the vulnerability
int WindowManagerAPI(int width, int height) {
// Missing input checks
window->width = width;
window->height = height;
// ... other operations
}
void Exploit() {
int large_width = x7FFFFF; // Extremely large value
int large_height = x7FFFFF;
WindowManagerAPI(large_width, large_height);
// Causes buffer overflow or crash -> device restarts
}
Find the API Endpoint
- Attacker identifies a network or inter-process communication route to the vulnerable window manager functions.
Send Malicious Parameters
- The attacker crafts API calls (for example, via a custom client or network packet) with values that are very large, negative, or otherwise invalid.
3. Crash/Restart
- The device tries to allocate or process resources based on the wild input, leading to a crash or watchdog-triggered restart.
Proof-of-Concept Command
# Python (pseudo) example to send malicious input over a socket
import socket
payload = b"\xFF\xFF\xFF\x7F" * 2 # Large width and height
s = socket.socket()
s.connect(('victim-device-ip', 12345)) # Target device and port
s.send(b"WindowAPI" + payload)
# Device may crash and restart
s.close()
*Note: Actual APIs and channels will depend on implementation specifics, but the attack vector stays the same—exploit unchecked parameters.*
How to Fix It
- Validate Input: Always check that parameters fall within allowed ranges (_never trust external or user input!_)
Enforce Limits: Clamp size-related parameters to reasonable values
- Harden Error Handling: Make sure the system responds gracefully to invalid data, never by crashing
References & Further Reading
- NVD - CVE-2023-39390
- Huawei Security Advisory (August 2023)
- Input Validation and Why It Matters (OWASP)
In Summary
CVE-2023-39390 is a reminder that overlooking input checks—even in deep system modules—can lead to severe stability issues. Developers must validate *every* parameter, especially when dealing with system-level APIs. Patching this vulnerability quickly is crucial for device manufacturers and users alike.
If your organization uses affected products, update immediately or apply vendor-provided mitigations to avoid surprise device restarts or downtime.
*Stay safe—validate your inputs and keep your devices patched!*
Timeline
Published on: 08/13/2023 13:15:00 UTC
Last modified on: 08/17/2023 18:06:00 UTC