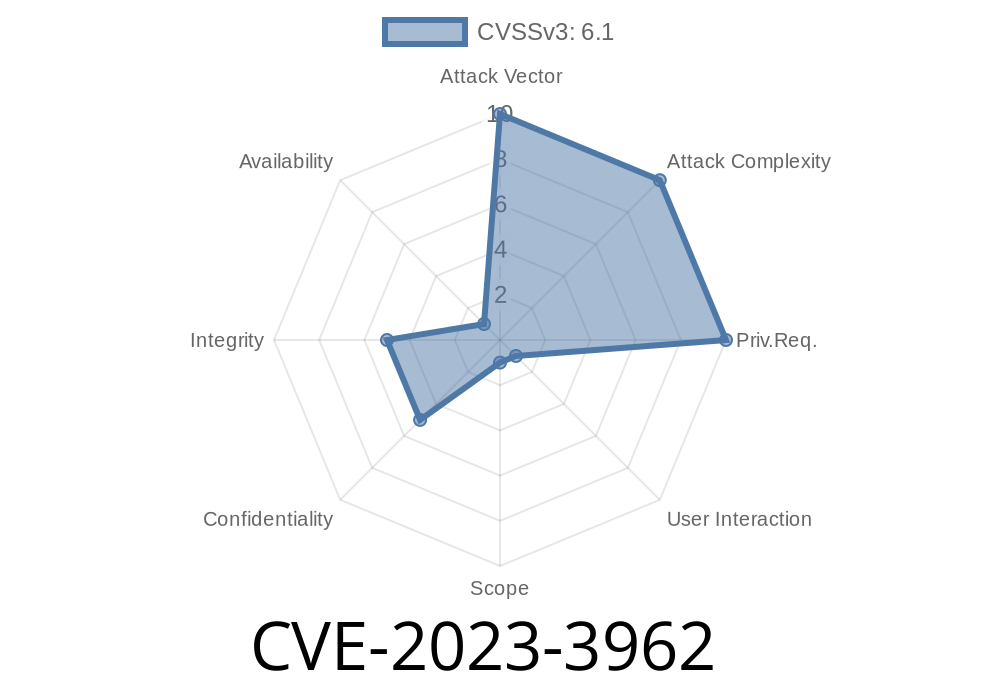
WordPress remains one of the most popular website platforms, but with popularity comes risk. Recently, a serious security vulnerability (CVE-2023-3962) was found in the Winters WordPress theme, affecting versions up to and including 1.4.3. This bug allows attackers—without requiring any login—to exploit reflected Cross-Site Scripting (XSS) via prototype pollution, making it possible to inject and execute arbitrary scripts, risking site compromise or data theft. In this article, we’ll break down how the vulnerability works, see proof-of-concept code, and learn how attackers can actually abuse it.
What is Prototype Pollution? (Simply Explained)
Prototype pollution is a vulnerability unique to JavaScript. JavaScript objects have something called a "prototype," which acts like a template for all objects of that type. If you can change the prototype, you can influence the behavior of *every* object created from it.
In the case of the Winters theme, insecure handling of user-supplied input means attackers can inject values that modify how JavaScript objects work—sometimes letting them run scripts that were not supposed to be possible.
How Reflected XSS Happens Here
Reflected XSS occurs when you send malicious data to a website, and that data is returned in the response without proper sanitization or escaping. If a user (especially an admin) can be tricked into clicking a crafted link, the script will run in their browser.
In this vulnerability, attackers could exploit the combination of bad input validation and output escaping along with the prototype pollution flaw to deliver malicious JavaScript to other users.
Code Snippet: The Injection Path
Here’s a simplified code example illustrating the path exploited in the Winters theme (in real life, the code is more complex, but this shows the basics):
<?php
// Simulating the vulnerable handler in the theme's PHP files
$param = $_GET['winters_param'] ?? '';
echo "<script>
var settings = " . json_encode($param) . ";
// Use settings object somewhere
// window.wintersSettings = settings;
</script>";
?>
If the site is not validating or encoding winters_param properly, this can be abused. Additionally, a related JavaScript snippet (embedded or loaded by the theme) might look like this:
let userSettings = {};
Object.assign(userSettings, window.wintersSettings);
// If an attacker sets wintersSettings to {"__proto__": {"isAdmin": true}},
// ALL new objects now have isAdmin=true!
Suppose a victim is tricked into clicking this crafted URL
https://vulnerable-site.com/?winters_param={"__proto__":{"toString":"alert('XSS!')";}}
If the theme fails to sanitize winters_param, the injected prototype can override core JavaScript behavior. Now, somewhere in the page, if toString() is called on any object, it could run alert('XSS!'), or worse.
Or, with direct reflected XSS
https://victim.com/?winters_param=<script>alert('Pwned!')</script>;
If the page echos back winters_param unsafely, the attacker's script executes immediately.
Send the link to a target user (admin is best, but any user is vulnerable).
4. If user clicks the link, the malicious script runs in their browser—hijacking sessions, stealing data, or manipulating the site.
Links to Original References
* WPScan Advisory (CVE-2023-3962)
* NIST NVD Entry
* What is Prototype Pollution?
* OWASP: Cross-site Scripting (XSS)
Remediation
Update Immediately: If you use the Winters theme, upgrade past 1.4.3 as soon as possible.
Conclusion
CVE-2023-3962 is a clear reminder that even visual, seemingly simple WordPress themes can contain dangerous vulnerabilities. Attackers don't need any credentials to exploit reflected XSS via prototype pollution, and just one click from a victim could compromise your whole site. Always stay updated and think twice before clicking suspicious links!
*Stay safe—patch and review your site’s security regularly!*
Timeline
Published on: 10/20/2023 16:15:19 UTC
Last modified on: 11/07/2023 04:20:02 UTC