WordPress is a beloved platform, powering over 40% of the web. Millions of businesses rely on plugins to enrich their sites, like the vCita Online Booking & Scheduling Calendar, a handy tool for getting appointments and managing clients.
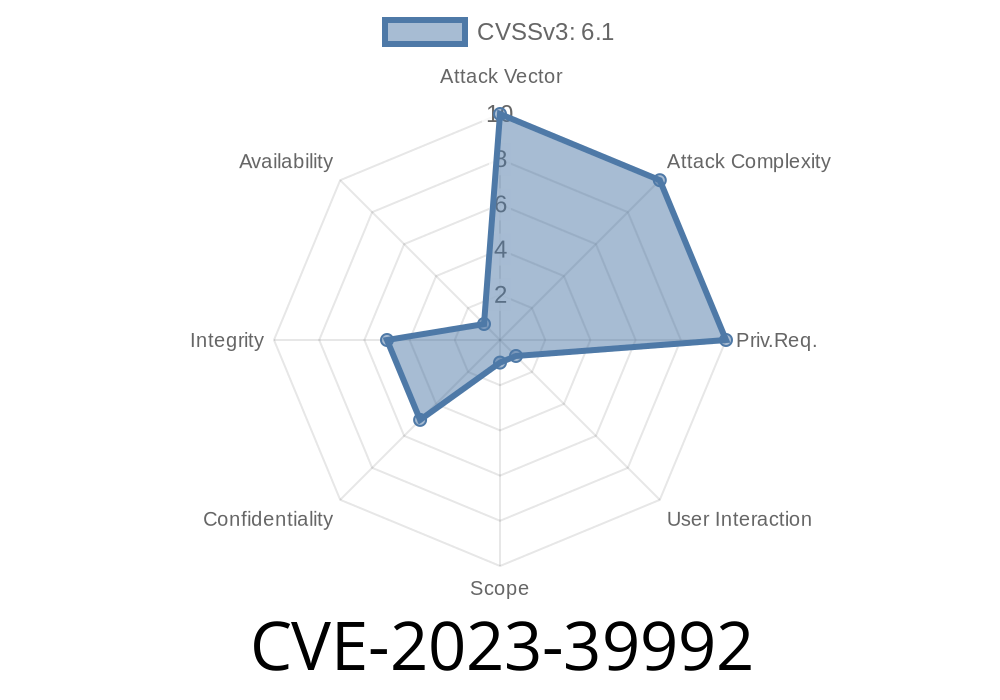
But in 2023, a serious Unauthenticated Reflected Cross-Site Scripting (XSS) vulnerability—CVE-2023-39992—was found in vCita's plugin (versions <= 4.3.2), putting site visitors and business owners at risk.
This exclusive post breaks down the vulnerability in simple terms, shares a sample proof-of-concept, and points you to more references so you can check your site or just deepen your knowledge.
What Is Reflected XSS?
First, a quick recap:
Reflected XSS means an attacker tricks a user into clicking a specially crafted link. The site, without checking, puts unfiltered data from that link straight into the page, running malicious JavaScript in the victim’s browser.
If the attacker succeeds, they can do things like steal cookies, impersonate the user, or mess with what the user sees.
About the vCita Plugin Vulnerability
Plugin Affected: vCita Online Booking & Scheduling Calendar for WordPress
Vulnerable versions: 4.3.2 or lower
Type: Unauthenticated Reflected XSS
The worst part? No login needed to trigger the bug. Anyone can exploit it if your site uses a vulnerable plugin version.
How It Happened
In vulnerable plugin versions, certain URL parameters passed to the plugin page were echoed into HTML responses without being properly escaped or sanitized. This lets attackers slip malicious JavaScript straight into the page a user is viewing.
Technical Details & PoC
Let's get specific.
The reflected XSS is found in the plugin's public-facing booking calendar page. A parameter (let’s call it wplc_id for example) is echoed back unescaped.
Suppose your site uses the plugin and your booking page is at
https://victim.com/your-booking-page/
The vulnerable parameter is appended as a GET variable
https://victim.com/your-booking-page/?wplc_id=<script>alert('XSS')</script>
When a victim clicks the malicious link, the <script>alert('XSS')</script> parameter gets rendered on the page, popping an alert. A real-world attacker could do much worse—steal session cookies, run keyloggers, etc.
A simplified example of bad PHP practice that leads to this
<?php
$wplc_id = $_GET['wplc_id']; // No validation or escaping!
echo "<div id='booking'>" . $wplc_id . "</div>";
?>
If someone visits
/?wplc_id=<script>alert('XSS')</script>
The script runs!
`
https://victim.com/booking/?wplc_id=
References & Original Reports
- NVD – CVE-2023-39992
- WPScan Vulnerability Database
- Plugin directory – vCita Online Booking
Patching & Mitigation
The fix:
The bug is resolved from v4.3.3 (August 2023) onward by sanitizing and escaping URL inputs.
Update NOW: Go to Plugins > Update vCita to the latest version.
- Use a security plugin (Wordfence, Sucuri) to scan your installation.
Replace bad code
echo $_GET['wplc_id'];
With good code
echo htmlspecialchars($_GET['wplc_id'], ENT_QUOTES, 'UTF-8');
Conclusion
CVE-2023-39992 shows how simple coding oversights can cause major problems for WordPress businesses.
By staying informed, updating plugins, and following coding best practices, we can all make WordPress websites safer for everyone.
If you’re running vCita’s calendar, patch up!
For more technical break-downs, follow the original sources or sign up for plugin security mailing lists.
Timeline
Published on: 09/04/2023 11:15:41 UTC
Last modified on: 09/06/2023 22:32:25 UTC