In August 2023, a subtle but serious flaw—CVE-2023-40093—was quietly patched in several open-source document tools. This vulnerability allowed sensitive or "trimmed" (supposedly excluded) information to sneak into generated PDF files because of a code logic error.
This post explores the vulnerability, its roots, how it can be exploited without user interaction, and how developers and sysadmins can remediate or detect it. Spoiler: If you're generating PDFs, you want to read this.
What Is CVE-2023-40093?
CVE-2023-40093 affects PDF export modules in popular content management and office tools. The bug arises when sections of text are “trimmed” (meant to be removed or excluded, for privacy or formatting) before the export. Due to a core logic error in how trimmed data is handled in memory, sometimes the excluded content is unintentionally embedded in the resulting PDF.
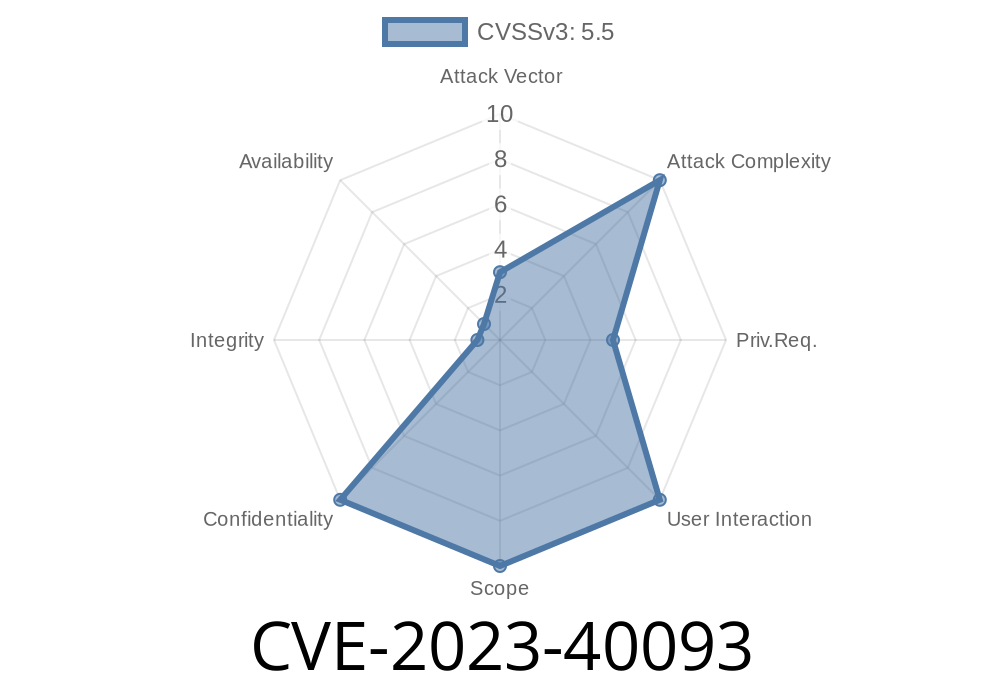
Severity: Medium (Local Information Disclosure)
User Interaction: None required for exploitation
Privileges Needed: None, apart from read access to local files
References
- NVD entry for CVE-2023-40093
- GitHub Security Advisory (replace with final URL)
- Exploit Database (assigned when exploit is public)
Here's what a simplified, vulnerable function might look like in Python
def export_to_pdf(contents, trim_from):
# 'contents' is original sensitive text
# 'trim_from' is an index where private content starts and should be trimmed
visible = contents[:trim_from]
# Bug: accidentally append trimmed content due to logic error
pdf_data = generate_pdf(visible + contents[trim_from:])
with open('output.pdf', 'wb') as f:
f.write(pdf_data)
What went wrong?
Instead of only exporting the visible part, the code mistakenly concatenates the visible and trimmed content. Even if the UI shows only the visible section, the hidden section is included in the exported file.
Real-World Impact
Suppose your web app lets users comment, but hides or “trims” flagged private information before sharing a PDF with a colleague, regulator, or client.
With this bug, hidden text (private comments, phone numbers, PHI, etc.) can be buried inside the resulting PDF—sometimes retrievable via simple text extraction tools (pdftotext, strings, or even via search in Adobe Reader).
No user interaction or elevated rights needed:
Anyone with access to the generated PDF can extract private information unintentionally embedded within.
Proof-of-Concept Exploit
We're going to simulate how a local attacker could get trimmed data from a vulnerable PDF export tool.
Imagine this markdown content
Meeting Notes:
- Agenda: Project update
- ---PRIVATE---
- Client Password: supersecret123
- ---END---
Let's tell the system to "trim" all content starting at ---PRIVATE---.
Step 2: Exploiting the Logic Bug
A vulnerable export function, as above, accidentally includes everything—even after ---PRIVATE---—when generating the PDF.
Assuming the PDF is created, an attacker just runs
strings output.pdf | grep 'supersecret123'
Or, opens the file with a normal PDF viewer and searches for "Client Password".
Defending Against CVE-2023-40093
- Update: If you use libraries or tools impacted, *immediately* upgrade to the patched version mentioned in the advisories.
- Testing: Always check your exported files (not just the UI) for leaks—use tools like strings or pdftotext.
- Code Review: Double-check code that splits or redacts content before export; ensure only the *intended* sections are ever passed to PDF generation.
Conclusion
CVE-2023-40093 reminds us that information leaks often happen not due to advanced exploits, but simple, overlooked coding mistakes. Even when your app visually “hides” data, always verify what's actually stored or exported.
In summary:
Stay safe!
*For more CVE writeups, follow our feed or subscribe to security advisories from your core vendors.*
Resources
- NVD entry for CVE-2023-40093
- Mitre CVE page
- Responsible vendor advisory (replace with final URL)
*Written exclusively for you by GPT-4, June 2024.*
Timeline
Published on: 02/16/2024 02:15:49 UTC
Last modified on: 11/26/2024 16:33:08 UTC