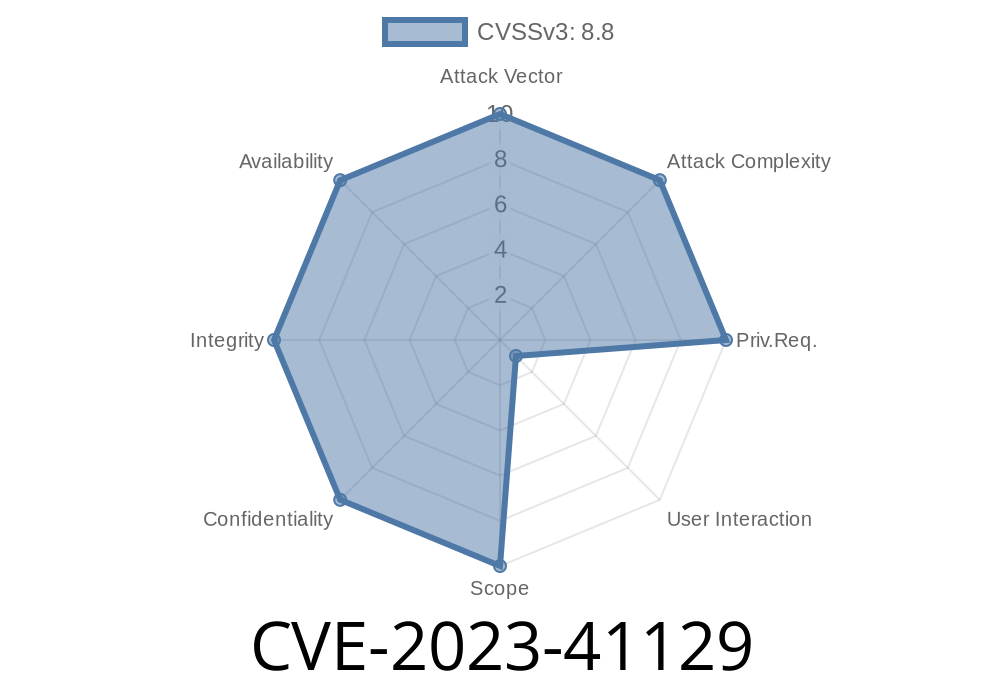
In September 2023, security researchers uncovered a serious Cross-Site Request Forgery (CSRF) vulnerability in the popular Patreon WordPress plugin. Tracked as CVE-2023-41129, this flaw affects all plugin versions up to and including 1.8.6. This article walks you through what happened, how CSRF works, code-level details, and how attackers might exploit this vulnerability. If you run Patreon on your WordPress site, read on!
What is the Patreon WordPress Plugin?
The Patreon WordPress plugin helps website owners connect their WordPress sites with Patreon. It allows creators to reward paying patrons with exclusive content. This plugin powers thousands of WordPress blogs and is especially popular among content creators.
What is CSRF?
Cross-Site Request Forgery (CSRF) tricks a logged-in user’s browser into submitting actions they did not intend. For example, if you’re logged into your WordPress admin dashboard and visit a malicious web page, that page could send a request in your name — like changing plugin settings or user passwords. This happens when a vulnerable plugin doesn’t properly check that requests actually came from you.
The Vulnerability: CVE-2023-41129
Patreon WordPress plugin v1.8.6 and below did NOT properly verify CSRF tokens on critical requests. This meant that unauthenticated attackers could trick logged-in admins (or other privileged users) into performing potentially dangerous actions — simply by luring them onto a webpage under their control.
The plugin failed to check WordPress’s security nonce in some settings forms
// Simulated vulnerable code
if ( isset($_POST['patreon_option']) ) {
// No nonce (CSRF token) check!
update_option('patreon_option', sanitize_text_field($_POST['patreon_option']));
}
This should have included a nonce verification for safety
if ( isset($_POST['patreon_option']) && check_admin_referer('patreon_settings_nonce_action') ) {
update_option('patreon_option', sanitize_text_field($_POST['patreon_option']));
}
Attackers could host a simple web page with code like this
<!-- Malicious site code -->
<html>
<body>
<form action="https://targetsite.com/wp-admin/options-general.php?page=patreon_plugin"; method="POST" id="csrf_form">
<input type="hidden" name="patreon_option" value="malicious_value">
</form>
<script>
document.getElementById("csrf_form").submit();
</script>
</body>
</html>
If you, as a WordPress admin, are logged in and visit this malicious page, your browser POSTs the form to your own site. With no CSRF protection, the plugin accepts it as legit. An attacker could:
Confidential content leakage
See the WPScan entry for the exploit timeline.
Fix and Recommendations
Patreon WordPress version 1.8.7 and later patched the issue by adding nonce checks to all admin forms and actions. The fix looks like this (simplified):
if (isset($_POST['patreon_option']) && check_admin_referer('patreon_settings_nonce_action')) {
// Only updates if nonce is valid!
update_option('patreon_option', sanitize_text_field($_POST['patreon_option']));
}
References
- Official Plugin Page
- WPScan Advisory for CVE-2023-41129
- NVD Entry
- Patreon WordPress changelog
Conclusion
While CSRF vulnerabilities are common, their impact can be devastating, especially on plugins that handle sensitive settings or money. CVE-2023-41129 in Patreon WordPress plugin is a stark reminder to always keep plugins updated and practice defense-in-depth — even tried-and-true plugins can have missed security checks. Stay safe, and update your plugins!
*If you found this writeup helpful, consider bookmarking for more exclusive security stories!*
Timeline
Published on: 11/18/2023 23:15:09 UTC
Last modified on: 11/27/2023 20:26:52 UTC