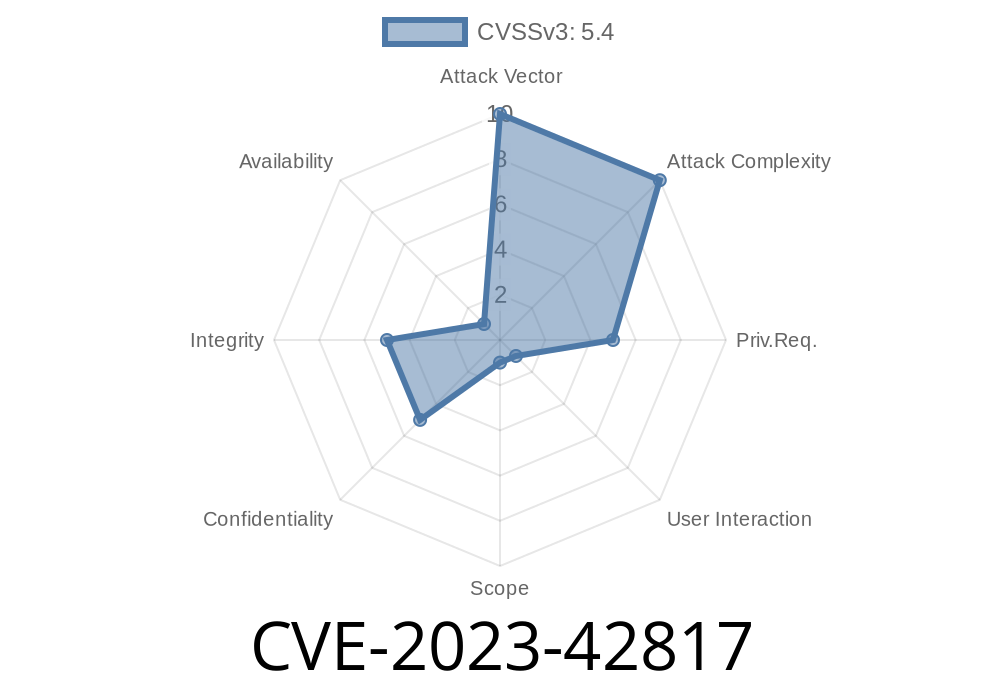
Pimcore, a popular open-source data and experience management platform, offers a classic admin backend UI as part of its admin-ui-classic-bundle. However, a security flaw identified as CVE-2023-42817 reveals how improper use of sprintf() with untrusted translations can open doors for skilled attackers—even those with only limited permissions.
In this detailed guide, we break down the vulnerability, demonstrate how it works, provide sample exploit code, and help you secure your Pimcore installation.
What is CVE-2023-42817?
The core of this vulnerability lies in Pimcore’s admin UI translation feature. In some cases, the translation strings—values designed to be displayed verbatim—include formatting tokens like %s. Instead of treating these as plain text, the application passes them to PHP’s sprintf() function, which attempts to substitute them with any extra variables provided. If an attacker can control the translation value, they may craft special strings to exploit this parsing, potentially affecting application behavior or user display—even with restricted permissions.
Pimcore’s permission model doesn’t tightly restrict access to translations, which increases the reach of this bug.
Suppose a translation for a UI dialog is defined as follows
// Fetched from translation file or database
$translationString = "%suggest: Please review %s before proceeding.";
// Used in code
echo sprintf($translationString, $someValue);
If an attacker can modify or supply $translationString, they might exploit sprintf()’s formatting behavior.
Attacker gains access to an account with translation editing rights.
2. Modifies a translation value to include malicious format strings or placeholders, such as %1$s %2$s %99999999$s.
3. When the vulnerable dialog box is rendered, sprintf() attempts to process the input, possibly causing errors, displaying unintended data, or even resulting in a Denial of Service or information leakage.
Suppose the translation for a warning dialog is changed to
"%s%s%s%s%s%s%s%s%s%s"
Sample Exploit Code
<?php
$malicious_translation = str_repeat('%s', 100000);
try {
// This will cause sprintf to expect 100,000 arguments!
echo sprintf($malicious_translation);
} catch (Throwable $e) {
echo "Caught error: " . $e->getMessage();
}
?>
Result: The application crashes or leaks detailed error information.
A subtler attack could expose private data if extra arguments are fed to sprintf(), especially when they are referenced by format specifiers (%2$s, %3$s, etc.).
Information Disclosure: If unintended arguments are printed via format specifiers.
- Privilege Escalation: Abuse of translation permissions to affect other modules/UI components.
How to Fix
This vulnerability was patched in commit abd77392, released in version 1.1.2 of the admin-ui-classic-bundle.
Or, apply the patch manually if you cannot upgrade immediately.
*Official advisory:* GitHub Security Advisory GHSA-3h7c-g527-xpwq
How to Patch (Manually)
The patch changes renderer logic to ensure translation values are treated as literals.
Original
echo sprintf($translationString, $someValue);
Patched
echo $translationString; // Direct, no sprintf
Or, if variables are intended, ensure all translations are sanitized, or better yet, avoid passing user-controlled input to sprintf().
Conclusion
If you’re running Pimcore with the admin-ui-classic-bundle, especially in a multi-user environment, update immediately to avoid exploitation. Always treat translation strings as potential attack surfaces, especially if users with low privileges can edit them.
References and Further Reading
- GitHub Advisory: GHSA-3h7c-g527-xpwq
- Pimcore admin-ui-classic-bundle Changelog
- Patch commit abd77392
- About translation attacks in PHP
Timeline
Published on: 09/25/2023 19:15:10 UTC
Last modified on: 09/26/2023 15:57:45 UTC