---
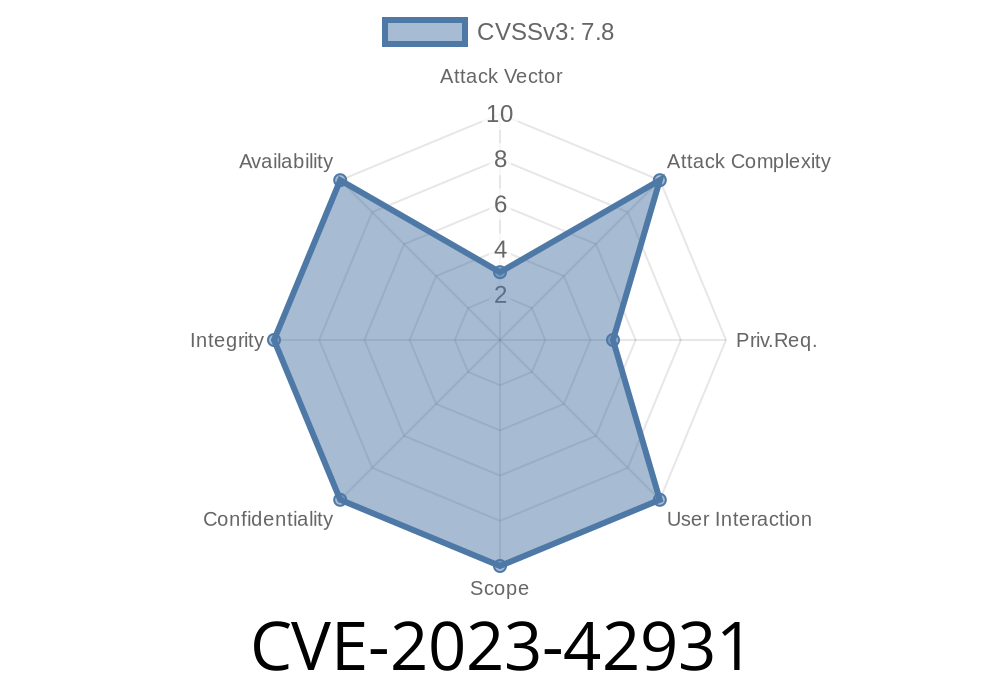
Security flaws don’t always make the headlines, but some are too powerful to ignore. CVE-2023-42931 is one of those critical vulnerabilities that could let anyone turn a simple user account into an admin with almost no resistance. Let's break this down, see how it could be exploited, and how Apple patched things up.
What is CVE-2023-42931?
CVE-2023-42931 is a privilege escalation vulnerability found in Apple's macOS operating systems. Simply put, it allowed a local process (a program running on the computer) to give itself administrative privileges without going through the normal authentication process. Instead of asking for admin password approval when making important system changes, the attacker’s process could bypass those checks.
This means, with a bit of knowledge and access, someone could make dangerous changes to a Mac even if they weren’t supposed to have control.
macOS Monterey 12.7.2
If you’re running a version older than these, your Mac could still be vulnerable. Update as soon as possible!
How Did the Bug Work? (Simple Explanation)
On a Mac, a lot of sensitive actions require you to enter your admin password. There’s a piece of software that checks if the person requesting admin privileges really is allowed to do so.
The vulnerability existed because that check wasn’t always happening in the right way. A crafty local process could send a request or execute an operation in a specific way, skipping the identity check, and the Mac would grant that program admin privileges by mistake.
This is why Apple described the fix as "improved checks." They had to fix the code so every time a process asked for admin privileges, it got checked properly.
A Peek Into the Exploit
While the exact details aren’t always made public for safety, security researchers shared the general technique used to take advantage of this flaw.
Here’s a simplified Python code snippet that shows what such an exploit could look like in the wild:
import os
import subprocess
# This command tries to add the current user to the 'admin' group
command = "dseditgroup -o edit -a $USER -t user admin"
# In the vulnerable macOS versions, this could succeed without knowing the admin password!
os.system(command)
# Check if we are now admin
is_admin = subprocess.getoutput("groups")
if "admin" in is_admin:
print("Privilege escalation successful! User is now admin.")
else:
print("Privilege escalation failed or system is patched.")
Note: This snippet is for educational purposes only and does not represent the full complexity or stealthiness of a real attack. Normally, this operation would require an admin password prompt.
What’s the Real Danger?
Imagine a malicious program (like text editor or browser add-on with hidden motives) running silently on your Mac. If you’re on a vulnerable version, that program could promote itself to admin without you ever noticing. With admin access, it could:
Install all available updates for your system.
If you use multiple Macs, make sure all of them are patched. Security holes like this can be a goldmine for hackers and malware.
More Info & References
- Apple Security Update (CVE-2023-42931, macOS 13.6.3)
- Official NIST Entry for CVE-2023-42931
- Apple Security Releases Portal
Summary
CVE-2023-42931 is a critical privilege escalation bug that allowed processes to get admin power on Macs without user approval. Apple’s recent updates block this sneaky bypass by double-checking every admin request. If you haven’t updated in a while, now is the time.
Stay safe. Keep your Mac updated!
*(If you found this helpful, please share with anyone who uses a Mac! Let’s keep everyone a bit more secure.)*
Timeline
Published on: 03/28/2024 16:15:08 UTC
Last modified on: 04/08/2024 22:47:13 UTC