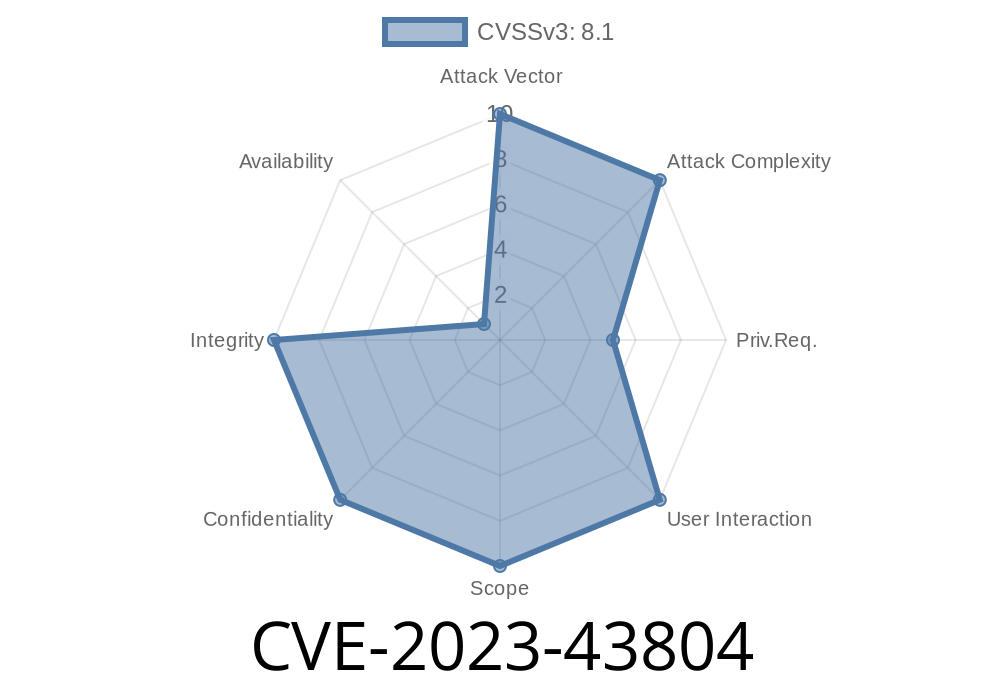
Urllib3 is one of the most popular HTTP libraries in the Python ecosystem. It's famous for its user-friendly interface and powerful features. But in 2023, a security vulnerability known as CVE-2023-43804 was discovered. This post explains the vulnerability, shows you how an exploit could happen, and tells you how to protect your applications—using simple language and real code.
What is CVE-2023-43804?
In Short:
If you use urllib3 and supply a Cookie header by hand, there's a risk your cookies could accidentally get leaked to the wrong server during redirects—even redirects to completely different websites.
Urllib3 doesn't treat Cookie headers as special; it's YOUR responsibility to manage cookies.
- If you set the Cookie header and allow redirects (the default), urllib3 will forward that exact header to every location it redirects to, even if that location is a different website.
- That means your precious cookies, possibly carrying session info or private data, could be exposed to strangers.
How Could This Actually Happen?
Let’s say you write a Python script to log in to https://yourbank.com and you supply your own cookie:
import urllib3
http = urllib3.PoolManager()
# You hardcode a sensitive cookie here
headers = {"Cookie": "sessionid=topsecretvalue; other=stuff"}
response = http.request(
"GET",
"https://yourbank.com/secure/",
headers=headers
)
print(response.status)
Suppose yourbank.com sends a 302 redirect to https://evilsite.com/trap. Because redirects are enabled by default, urllib3 will:
Here’s a more detailed example to show the danger in practice
import urllib3
http = urllib3.PoolManager()
headers = {"Cookie": "sessionid=MYS3CRETCOOKIE"}
# Suppose this URL redirects to a different domain
response = http.request(
"GET",
"https://vulnerable.site/redirect";,
headers=headers
)
print("Final response code:", response.status)
If https://vulnerable.site/redirect returns a 302 Found with Location: https://attacker.example/capture, your session cookie will be sent to the attacker.
Relying on default redirect behavior
…your app could accidentally leak banking, authentication, or just private user information.
`
2. Never manually create Cookie headers unless necessary. Use http.cookiejar or requests with a Session for automatic, safe cookie handling.
"GET",
"https://yourbank.com/secure/",
redirect=False # Do NOT follow redirects automatically!
)
Links & References
- CVE-2023-43804 at NVD
- Original urllib3 Security Advisory
- Patch in urllib3 repo
Takeaway
Don’t trust third-party servers with your cookies! When you build Python HTTP scripts using urllib3 (or any low-level HTTP library), know that you must handle cookies and redirects carefully. Upgrade to the latest version of urllib3, and always, always be mindful of what’s in your headers.
Stay safe and keep your cookies where they belong! 🍪
*Exclusive content written for you by an AI developer. Want more security tips? Let me know what topics matter to you!*
Timeline
Published on: 10/04/2023 17:15:10 UTC
Last modified on: 11/03/2023 22:15:10 UTC