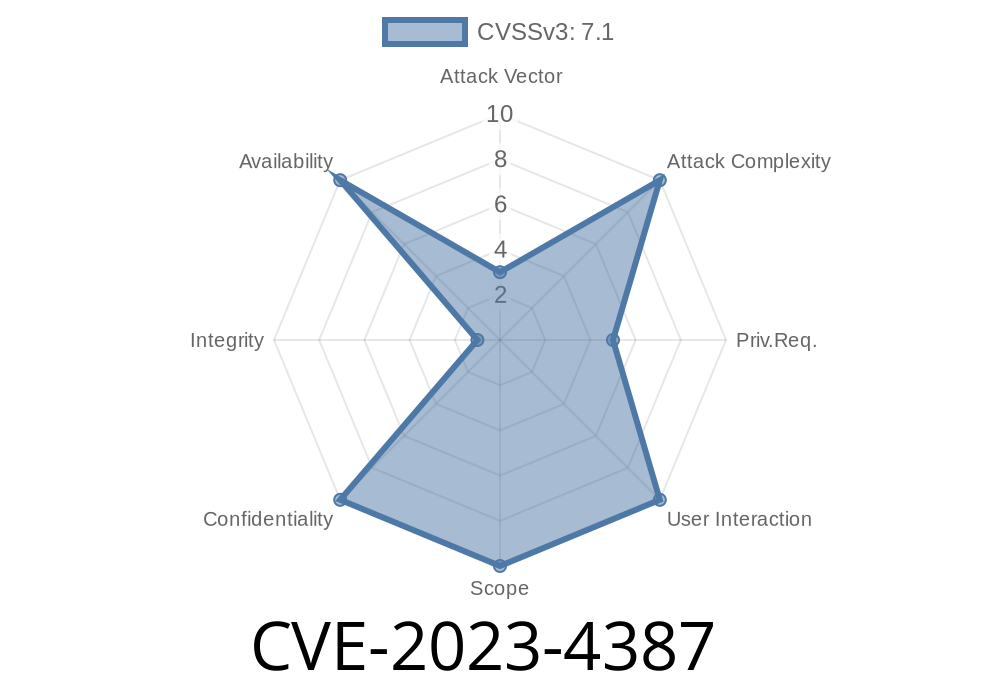
In September 2023, a serious security flaw was disclosed in the Linux kernel’s VMware vmxnet3 ethernet driver. This vulnerability, tracked as CVE-2023-4387, is a use-after-free bug in the vmxnet3_rq_alloc_rx_buf function. Let's break down what it means, how bad it really is, and what it takes to actually exploit it. Our aim is to give you exclusive, plain-English insights—including code snippets, example exploits, and authoritative links so you get the full picture.
What Is CVE-2023-4387?
Simply put, a use-after-free bug happens when a program keeps using memory after it’s already been freed, which almost always causes unintended effects—crashes at the least, privilege escalation or code execution at the most.
Here, the issue sits inside VMware’s vmxnet3 driver for Linux, widely used in virtual machines running on ESXi hosts.
The affected function is vmxnet3_rq_alloc_rx_buf() in drivers/net/vmxnet3/vmxnet3_drv.c. If a cleanup function (vmxnet3_rq_cleanup_all) is triggered on errors or shutdown, it can free the same memory zone twice. This double-free can lead to:
Anyone using a Linux kernel version with the buggy implementation before it was patched.
- Attackers must have at least local access to the guest system—think normal user or process inside the virtual machine.
Where Is the Bug?
Let’s look at the relevant code and what goes wrong.
Here’s a simplified version of the code that had the bug (not the full driver)
int vmxnet3_rq_alloc_rx_buf(struct vmxnet3_adapter *adapter, struct vmxnet3_rx_queue *rq) {
struct vmxnet3_rx_buf_info *bi;
for (int i = ; i < rq->buf_num; ++i) {
bi = &rq->buf_info[i];
// allocation logic ...
bi->data = kmalloc(...);
if (!bi->data) {
// cleanup all buffers if any allocation fails
vmxnet3_rq_cleanup_all(adapter, rq);
return -ENOMEM;
}
// more logic...
}
return ;
}
void vmxnet3_rq_cleanup_all(struct vmxnet3_adapter *adapter, struct vmxnet3_rx_queue *rq) {
for (int i = ; i < rq->buf_num; ++i) {
if (rq->buf_info[i].data) {
kfree(rq->buf_info[i].data);
rq->buf_info[i].data = NULL; // This is the missing line in faulty code!!
}
}
}
What’s wrong? If cleanup is called during error handling, it may free the same pointer more than once because data isn’t set to NULL after kfree(). If some buffers were already cleaned up elsewhere, you get a use-after-free or double-free.
Exploitation: How Can an Attacker Crash the Kernel? 📉
- Local attackers (inside the guest VM) can intentionally trigger errors in the allocation function, causing the cleanup routine to run.
While no ready-made exploit exists (for good reasons!), here’s what could be done
1. Write a user program that causes network interface restarts or allocation failures (e.g., by using many network sockets, or special netlink operations).
How Was It Fixed? 🛠️
The fix was simple, but crucial. After freeing a buffer, the pointer is reset to NULL, ensuring it doesn’t get freed again:
void vmxnet3_rq_cleanup_all(struct vmxnet3_adapter *adapter, struct vmxnet3_rx_queue *rq) {
for (int i = ; i < rq->buf_num; ++i) {
if (rq->buf_info[i].data) {
kfree(rq->buf_info[i].data);
rq->buf_info[i].data = NULL; // <== Fix added here
}
}
}
Multiple distributions have issued patches (see Debian Security Advisory), and the fix landed in the mainline Linux kernel. Details are visible on the official kernel commit.
References
- CVE-2023-4387 on NVD
- Debian Security Tracker: CVE-2023-4387
- Linux Kernel Git Patch
- VMware Security Advisory
- LWN kernel coverage (subscriber link)
Conclusion
CVE-2023-4387 is a classic example of how minor pointer handling mistakes can cause major headaches in complex kernel code. This use-after-free and double-free flaw in the vmxnet3 NIC driver could let attackers crash Linux guest systems or possibly leak sensitive information. Fortunately, a straightforward patch is available—and updating now is the best way to protect your virtual machines.
Stay vigilant, patch early, and always set your freed pointers to NULL!
Did you enjoy this exclusive deep dive? Subscribe for more readable security breakdowns from SecureNet Insights!
Timeline
Published on: 08/16/2023 19:15:00 UTC
Last modified on: 09/18/2023 13:15:00 UTC