---
Introduction
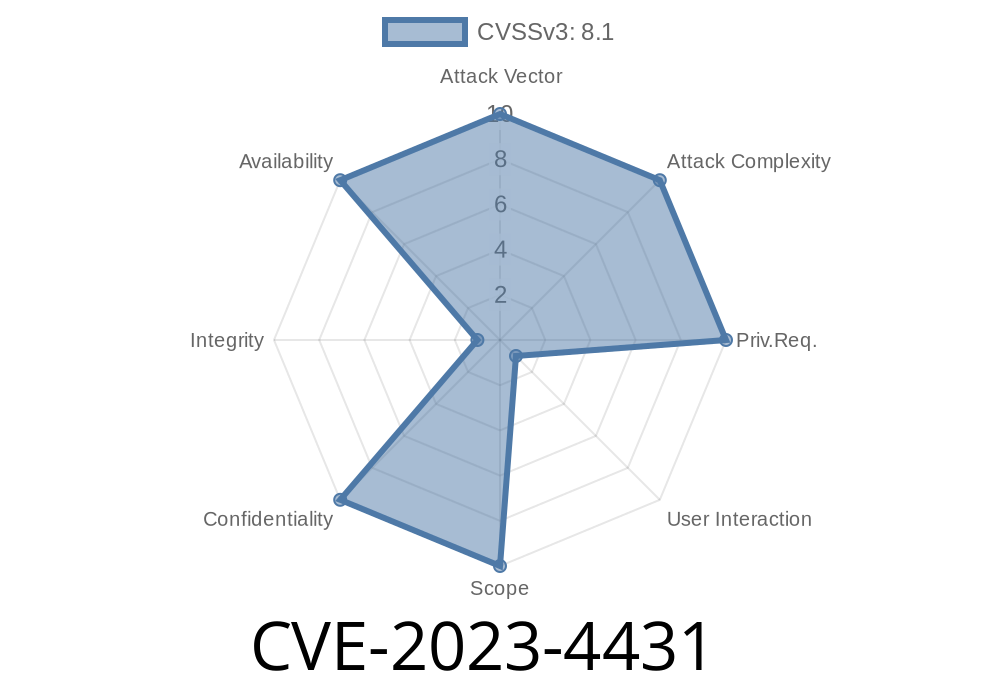
In the tech world, security is always a moving target. In August 2023, a medium-severity security bug dubbed CVE-2023-4431 was uncovered in Google Chrome. It affected how Chrome processes fonts in web pages. Let’s break down what happened, how it works, and what it means for anyone using Chrome.
What Is CVE-2023-4431?
CVE-2023-4431 stands for "Common Vulnerabilities and Exposures" number 2023-4431. It was a bug found in the way Google Chrome handled certain web fonts before version 116..5845.110.
Component affected: Fonts
- Impact: Allowed attackers to read parts of the browser's memory by making you visit a malicious HTML page
The Problem with Fonts
Chrome lets web pages display custom fonts. This involves reading, decoding, and rendering font files. If these steps aren’t checked properly, a webpage can trick Chrome into reading memory outside the font’s allocated data—this is called out-of-bounds memory access.
When someone visits the page in a vulnerable version of Chrome, the browser processes the font.
3. Code in Chrome tries to read font data, but due to missing checks, it accidentally reads past the end of the allowed memory.
The Technical Details
Chromium’s Patch:
Chromium Commit: Out-of-bounds memory access in Fonts
The vulnerable code was somewhere along these lines (simplified for clarity)
// Vulnerable pattern (not actual Chrome code)
uint16_t glyphCount = ReadUInt16(fontData + offset);
Glyph* glyphs = (Glyph*)(fontData + offset + 2);
for (int i = ; i < glyphCount; i++) {
// If glyphCount is too big, this will go beyond the buffer.
ProcessGlyph(glyphs[i]);
}
It then loops through that number, processing each "glyph" (shape).
- If the font says it has 100 glyphs but only provides data for 10, the loop will read random memory after the font data, outside of what’s safe.
The patch added a check to make sure glyphCount isn’t larger than the data actually available
// Patch (simplified)
if (glyphCount > expectedGlyphsInBuffer) {
// Error: don't process
return;
}
Proof-of-Concept Exploit
Here’s a simplified example of how an attacker might craft a webpage (the real exploit code is more complex and depends on knowledge of font file structures):
<!-- Exploit HTML (theory, for educational purposes) -->
<!DOCTYPE html>
<html>
<head>
<style>
@font-face {
font-family: 'BadFont';
src: url('malformed-font.woff2'); /* A font with manipulated glyph counts */
}
.test-text {
font-family: 'BadFont', sans-serif;
font-size: 24px;
}
</style>
</head>
<body>
<div class="test-text">
Exploiting Chrome's font memory!
</div>
</body>
</html>
The malformed-font.woff2 would contain a header that claims a huge number of glyphs, tricking Chrome into reading too far into memory when drawing the text.
Protecting Yourself
- Update Chrome: Always use the latest version. This bug was fixed in Chrome 116..5845.110 and later.
Don’t ignore browser updates: Chrome's auto-update matters.
- Watch out for new font files: Avoid shady sites, as many browser bugs are triggered by opening weird web pages.
References
- Chromium Security Advisory
- CVE Details Page - CVE-2023-4431
- Chromium Commit Fix
- Project Zero: Exploiting Browser Memory Bugs - General Reading
Conclusion
CVE-2023-4431 shows how web browsers are always at risk from even everyday features like fonts. Attackers look for any gap—no matter how small—to get information or cause crashes. The best way to stay safe is simple: keep your browser up to date.
Share this with anyone you know who might not update their Chrome regularly—because even fonts can be dangerous!
Timeline
Published on: 08/23/2023 00:15:00 UTC
Last modified on: 08/25/2023 13:19:00 UTC