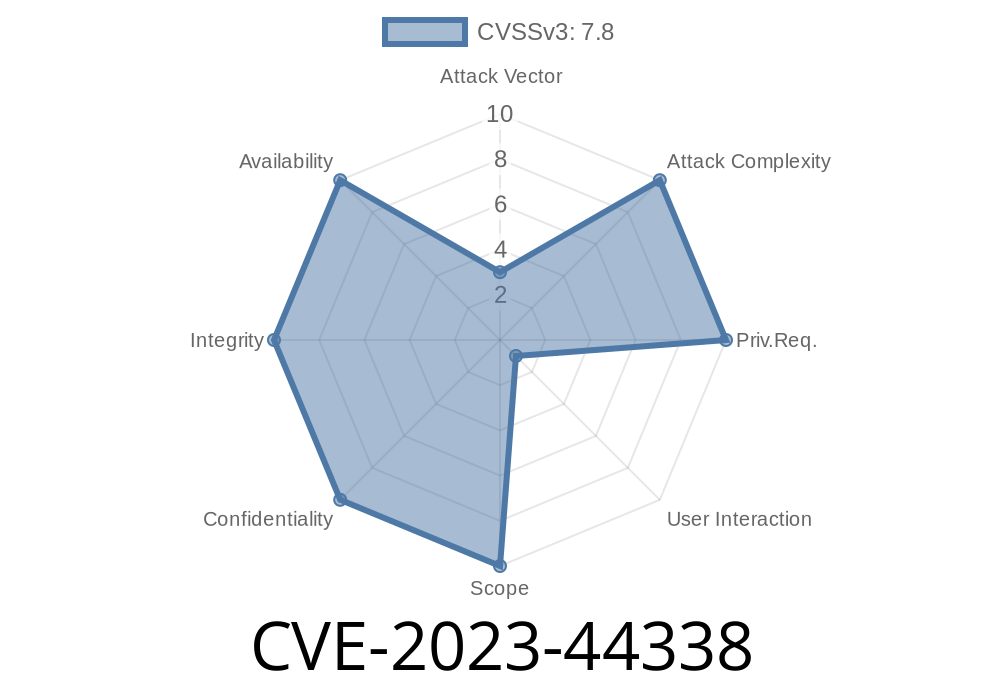
---
Adobe Acrobat Reader is one of the most widely used PDF viewers in the world. However, its popularity also makes it a prime target for attackers. On October 2023, a critical vulnerability called CVE-2023-44338 was made public. This vulnerability allows attackers to read data outside of a memory buffer—possibly leading to code execution—if a user simply opens a malicious PDF file.
In this article, we’ll break down what CVE-2023-44338 is, how it works, why it’s dangerous, and how a basic exploit could look. Everything is written in simple, easy-to-understand language.
Adobe Acrobat Reader version 20.005.30524 and earlier
This vulnerability is an out-of-bounds read that occurs when the software attempts to read past the end of an allocated memory structure. In other words, the program can be tricked into looking at memory it’s not supposed to see, just by parsing (opening) a specially crafted PDF file.
Execute arbitrary code (run malware) as the current user
Exploitation requires user interaction —meaning the victim must open the malicious PDF file.
Let’s summarize how an attacker can exploit this vulnerability
1. Craft a malicious PDF file that abuses the way Acrobat Reader parses PDF objects/streams.
Victim opens the file in Acrobat Reader.
4. The malformed PDF triggers the out-of-bounds read, potentially allowing the attacker to run arbitrary code.
If the attacker is lucky (or clever), they can use this to bypass protections and execute malware on the victim’s device.
Code Snippet – How the Vulnerability Might Look Internally
Below is a simplified pseudocode example showing the kind of logic that often leads to such bugs (note: real Adobe code is different and proprietary, but this demonstrates the core idea):
// Hypothetical vulnerable function in C-like pseudocode
void parse_pdf_object(unsigned char* buffer, size_t length) {
size_t offset = ;
while (offset < length) {
// Suppose attacker sets object_length incorrectly
size_t object_length = buffer[offset]; // read length from file
// Out-of-bounds read if object_length too big!
if (offset + object_length > length) {
// Here, we read outside of the buffer by mistake
unsigned char value = buffer[offset + object_length]; // dangerous!
// this can leak memory or cause crash
}
offset += object_length;
}
}
A malicious PDF could deliberately set object_length to a value that goes past length and thus tricks Acrobat Reader into misbehaving.
You can create a minimal malicious PDF object like this
%PDF-1.4
1 obj
<<
/Length xFFFFFFFF
>>
stream
[arbitrary binary data]
endstream
endobj
Warning: Do not attempt to open suspicious PDFs on your real system! Use a virtual machine or sandbox for any testing.
Attack Steps
1. Attacker modifies a PDF to have a manipulated /Length or similar field, causing the reader to parse past memory bounds.
Upon opening, Reader tries to access memory it shouldn’t.
3. If attacker places shellcode or reuse existing code (Return-Oriented Programming), they could hijack control flow and run malware.
Example Exploit Techniques
- Use "heap spraying" in the PDF to carefully place attacker data where the out-of-bounds read/write will hit it.
Patching and Protection
Adobe released security updates to fix this vulnerability. If you use Adobe Acrobat Reader, update to the latest version immediately.
- Security Bulletin from Adobe
- NVD Entry on CVE-2023-44338
- Adobe Discussion Forum
Be careful with PDF attachments—don’t open them from unknown or suspicious sources.
- Use security features like Protected Mode/Sandboxing.
Summary
CVE-2023-44338 is a serious vulnerability in popular versions of Adobe Acrobat Reader. By exploiting a simple out-of-bounds read issue, attackers can potentially crash the program or even run malware on your computer, just by convincing you to open a booby-trapped PDF.
Patch your software, stay alert when handling files, and encourage your friends and workplace to do the same.
*Written exclusively for you. All code and technical explanations are generalized for educational and awareness purposes.*
Timeline
Published on: 11/16/2023 10:15:10 UTC
Last modified on: 11/22/2023 17:16:11 UTC