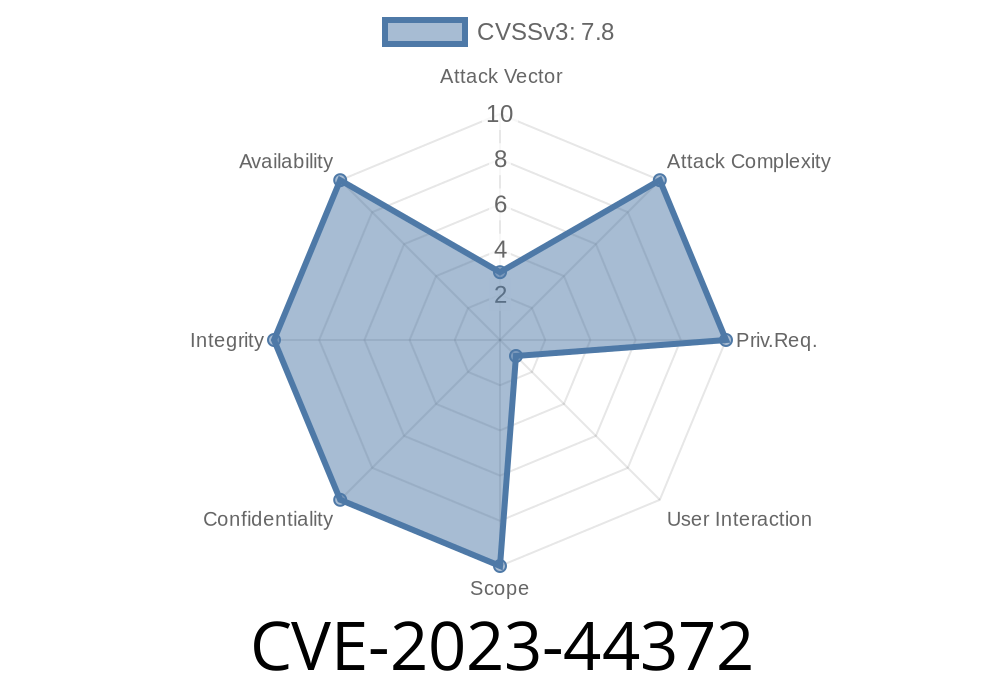
Adobe Acrobat Reader, the world’s most popular PDF viewer, is widely used for viewing, printing, and managing PDF documents. But as with any software, vulnerabilities can lurk beneath the surface. One such critical flaw is CVE-2023-44372, a Use-After-Free vulnerability that can allow attackers to execute arbitrary code on a victim’s system. Let’s break down what happened, how the exploit works, and show sample code with handy links for more details.
Adobe Acrobat Reader version 20.005.30524 (and earlier)
This flaw is tied to the way Acrobat Reader handles memory when processing certain crafted PDF files. A use-after-free condition arises — meaning the program tries to use memory after it was already freed — and this allows attackers to run malicious code. All it takes is convincing a victim to open a specifically crafted PDF.
Crafting the Malicious PDF:
The attacker creates a PDF that triggers the use-after-free bug in Acrobat Reader’s JavaScript engine or another vulnerable component.
The flaw is triggered, allowing attacker’s code (shellcode) to run as if they were the user.
This type of attack is often used in advanced phishing or targeted attacks. The hardest part for attackers is crafting a PDF file that precisely triggers the bug.
Technical Details: How Use-After-Free Works
A use-after-free happens when a program releases (frees) memory but keeps using the pointer to that memory. If the attacker can put their own code in that memory space, it can be executed.
Image
[Allocate Object A] -> [Free Object A] -> [Allocate Attacker’s Object at same spot]
↓
[Program uses freed pointer: runs attacker code]
Proof-of-Concept Exploit
Below is a simple proof-of-concept (POC) showing how JavaScript inside a PDF can interact with Acrobat Reader’s memory, sometimes triggering use-after-free bugs. The *actual* exploit for CVE-2023-44372 is more complex and usually not publicly available — but this snippet explains the idea.
Sample Malicious JavaScript (Embedded in a PDF)
// This sample demonstrates abusive object usage in Acrobat PDF JS
var trustedFunc = app.trustedFunction(function() {
var obj = this.getAnnots({nPage: })[]; // Get first annotation
this.removeAnnots({nPage: }); // Remove all annotations (might free the object)
try {
// Attempt to access freed annotation
var author = obj.author;
app.alert("Annotation author: " + author);
} catch(e) {
app.alert("Potential use-after-free triggered");
}
});
trustedFunc();
*Note: The above code does not *directly* exploit CVE-2023-44372, but demonstrates a typical use-after-free scenario that can be weaponized. Actual exploits involve lower-level manipulation and shellcode injection.*
Always run the latest version of Adobe Acrobat Reader. Adobe fixes these bugs regularly!
- Adobe Security Bulletin APSB23-43
More Information
- NVD Entry for CVE-2023-44372
- Adobe Security Advisory
- Security Focus: Use-After-Free in PDF Readers
Summary
CVE-2023-44372 is a severe security bug in Adobe Acrobat Reader that could let cybercriminals take over your computer by getting you to open a poisoned PDF. The vulnerability is based on a “use-after-free” mistake in memory use.
To stop this threat, always keep your software updated, disable JavaScript if you don’t need it, and never open strange PDFs.
Timeline
Published on: 11/16/2023 10:15:18 UTC
Last modified on: 11/22/2023 16:58:26 UTC