TL;DR
CVE-2023-44384 is a critical security vulnerability in the _discourse-jira_ plugin that could let attackers abuse admin or moderation features to perform SSRF (Server-Side Request Forgery) and unauthorized API requests with elevated Jira permissions. In this post, you'll learn how the exploit works, see code snippets, review mitigation steps, and get direct reference links.
What is Discourse-Jira?
Discourse is a popular forum platform. discourse-jira is an official plugin that syncs Jira issues, project info, and fields automatically, so teams can link forum topics to Jira tasks. The integration typically needs a Jira admin to set up Jira API credentials in the plugin settings.
Vulnerability Overview
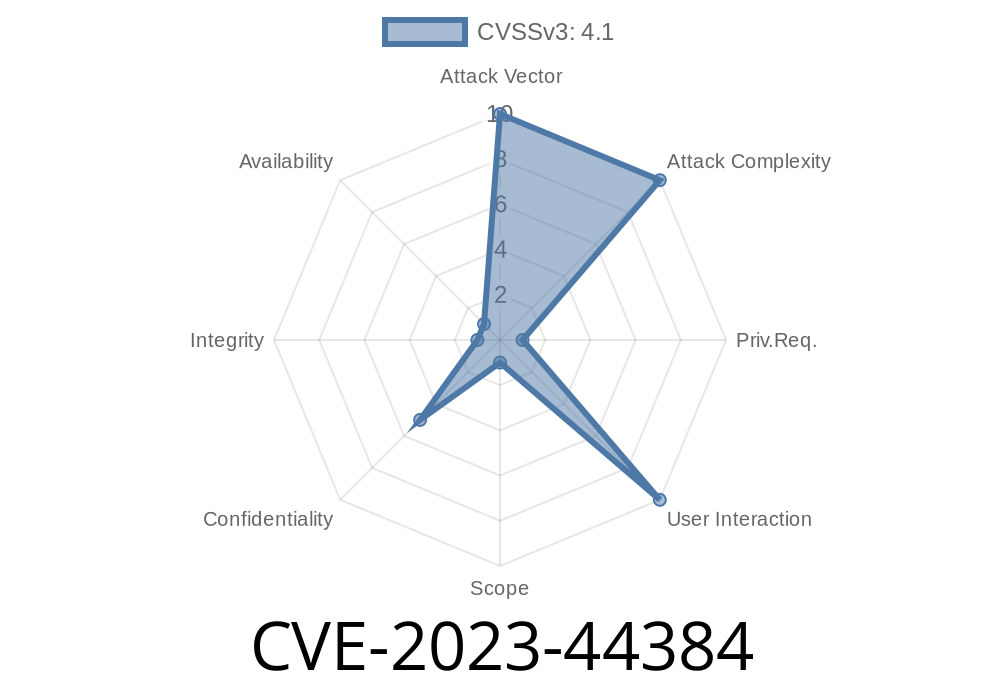
The CVE report is here:
- NVD - CVE-2023-44384 entry
- Github Advisory
Admin SSRF:
Any admin could change the Jira URL in the plugin settings to an address they control (even an internal AWS metadata endpoint or localhost). Once the verbose log setting is enabled, Discourse would try to fetch data from _any_ address, leak responses, and save results.
Moderator Privilege Escalation:
Moderators (not just admins!) could tamper with the path used by the plugin's backend to talk to Jira. Because the backend was using _Jira application credentials_, GET requests to arbitrary API endpoints became possible—including potentially sensitive Jira APIs, or even outside hosts if the Jira server accepted strange paths.
Let's say you're an admin. In the Admin > Plugins > Jira settings
- Jira URL: Change this from https://yourcompany.atlassian.net to http://169.254.169.254/latest/meta-data/
Turn on discourse_jira_verbose_log
- The plugin tries to sync with "Jira", which now is actually the cloud VM’s internal metadata endpoint.
Code Location:
In older versions, code that handled sync fetches directly consumed the user-given URL variable
# File: plugins/discourse-jira/lib/jira.rb (simplified pseudocode)
class JiraClient
def initialize(base_url)
@url = base_url # no URL validation!
end
def fetch_projects
# If @url = http://169.254.169.254, we hit it!
resp = HTTParty.get("#{@url}/rest/api/2/project", ...)
# If verbose log enabled, log the raw response (potential credential leakage)
Rails.logger.info(resp.body) if SiteSetting.discourse_jira_verbose_log
end
end
Outcome:
The server makes requests to _whatever address the admin sets_, and verbose log may leak response bodies.
2. Moderator Path Manipulation (Privilege Escalation)
Normally only safe, whitelisted Jira API paths are requested by the plugin, but due to weak validation, a moderator can make requests like:
GET /plugins/discourse-jira/api/proxy?path=/%2e%2e/%2e%2e/%2e%2e/etc/passwd
Or go after sensitive Jira endpoints they shouldn’t access
GET /plugins/discourse-jira/api/proxy?path=/rest/api/2/user/search?username=admin
Since the proxy layer uses Application credentials for Jira, the moderator can get much more than their own Jira account allows.
Vulnerable snippet (simplified pseudocode)
# File: plugins/discourse-jira/controllers/api_controller.rb
def proxy
path = params[:path] # no or poor sanitization
jira_url = SiteSetting.jira_url
credential = SiteSetting.jira_api_key
resp = HTTParty.get("#{jira_url}#{path}", headers: auth_headers(credential))
render json: resp.body
end
Attackers as Admins:
Can make requests _anywhere_ from the Discourse host, stealing inner network data, or cloud credentials, or triggering other webhooks or apps.
Moderators (Lower Privilege):
Can use your Jira API credentials for unauthorized reconnaissance or data theft, possibly downloading sensitive corporate data or personal information.
Patch example (simplified)
def proxy
path = params[:path]
# Only allow certain paths!
unless ALLOWED_PATHS.include?(path)
render status: 403, json: { error: 'Invalid API path' }
return
end
... # make safe request
end
See the fix:
Discourse sites running discourse-jira (any version before the fix).
- Hosts with admins or moderators you don't 100% trust. Either group could potentially escalate this!
How to Protect Your Forum
1. Upgrade the plugin to at least version .2.1.
References
- CVE-2023-44384 at NVD
- GitHub Security Advisory for discourse-jira
- Discourse-Jira GitHub plugin
- Original PR fixing vulnerability
- SSRF Explainer
Summary
CVE-2023-44384 exposed Discourse forums to SSRF and credential leakage due to insecure handling of external requests in the Jira plugin. Both admins and moderators could elevate privileges or make sensitive requests with backend Jira API credentials. Upgrade your plugin now, and remember: never trust user-configured URLs without proper validation.
Timeline
Published on: 10/06/2023 18:15:12 UTC
Last modified on: 10/11/2023 17:49:49 UTC