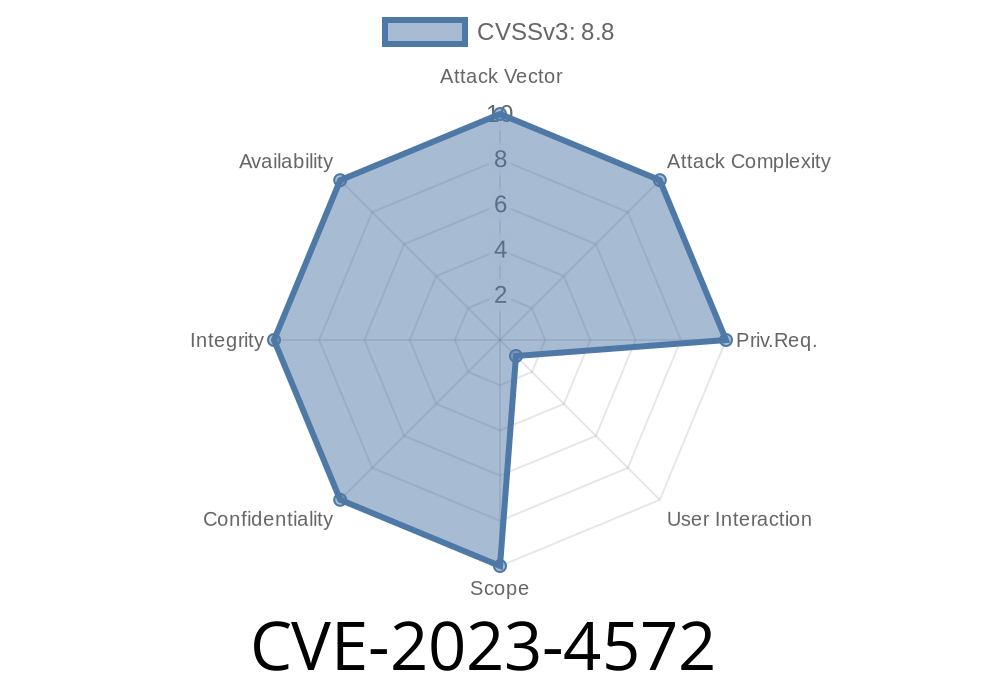
---
In August 2023, Google addressed a serious "use after free" vulnerability in the MediaStream component of Google Chrome, tracked as CVE-2023-4572. Before version 116..5845.140, attackers could remotely exploit Chrome via a specially crafted HTML page. This critical flaw posed a big threat, allowing potential heap corruption with high security risks. Today, let's go step-by-step through what this vulnerability is, how it works, and outline (for educational purposes) what an exploit might look like.
What is a "Use After Free" Bug?
A "use after free" (UAF) bug happens when a program continues to use a piece of memory after it has been freed (released). This can open the door to heap corruption or arbitrary code execution, since the memory could have been re-allocated for another purpose, or worse, crafted by an attacker.
Where Did the Bug Live?
The culprit was Chrome's MediaStream feature, which lets websites capture and process video & audio streams (like webcam and mic access). The bug was rooted in how Chrome handles certain MediaStream objects, leaving them dangling after they had been released.
Exploitation Scenario
A remote attacker could lure a Chrome user to visit a malicious HTML page containing JavaScript code. This code would manipulate MediaStream objects, triggering the use-after-free condition, and potentially allow for heap data corruption. In specific cases, attackers could gain further privileges or even execute arbitrary code.
Code Snippet: How an Attack May Look
Below is a simplified (sanitized) pseudocode representation inspired by public write-ups and bug tracker information:
// WARNING: DO NOT use for attack—educational ONLY
// Create a video element
let video = document.createElement('video');
// Get access to user's camera (user will be prompted)
navigator.mediaDevices.getUserMedia({ video: true })
.then(stream => {
video.srcObject = stream;
// Attach event
video.onloadedmetadata = () => {
// Repeatedly detach and attach the MediaStream
for (let i = ; i < 100; i++) {
video.srcObject = null;
video.srcObject = stream;
}
// Force garbage collection (in some environments)
if (window.gc) window.gc();
};
document.body.appendChild(video);
});
How does this relate to the bug?
By quickly switching srcObject between null and the same stream, it causes a race where the MediaStream object gets freed but is still used internally, potentially leading to a use-after-free scenario.
Exploit Details (at a High Level)
1. Trigger the Vulnerability: The exploit rapidly attaches/detaches MediaStream objects to a <video> element.
2. Heap Corruption: If the MediaStream object is freed but still referenced, the browser could access invalid memory.
3. Potential Payload Execution: With heap manipulation, a skilled attacker may craft memory layouts that result in code execution or a crash.
*Note*: Real-world exploitation may require bypassing Chrome’s sandbox and memory protections like PartitionAlloc.
Real-World Consequence
This bug was given a "High" severity rating by the Chromium Project due to:
Reported: August 2023
- Patched: Chrome 116..5845.140
- Public Disclosure: Via Google's Release Blog, with proper attribution to the security researcher who found it.
If you're running a Chrome version prior to 116..5845.140, it's critical to update now.
References & Credits
- NIST CVE-2023-4572 detail
- Chromium Security Blog
- Patch Commit in Chromium
- MediaStream API, MDN
- Common 'Use After Free' Explained
Conclusion
CVE-2023-4572 is a prime example of how a seemingly small bug in a browser’s media handling can have big security consequences. The best defense? Keep Chrome up-to-date and stay alert for security advisories. Understanding these vulnerabilities helps us build safer software and surf smarter.
Timeline
Published on: 08/29/2023 20:15:00 UTC
Last modified on: 09/01/2023 04:15:00 UTC